In this article, we will tell the best way to find the last logon time for the AD domain client and discover accounts that have been inactive for over 90 days.
How to Get a User’s Last Logon Time Using ADUC?
You can discover the last logon time for the space client with the ADUC graphical control center (Active Directory Users and Computers).
1-Run the control center dsa.msc;
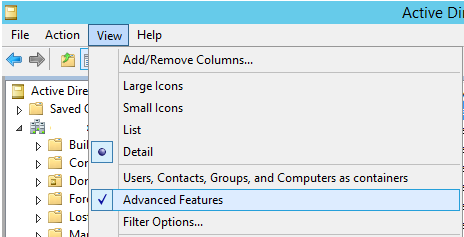
2- In the top menu, enable the choice View > Advanced Features;
3- Discover the client in the AD tree and open its properties;
4- Snap-on the tab Attribute Editor;
5- In the rundown of qualities, discover lastLogon. This quality contains the time the client was last signed in the space
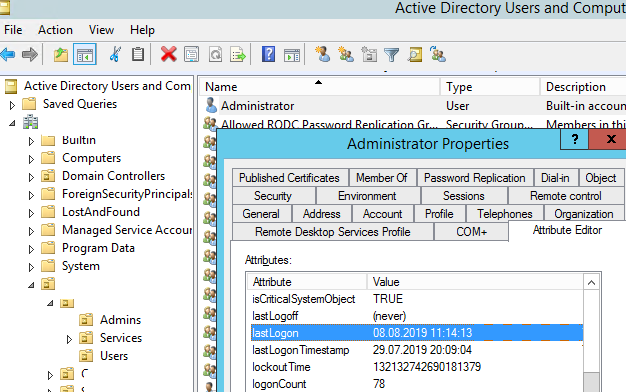
Note. You will have two similar attributes on the screenshot above — lastLogon and lastLogonTimestamp. What’s the difference between them?
lastLogon attribute is refreshed when the client signs on to the domain. Yet, it just changes on the domain regulator that confirmed the user, and isn’t repeated to other space regulators. Accordingly, in case there are numerous domain regulators at various AD destinations, you should check this characteristic on every one of them and afterward think about the subsequent information. The worth of this characteristic on various DCs for the client can be unique or even zero (if the client has never been validated on this DC);
lastLogonTimeStamp attribute is likewise changed when the client signs on to the area regulator and is repeated to different DCs. Be that as it may, replication of this attribute consumes a large chunk of the day (this characteristic is reproduced just if its worth is 14 days or more established than the past one). Consequently, the information in this trait on a particular DC may not be relevant.
Find last logon using CMD
You can discover the time the client last signed into the space from the COMMAND line utilizing the net or dsquery devices.
Open a COMMAND brief (you needn’t bother with area overseer advantages to get AD client data), and run the command:
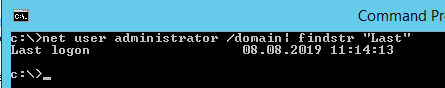
net user administrator /domain| findstr "Last"
You got the user’s last logon time: 08.08.2019 11:14:13.
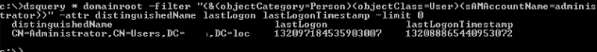
You can also get the last logon time using dsquery. For example:
dsquery * domainroot -filter "(&(objectCategory=Person)(objectClass=User)(sAMAccountName=administrator))" -attr distinguishedName lastLogon lastLogonTimestamp -limit 0
The primary issue is that the characteristics lastLogon and lastLogonTimestamp are put away in timestamp design in AD, and you need to moreover change it over to an ordinary time design.
You can also use this command to find all users who are inactive, for example, for 10 weeks:
dsquery user domainroot -inactive 10Find last Logon time using Powershell
You can likewise utilize PowerShell to get the client’s last area logon time. For this, you need to utilize the Active Directory module for Windows PowerShell. Introduce this module and import it into your PowerShell meeting:
Import-Module ActiveDirectory
To figure out the last logon time for the area director account, run the order:
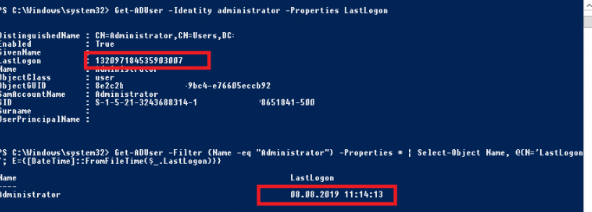
Get-ADUser -Identity administrator -Properties LastLogon
The cmdlet returned the time in Timestamp design. To change it over to a typical time, utilize the accompanying order:
Get-ADUser -Filter {Name -eq "administrator"} -Properties * | Select-Object Name, @{N='LastLogon'; E={[DateTime]::FromFileTime($_.LastLogon)}}
By PowerShell, you can show the last logon time for all enabled domain users:
Get-ADUser -filter {enabled -eq $true} -Properties * | Select-Object Name, @{N='LastLogon'; E={[DateTime]::FromFileTime($_.LastLogon)}}|Sort-Object LastLogon -Descending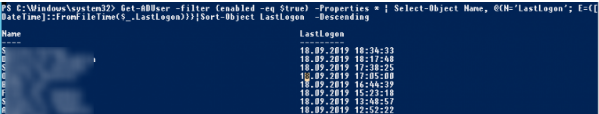
Or you can find users who are inactive for more than 90 days:
$date1= (Get-Date).AddDays(-90)
Get-ADUser -Properties LastLogonDate -Filter {LastLogonDate -lt $date1} | ftSubsequent to distinguishing inactive accounts, we suggest you disable those clients’ records, stand by half a month, and afterward erase the records if no issues have been accounted for. You can incapacitate dormant clients utilizing the Disable-ADAccount cmdlet:
Get-ADUser -Properties LastLogonDate -Filter {LastLogonDate -lt $date1} | Disable-ADAccount
Essentially, you can triumph when it’s all said and done the last logon time for PC objects in a domain. The accompanying command will list all PCs that have been latent for over 90 days:
Get-ADComputer -Properties LastLogonDate -Filter {LastLogonDate -lt $date1} | Sort LastLogonDate | FT Name, LastLogonDate -AutosizeClue. You can get the definite client logon history just from the security events logs of domain regulators.
Get Last Logon for User across All Domain Controllers
As we said before, if there are a few domain regulators in your domain, the lastlogon value on them might vary. In the event that a client has been inactive for over 14 days, the most effortless way is to get the value of the lastLogonTimeStamp property from any domain regulator. In any case, in the event that you don’t realize which site or DC the client was keep going validated on, you should inquiry all domain regulators in the AD to get the client’s last logon date.
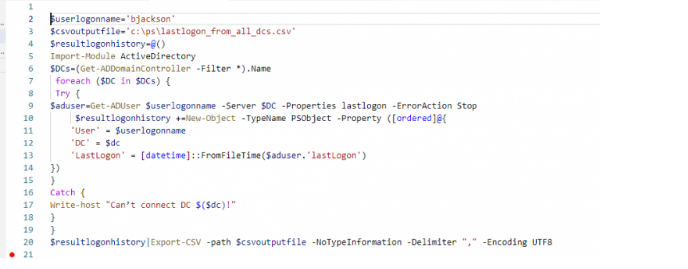
The below-mentioned PowerShell script loop through all domain regulators in the domain and gets the value of the lastLogonTime quality from every one of them. The outcome is traded to a CSV record:
$userlogonname='bjackson'
$csvoutputfile='c:\ps\lastlogon_from_all_dcs.csv'
$resultlogonhistory=@()
Import-Module ActiveDirectory
$DCs=(Get-ADDomainController -Filter *).Name
foreach ($DC in $DCs) {
Try {
$aduser=Get-ADUser $userlogonname -Server $DC -Properties lastlogon -ErrorAction Stop
$resultlogonhistory +=New-Object -TypeName PSObject -Property ([ordered]@{
'User' = $userlogonname
'DC' = $dc
'LastLogon' = [datetime]::FromFileTime($aduser.'lastLogon')
})
}
Catch {
Write-host "Can’t connect DC $($dc)!"
}
}
$resultlogonhistory|Export-CSV -path $csvoutputfile -NoTypeInformation -Delimiter "," -Encoding UTF8
If you want to find the maximum user LastLogon value quickly from all DCs, use the following:
[datetime]::FromFileTime((Get-ADDomainController -Filter * | foreach {Get-ADUser 'bjackson' -Properties LastLogon -Server $_.Name | select LastLogon} | Measure-Object -Property LastLogon -Maximum).Maximum)