Microsoft Active Directory provides 2 necessary services: authentication and authorization. As a part of the authentication method, Active Directory validates Associate in nursing identity before the user will access resources on the assembly network. There area unit many events happening in a lively Directory atmosphere. A number of the events may well be associated with unhealthy logon tries created by users and pc accounts. However, it becomes therefore tough to spot the amount of individuals WHO are causing unhealthy logon tries unless you utilize an automatic approach. This is often wherever this text comes handy. As a part of this text, we have a tendency to justify the way to use PowerShell commands and scripts to spot the users causing unhealthy logon tries in a lively Directory atmosphere and conjointly generate reports for distinctive the users causing unhealthy logon tries.
Why check for unhealthy logon tries in Active Directory?
It is imperative to know that a hacker would continuously decide to go surfing to a system or servers in an exceedingly production atmosphere employing a username and positive identification. The positive identification furnished the username is attested by Active Directory. If Active Directory isn’t able to manifest or if the positive identification doesn’t match with the positive identification hold on within the Active Directory info, the logon is rejected and Active Directory stores the “bad logon attempt” against that user in its info. There area unit 2 reasons why you’d want a nasty logon tries report:
If you’ve got thousands of staff in your organization, as a part of the cybersecurity assessment, it becomes necessary for you to drag out a report on the amount of unhealthy logon tries created by each user within the Active Directory atmosphere. The report would assist you learn unhealthy logon tries created by each user and therefore the “count” is extremely necessary here. If you see many users area unit causing too several unhealthy logon tries those users will return underneath the suspicious class.
It is on no account continuously the case that a user WHO seems to be inflicting a nasty logon try is truly the user himself. It can be Associate in Nursing application running on the user’s laptop that’s attempting to use the user’s credentials to manifest against the Active Directory, or somebody else attempting to impersonate that user.
Tip: If you may establish the rationale for unhealthy logon tries, you may save time work the cause for account lockouts.
Checking unhealthy logon tries for one user account:
If you’ve got put in Active Directory PowerShell modules, you’ve got Get-ADUser PowerShell cmdlet which may be accustomed check unhealthy logon tries sent by users. for instance, this PowerShell command is dead to see what percentage unhealthy logon tries were sent by the user:
Get-ADUser -Identity SamUser -Filter * -Properties BadLogonCount,CanonicalName
As you’ll see within the higher than command, we have a tendency to area unit checking BadLogonCount property to see the amount of unhealthy logon tries sent by the users. It’s necessary to know that a traditional user will send unhealthy logon tries thanks to the actual fact they could have forgotten or mistyped their positive identification, however too several tries can be thought-about as a suspicious activity. So, if you’re thinking that that a selected user account is playacting unauthorized activities, use the higher than command to see the unhealthy logon counts.
Checking unhealthy logon tries for all user accounts in Active Directory:
As a part of the cybersecurity assessment, one amongst the responsibilities of a lively Directory administrator is to see the amount of unhealthy logon counts for every user within the Active Directory. By now, understand the command that might be accustomed check the unhealthy logon counts as explicit within the previous section of this text, however doing it manually for all users would take a substantial quantity of your time. The PowerShell script below is accustomed collect unhealthy logon counts for all users in every Active Directory domain and generate a report. There area unit 2 reports generated by the script:
Summary report.
Report with username causing unhealthy logon counts.
Both reports area unit situated underneath C:\Temp directory.
Requirements to run the PowerShell script:
Before you’ll run the PowerShell script provided as a part of this text, make certain you meet these requirements:
You have put in Active Directory PowerShell modules on the pc from wherever you propose to run the script.
You have access to Active Directory domains. The script connects to all or any Active Directory domains and provides knowledge for every domain.
You have created a file referred to as C:\Temp\DomainList.DPC and such all domains to be checked as a part of the script.
Your account has permissions to access all domains within the current Active Directory forest.
What will the script do?
The PowerShell script performs the subsequent operations:
Checks all Active Directory domains laid out in the C:\Temp\DomainList.DPC file.
Imports Active Directory PowerShell modules into this PowerShell session.
Connects to every Active Directory domain victimization Get-ADUser and collects the user unhealthy logon counts.
Creates 2 files: C:\Temp\SummaryReport.CSV and C:\Temp\BadLogonAttemptsData_Data.CSV file.
Important: The script doesn’t write something to Active Directory domain controllers. The script simply executes Get-ADUser PowerShell cmdlet, that may be a read-only command, to assemble needed knowledge and supply the ends up in the CSV file.
The PowerShell script:
$TestCSVFile ="C:\Temp\SummaryReport.CSV"
Remove-Item $TestCSVFile
$UniqueTest = “BadLogonAttemptsData”
$CurrentLoc=”C:\Temp”
$STR = “Total Users, Total Users Sending bad logon Attempts, AD Domain, Data File Location”
Add-Content $TestCSVFile $STR
$DataFileLocation=$CurrentLoc+”\”+$UniqueTest+”_DATA.CSV”
Remove-Item $DataFileLocation -ErrorAction SilentlyContinue
$STR = “User Location, BadLogonCount”
Add-Content $DataFileLocation $STR
$GDomList = “C:\Temp\DomainList.DPC”
$TotNo=0
$ItemCount=0
$TestText = “Please check result”
$TestStatus=”Completed”
$SumVal = “NA”
$AnyGap = “No”
ForEach ($ThisDomain in Get-Content “$GDomList”)
{
$AllComps = Get-ADUser -Filter * -Properties BadLogonCount,CanonicalName -Server $ThisDomain
$TotCompsNow = $AllComps.CanonicalName.Count
$TotWithBadAttempts = 0
ForEach ($Item in $AllComps)
{
$ThisDName = $Item.CanonicalName
$BadNumber = $Item.BadLogonCount
IF ($BadNumber -eq 0)
{
}
else
{
$AnyGap = “Yes”
$TotWithBadAttempts++
$STR = $ThisDName+”,”+$BadNumber
Add-Content $DataFileLocation $STR
}
}
$STR = $TotCompsNow.ToString()+”,”+$TotWithBadAttempts.ToString()+”,”+$ThisDomain+”,”+$DataFileLocation
Add-Content $TestCSVFile $STR
}
IF ($AnyGap -eq “Yes”)
{
$TestText = “Users are sending bad logon Attempts. Please check result.”
$SumVal = “”
$TestStatus=”High”
}
else
{
$TestText = ” “
$SumVal = “”
$TestStatus=”Passed”
}
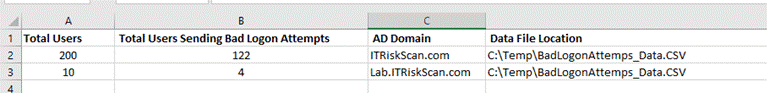
Once the script has finished death penalty, you’ll check the info within the C:\Temp folder. The 2 files created by the script give details concerning unhealthy logon counts. As you’ll see within the output below generated by the script, the outline shows the amount of users in every Active Directory domain, total users causing unhealthy logon tries in every domain, and record location. As you’ll see there area unit two hundred users in ITRiskScan.com domain and 122 users out of two hundred area unit causing unhealthy logon tries. Similarly, for Lab.ITRiskScan.com, the result shows that four out of ten users are causing unhealthy logon tries. The outline conjointly shows the info file location.
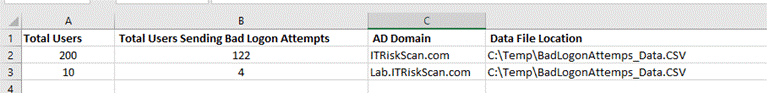
If you wish to see all WHO are causing unhealthy logon tries, open C:\Temp\BadLogonAttempts_Data.CSV file and establish the usename and variety of unhealthy logon tries by every user shown within the screenshot below:
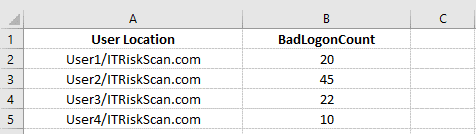
As you’ll see within the output higher than, the unhealthy logon try for user1 and user2 is twenty and forty five, severally. Once you’ve got the output with you, you’ll get in grips with the user and check on why there have been numerous unhealthy logon tries victimization their Active Directory logon credentials.
Take action:
Don’t simply sit there with the report. You need to take action to avoid any security risks. You’ll take the subsequent actions:
- Get in grips with the user and raise what percentage unhealthy logon tries were wiped out the past few days and why.
- Check with the user if they’re victimization Associate in Nursing Active Directory application that has been organized with a recent positive identification that’s triggering a nasty logon try.
- Check if the user put in any application recently that needed them to provide their credentials throughout the installation.
The script that you just see as a part of this text is obtained from DynamicPacks IT Health Profiler, a health and risk assessment product designed to assess risk and health problems in a lively Directory atmosphere as shown within the screenshot below: