This reference topic for the IT skilled contains supported written account setting data for the Windows implementation of the Transport Layer Security (TLS) protocol and also the Secure Sockets Layer (SSL) protocol through the Channel Security Support supplier (SSP). The written account sub keys and entries lined during this topic assist you administer and troubleshoot the Schannel SSP, specifically the TLS and SSL protocols.
Caution:
This data is provided as a relevancy use once you area unit troubleshooting or validator that the specified settings area unit applied. We tend to advocate that you simply don’t directly edit the written account unless there’s no alternative different. Modifications to the written account don’t seem to be valid by the written account Editor or by the Windows OS before they’re applied. As a result, incorrect values are often holding on, and this may lead to irrecoverable errors within the system. once doable, rather than piece of writing the written account directly, use cluster Policy or alternative Windows tools like the Microsoft Management Console (MMC) to accomplish tasks. If you want to edit the written account, use extreme caution.
Certificate Mapping Methods:
This entry doesn’t exist within the written account by default. The default price is that everyone four certificate mapping ways, listed below, area unit supported.
When a server application needs shopper authentication, Schannel mechanically tries to map the certificate that’s provided by the shopper pc to a user account. you’ll be able to certify users United Nations agency sign on with a shopper certificate by making mappings, that relate the certificate data to a Windows user account. once you produce and modify a certificate mapping, whenever a shopper presents a shopper certificate, your server application mechanically associates that user with the suitable Windows user account.
In most cases, a certificate is mapped to a user account in one in every of 2 ways:
A single certificate is mapped to one user account (one-to-one mapping).
Multiple certificates area unit mapped to at least one user account (many-to-one mapping).
By default, the Schannel supplier can use the subsequent four certificate mapping ways, listed so as of preference:
Kerberos service-for-user (S4U) certificate mapping
User principal name mapping
One-to-one mapping (also called subject/issuer mapping)
Many-to-one mapping
Applicable versions: As selected within the Applies To list that’s at the start of this subject.
Registry path: HKLM
SYSTEM\CurrentControlSet\Control\SecurityProviders\SCHANNEL
Ciphers:
TLS/SSL ciphers ought to be controlled by configuring the cipher suite order. For details, see Configuring TLS Cipher Suite Order.
For data concerning default cipher suites order that area unit employed by the Schannel SSP, see Cipher Suites in TLS/SSL (Schannel SSP).
CipherSuites:
Configuring TLS/SSL cipher suites ought to be done victimization cluster policy, MDM or PowerShell, see Configuring TLS Cipher Suite Order for details.
For data concerning default cipher suites order that area unit employed by the Schannel SSP, see Cipher Suites in TLS/SSL (Schannel SSP).
ClientCacheTime:
This entry controls the quantity of your time that the OS takes in milliseconds to expire client-side cache entries. a worth of zero turns off secure-connection caching. This entry doesn’t exist within the written account by default.
The first time a shopper connects to a server through the Schannel SSP, a full TLS/SSL shake is performed. once this can be complete, the master secret, cipher suite, and certificates area unit hold on within the session cache on the individual shopper and server.
Beginning with Windows Server 2008 and Windows visual image, the default shopper cache time is ten hours.
Registry path: HKLM
SYSTEM\CurrentControlSet\Control\SecurityProviders\SCHANNEL
Default shopper cache time
EnableOcspStaplingForSni:
Online Certificate standing Protocol (OCSP) stapling permits an online server, like web data Services (IIS), to supply the present revocation standing of a server certificate once it sends the server certificate to a shopper throughout the TLS shake. This feature reduces the load on OCSP servers as a result of internet the online the net} server will cache the present OCSP standing of the server certificate and send it to multiple web shoppers. While not this feature, every internet shopper would attempt to retrieve the present OCSP standing of the server certificate from the OCSP server. this may generate a high load on it OCSP server.
In addition to IIS, internet services over protocol.sys may enjoy this setting, together with Active Directory Federation Services (AD FS) and internet Application Proxy (WAP).
By default, OCSP support is enabled for IIS websites that have a straightforward secure (SSL/TLS) binding. However, this support isn’t enabled by default if the IIS web site is victimization either or each of the subsequent styles of secure (SSL/TLS) bindings:
Require Server Name Indication
Use Centralized Certificate Store
In this case, the server greeting response throughout the TLS shake will not embrace associate degree OCSP pinned standing by default. This behavior improves performance: The Windows OCSP stapling implementation scales to many server certificates. as a result of SNI and CCS modify IIS to scale to thousands of internet sites that doubtless have thousands of server certificates, setting this behavior to be enabled by default might cause performance problems.
Applicable versions: All versions starting with Windows Server 2012 and Windows eight.
Registry path:
[HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Control\SecurityProviders\SCHANNEL]
Add the subsequent key:
“EnableOcspStaplingForSni”=dword:00000001
To disable, set the DWORD price to 0:
“EnableOcspStaplingForSni”=dword:00000000
Note
Enabling this written account key contains a potential performance impact.
FIPSAlgorithmPolicy:
This entry controls Federal scientific discipline (FIPS) compliance. The default is zero.
Applicable versions: All versions starting with Windows Server 2012 and Windows eight.
Registry path: HKLM SYSTEM\CurrentControlSet\Control\LSA
Windows Server FIPS cipher suites: See Supported Cipher Suites and Protocols within the Schannel SSP.
Hashes:
TLS/SSL hash algorithms ought to be controlled by configuring the cipher suite order. See Configuring TLS Cipher Suite Order for details.
IssuerCacheSize:
This entry controls the dimensions of the institution cache, and it’s used with institution mapping. The Schannel SSP tries to map all of the institutions within the shopper’s certificate chain—not solely the direct issuer of the client certificate. Once the issuers don’t map to associate degree account, that is that the typical case, the server would possibly decide to map a similar institution name repeatedly, many times per second.
To prevent this, the server contains a negative cache, therefore if associate degree institution name doesn’t map to associate degree account, it’s further to the cache and also the Schannel SSP won’t decide to map the institution name once more till the cache entry expires. This written account entry specifies the cache size. This entry doesn’t exist within the written account by default. The default price is one hundred.
Applicable versions: All versions starting with Windows Server 2008 and Windows visual image.
Registry path: HKLM SYSTEM\CurrentControlSet\Control\SecurityProviders\SCHANNEL
IssuerCacheTime:
This entry controls the length of the cache timeout interval in milliseconds. The Schannel SSP tries to map all of the institutions within the shopper’s certificate chain—not solely the direct issuer of the client certificate. within the case wherever the issuers don’t map to associate degree account, that is that the typical case, the server would possibly decide to map a similar institution name repeatedly, many times per second.
To prevent this, the server contains a negative cache, therefore if associate degree institution name doesn’t map to associate degree account, it’s further to the cache and also the Schannel SSP won’t decide to map the institution name once more till the cache entry expires. This cache is unbroken for performance reasons, so the system doesn’t continue making an attempt to map a similar issuers. This entry doesn’t exist within the written account by default. The default price is ten minutes.
Applicable versions: All versions starting with Windows Server 2008 and Windows visual image.
Registry path: HKLM SYSTEM\CurrentControlSet\Control\SecurityProviders\SCHANNEL
KeyExchangeAlgorithm – shopper RSA key sizes:
This entry controls the shopper RSA key sizes.
Use of key exchange algorithms ought to be controlled by configuring the cipher suite order.
Added in Windows ten, version 1507 and Windows Server 2016.
Registry path: HKLM\SYSTEM\CurrentControlSet\Control\SecurityProviders\SCHANNEL\KeyExchangeAlgorithms\PKCS
To specify a minimum supported vary of RSA key bit length for the TLS shopper, produce a ClientMinKeyBitLength entry. This entry doesn’t exist within the written account by default. once you have got created the entry, amendment the DWORD price to the specified bit length. If not organized, 1024 bits are the minimum.
To specify a most supported vary of RSA key bit length for the TLS shopper, produce a ClientMaxKeyBitLength entry. This entry doesn’t exist within the written account by default. once you have got created the entry, amendment the DWORD price to the specified bit length. If not organized, then a most isn’t enforced.
KeyExchangeAlgorithm – Diffie-Hellman key sizes:
This entry controls the Diffie-Hellman key sizes.
Use of key exchange algorithms ought to be controlled by configuring the cipher suite order.
Added in Windows ten, version 1507 and Windows Server 2016.
Registry path: HKLM\SYSTEM\CurrentControlSet\Control\SecurityProviders\SCHANNEL\KeyExchangeAlgorithms\Diffie-Hellman
To specify a minimum supported vary of Diffie-Helman key bit length for the TLS shopper, produce a ClientMinKeyBitLength entry. This entry doesn’t exist within the written account by default. Once you have got created the entry, amendment the DWORD price to the specified bit length. If not organized, 1024 bits are the minimum.
To specify a most supported vary of Diffie-Helman key bit length for the TLS shopper, produce a ClientMaxKeyBitLength entry. This entry doesn’t exist within the written account by default. once you have got created the entry, amendment the DWORD price to the specified bit length. If not organized, then a most isn’t enforced.
To specify the Diffie-Helman key bit length for the TLS server default, produce a ServerMinKeyBitLength entry. This entry doesn’t exist within the written account by default. once you have got created the entry, amendment the DWORD price to the specified bit length. If not organized, 2048 bits are the default.
MaximumCacheSize:
This entry controls the most range of cache parts. Setting MaximumCacheSize to zero disables the server-side session cache and prevents reconnection. Increasing MaximumCacheSize on top of the default values causes Lsass.exe to consume extra memory. every session-cache part usually needs two to four kilobyte of memory. This entry doesn’t exist within the written account by default. The default price is twenty,000 parts.
Applicable versions: All versions starting with Windows Server 2008 and Windows visual image.
Registry path: HKLM SYSTEM\CurrentControlSet\Control\SecurityProviders\SCHANNEL
Messaging – fragment parsing:
This entry controls the most allowed size of fragmented TLS shake messages that may be accepted. Messages larger than the allowed size won’t be accepted and also the TLS shake can fail. These entries don’t exist within the written account by default.
When you set the worth to 0x0, fragmented messages don’t seem to be processed and can cause the TLS shake to fail. This makes TLS shoppers or servers on the present machine non-compliant with the TLS RFCs.
The maximum allowed size are often magnified up to 2^24-1 bytes. permitting a shopper or server to scan and store giant amounts of unproved information from the network isn’t an honest plan and can consume extra memory for every security context.
Added in Windows seven and Windows Server 2008 R2. associate degree update that allows web person in Windows XP, in Windows visual image, or in Windows Server 2008 to analyse fragmented TLS/SSL shake messages is accessible.
Registry path: HKLM\SYSTEM\CurrentControlSet\Control\SecurityProviders\SCHANNEL\Messaging
To specify a most allowed size of fragmented TLS shake messages that the TLS shopper can settle for, produce a MessageLimitClient entry. once you have got created the entry, amendment the DWORD price to the specified bit length. If not organized, the default price are 0x8000 bytes.
To specify a most allowed size of fragmented TLS shake messages that the TLS server can settle for once there’s no shopper authentication, produce a MessageLimitServer entry. Once you have got created the entry, amendment the DWORD price to the specified bit length. If not organized, the default price is 0x4000 bytes.
To specify a most allowed size of fragmented TLS shake messages that the TLS server can settle for once there’s shopper authentication, produce a MessageLimitServerClientAuth entry. Once you have got created the entry, amendment the DWORD price to the specified bit length. If not organized, the default price is 0x8000 bytes.
SendTrustedIssuerList:
This entry controls the flag that’s used once the list of trustworthy issuers is shipped. Within the case of servers that trust many certification authorities for shopper authentication, there area unit too several issuers for the server to be able to send all to the shopper pc once requesting shopper authentication. during this scenario, this written account key are often set, and rather than causing a partial list, the Schannel SSP won’t send any list to the shopper.
Not causing a listing of trustworthy issuers would possibly impact what the shopper sends once it’s asked for a shopper certificate. as an example, once web person receives asking for shopper authentication, it solely displays the shopper certificates that bind to at least one of the certification authorities that’s sent by the server. If the server didn’t send a listing, web person displays all of the shopper certificates that area unit put in on the shopper.
This behavior may be fascinating. as an example, once PKI environments embrace cross certificates, the shopper and server certificates won’t have a similar root CA; thus, web person cannot selected a certificate that chains up to at least one of the server’s CAs. By configuring the server to not send a trustworthy institution list, web person can send all its certificates.
This entry doesn’t exist within the written account by default.
Default Send trustworthy institution List behavior
Windows version Time
Windows Server 2012 and Windows eight and later FALSE
Windows Server 2008 R2 and Windows seven and earlier TRUE
Applicable versions: All versions starting with Windows Server 2008 and Windows visual image.
Registry path: HKLM SYSTEM\CurrentControlSet\Control\SecurityProviders\SCHANNEL
ServerCacheTime:
This entry controls the quantity of your time in milliseconds that the OS takes to expire server-side cache entries. a worth of zero disables the server-side session cache and prevents reconnection. Increasing ServerCacheTime on top of the default values causes Lsass.exe to consume extra memory. Every session cache part usually needs two to four kilobyte of memory. This entry doesn’t exist within the written account by default.
Applicable versions: All versions starting with Windows Server 2008 and Windows visual image.
Registry path: HKLM SYSTEM\CurrentControlSet\Control\SecurityProviders\SCHANNEL
Default server cache time: ten hours
SSL 2.0:
This subkey controls the employment of SSL two.0.
Beginning with Windows ten, version 1607 and Windows Server 2016, SSL 2.0 has been removed and isn’t any longer supported. For a SSL two.0 default settings, see Protocols within the TLS/SSL (Schannel SSP).
Registry path: HKLM SYSTEM\CurrentControlSet\Control\SecurityProviders\SCHANNEL\Protocols
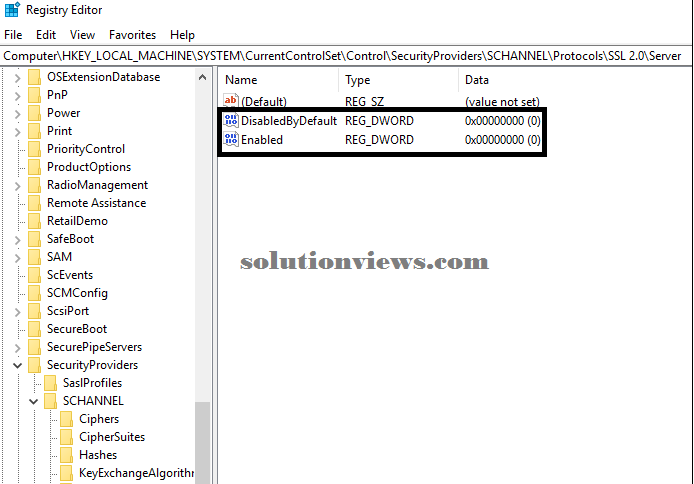
to modify the SSL two.0 protocol, produce associate degree Enabled entry in either the shopper or Server subkey, as delineated within the following table. This entry doesn’t exist within the written account by default. Once you have got created the entry, amendment the DWORD price to one.
Subkey Description
Client Controls the employment of SSL two.0 on the SSL shopper.
Server Controls the employment of SSL two.0 on the SSL server.
To disable SSL two.0 for shopper or server, amendment the DWORD price to zero. If associate degree SSPI app requests to use SSL two.0, it’ll be denied.
To disable SSL two.0 by default, produce a DisabledByDefault entry and alter the DWORD price to one. If associate degree SSPI app explcitly requests to use SSL two.0, it should be negotiated.
The following example shows SSL two.0 disabled within the registry:
SSL 3.0:
This subkey controls the employment of SSL three.0.
Beginning with Windows ten, version 1607 and Windows Server 2016, SSL 3.0 has been disabled by default. For SSL 3.0 default settings, see Protocols within the TLS/SSL (Schannel SSP).
Registry path: HKLM SYSTEM\CurrentControlSet\Control\SecurityProviders\SCHANNEL\Protocols
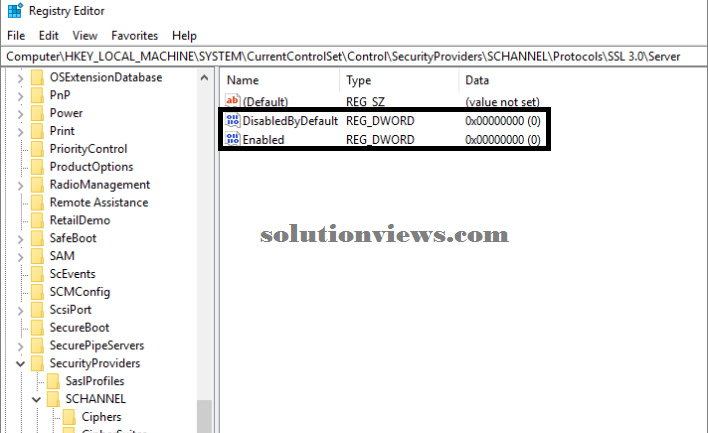
To modify the SSL three.0 protocol, produce associate degree Enabled entry in either the shopper or Server subkey, as delineated within the following table.
This entry doesn’t exist within the written account by default. once you have got created the entry, amendment the DWORD price to one.
SSL 3.0 subkey table
Subkey Description
Client Controls the employment of SSL three.0 on the SSL shopper.
Server Controls the employment of SSL three.0 on the SSL server.
To disable SSL three.0 for shopper or server, amendment the DWORD price to zero. If associate degree SSPI app requests to use SSL three.0, it’ll be denied.
To disable SSL three.0 by default, produce a DisabledByDefault entry and alter the DWORD price to one. If associate degree SSPI app expressly requests to use SSL three.0, it should be negotiated.
The following example shows SSL three.0 disabled within the registry:
TLS 1.0:
This subkey controls the employment of TLS one.0.
For TLS 1.0 default settings, see Protocols within the TLS/SSL (Schannel SSP).
Registry path: HKLM SYSTEM\CurrentControlSet\Control\SecurityProviders\SCHANNEL\Protocols
To modify the TLS one.0 protocol, produce associate degree Enabled entry in either the shopper or Server subkey as delineated within the following table. This entry doesn’t exist within the written account by default. once you have got created the entry, amendment the DWORD price to one.
TLS 1.0 subkey table
Subkey Description
Client Controls the employment of TLS one.0 on the TLS shopper.
Server Controls the employment of TLS one.0 on the TLS server.
To disable TLS one.0 for shopper or server, amendment the DWORD price to zero. If associate degree SSPI app requests to use TLS one.0, it’ll be denied.
To disable TLS one.0 by default, produce a DisabledByDefault entry and alter the DWORD price to one. If associate degree SSPI app expressly requests to use TLS one.0, it should be negotiated.
The following example shows TLS one.0 disabled within the registry:
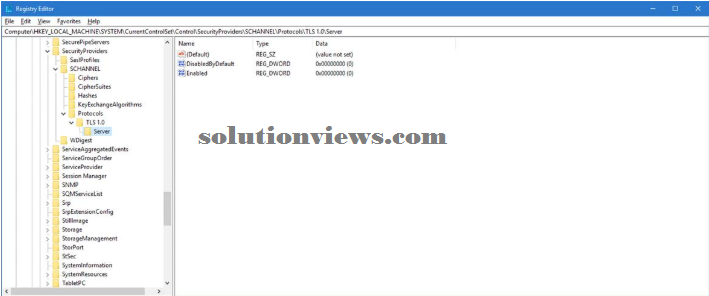
TLS 1.1:
This subkey controls the employment of TLS one.1.
For TLS 1.1 default settings, see Protocols within the TLS/SSL (Schannel SSP).
Registry path: HKLM SYSTEM\CurrentControlSet\Control\SecurityProviders\SCHANNEL\Protocols
to modify the TLS one.1 protocol, produce associate degree Enabled entry in either the shopper or Server subkey as delineated within the following table. This entry doesn’t exist within the written account by default. Once you have got created the entry, amendment the DWORD price to one.
TLS 1.1 subkey table
Subkey Description
Client Controls the employment of TLS one.1 on the TLS shopper.
Server Controls the employment of TLS one.1 on the TLS server.
To disable TLS one.1 for shopper or server, amendment the DWORD price to zero. If associate degree SSPI app requests to use TLS one.1, it’ll be denied.
To disable TLS one.1 by default, produce a DisabledByDefault entry and alter the DWORD price to one. If associate degree SSPI app expressly requests to use TLS one.1, it should be negotiated.
The following example shows TLS one.1 disabled within the registry:

TLS 1.2:
This subkey controls the employment of TLS one.2.
For TLS 1.2 default settings, see Protocols within the TLS/SSL (Schannel SSP).
Registry path: HKLM SYSTEM\CurrentControlSet\Control\SecurityProviders\SCHANNEL\Protocols
to modify the TLS one.2 protocol, produce associate degree Enabled entry in either the shopper or Server subkey as delineated within the following table. This entry doesn’t exist within the written account by default. Once you have got created the entry, amendment the DWORD price to one.
TLS 1.2 subkey table
Subkey Description
Client Controls the employment of TLS one.2 on the TLS shopper.
Server Controls the employment of TLS one.2 on the TLS server.
To disable TLS one.2 for shopper or server, amendment the DWORD price to zero. If associate degree SSPI app requests to use TLS one.2, it’ll be denied.
To disable TLS one.2 by default, produce a DisabledByDefault entry and alter the DWORD price to one. If associate degree SSPI app expressly requests to use TLS one.2, it should be negotiated.
The following example shows TLS one.2 disabled within the registry:
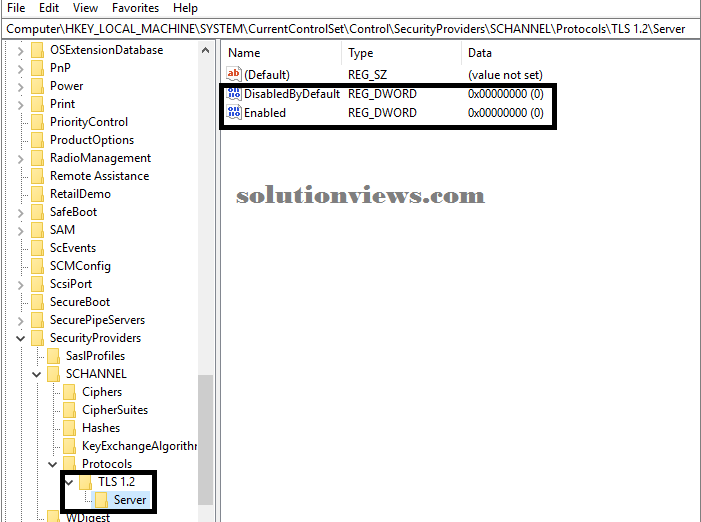
DTLS 1.0:
This subkey controls the employment of DTLS one.0.
For DTLS 1.0 default settings, see Protocols within the TLS/SSL (Schannel SSP).
Registry path: HKLM SYSTEM\CurrentControlSet\Control\SecurityProviders\SCHANNEL\Protocols
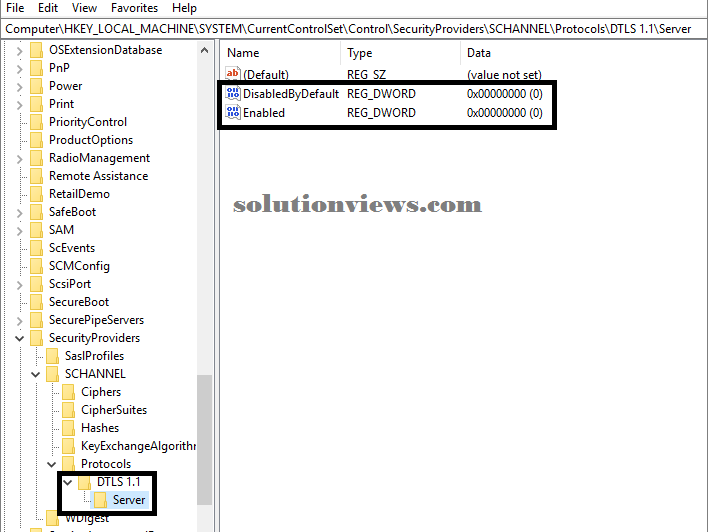
To modify the DTLS one.0 protocol, produce associate degree Enabled entry in either the shopper or Server subkey as delineated within the following table. This entry doesn’t exist within the written account by default. once you have got created the entry, amendment the DWORD price to one.
DTLS 1.0 subkey table
Subkey Description
Client Controls the employment of DTLS one.0 on the DTLS shopper.
Server Controls the employment of DTLS one.0 on the DTLS server.
To disable DTLS one.0 for shopper or server, amendment the DWORD price to zero. If associate degree SSPI app requests to use DTLS one.0, it’ll be denied.
To disable DTLS one.0 by default, produce a DisabledByDefault entry and alter the DWORD price to one. If associate degree SSPI app expressly requests to use DTLS one.0, it should be negotiated.
The following example shows DTLS one.0 disabled within the registry:
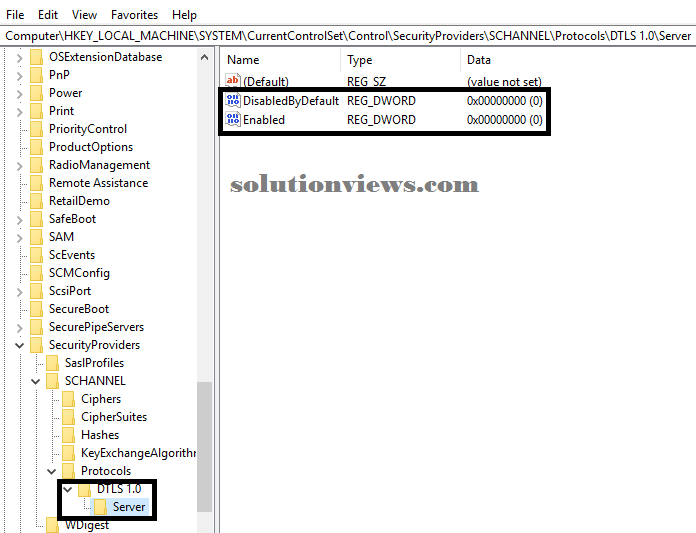
DTLS
1.2:
This subkey
controls the employment of
DTLS one.2.
For DTLS
1.2 default settings, see Protocols within the TLS/SSL (Schannel SSP).
Registry
path: HKLM
SYSTEM\CurrentControlSet\Control\SecurityProviders\SCHANNEL\Protocols
To modify the DTLS one.2 protocol, produce associate degree Enabled entry in either the shopper or Server subkey as delineated within the following
table. This entry doesn’t exist within the written account by default. once you have got created the entry, amendment the DWORD price to one.
DTLS 1.2
subkey table
Subkey Description
Client Controls the employment of DTLS one.2 on the DTLS shopper.
Server Controls the employment of DTLS one.2 on the DTLS server.
To disable DTLS one.2 for shopper or server, amendment the DWORD price to zero. If associate degree SSPI app requests to use DTLS one.0, it’ll be denied.
To disable DTLS one.2 by default, produce a DisabledByDefault entry and alter the DWORD price to one. If associate degree SSPI app expressly requests to use DTLS one.2, it should be negotiated.
The following example shows DTLS one.1 disabled within the registry: