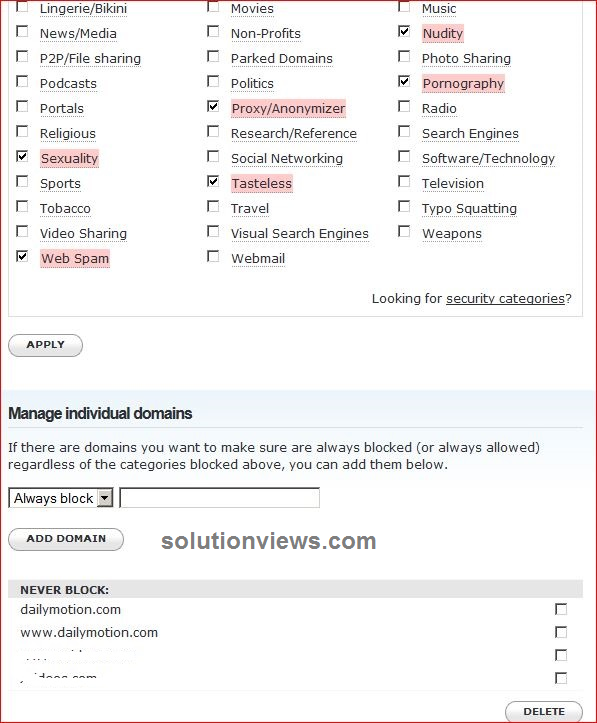
In this article, we tend to discuss ways that to bypass VPN blocks. Employing a VPN could be a good way to beat net censorship. beneath traditional circumstances, all you wish do is hook up with a VPN server set somewhere that’s not expurgated, and you have got uncensored access to the net.
The downside, of course, is that this feature of VPNs is well-known. And as a result, those that would censor your net conjointly try and block the utilization of VPNs to bypass their censorship…
Internet censorship
Internet censorship comes in several shapes and sizes. Common examples include:
Government censorship for political and/or social reasons:
Classic examples embody the nice Firewall of China and state censorship in Persia. The UAE has conjointly recently hit the headlines for criminalizing the utilization of VPNs and therefore the wish to bypass its censorship restrictions. For additional info regarding employing a VPN to bypass censorship in these countries see our VPN for UAE and VPN for China guides.
Government censorship for copyright reasons:
It is turning into more and more common for governments to dam access to websites that area unit deemed to market or facilitate copyright piracy. this manner of censorship is especially common in European counties, with the united kingdom leading the charge. Russia has conjointly recently ramped-up its efforts to dam access to pirated content.
Work:
Many workplaces try and stop workers from accessing content which may upset or offend alternative colleagues (see Not safe for work). Or that is probably going to distract them from work (such as chatting on social media). Such restrictions area unit typically quite comprehendible within the context of a operating atmosphere.
Schools and faculties:
It is common for academic establishments to dam access to web page. once the pupils area unit minors, this is often arguably even. it’s less therefore, though, at universities and better education institutions wherever the attendees area unit adults. Indeed, the notion of censorship at higher academic establishments is over a touch ironic!
Porn, social media and websites connected to infringement area unit typically the most targets. It’s not uncommon, however, for political content to be expurgated.

Even additional worrying is denying kids access to big info about social problems like drug recommendation, sexual health, racial and/or sexism, bullying, and more.
Websites that block VPNs:
It is turning into more and more common for media streaming websites to dam viewers WHO use VPNs bypass geo-restrictions placed on their services. Prime examples embody Hulu, US Netflix, and BBC player.
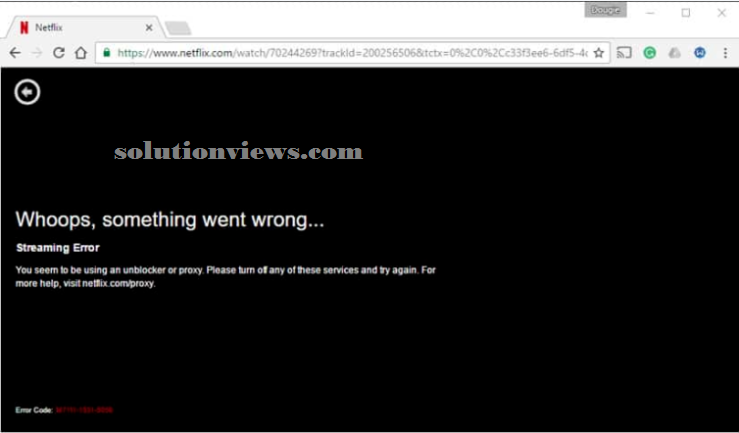
The reason for such blocks is sort of invariably as a result of copyright holders need to maximize their profits by unnaturally segregating the planet market.
Legal concerns:
VPN blocks area unit place into place for a reason, and therefore the folks putting them typically take a dim read of efforts to evade their blocks.
That said, even in countries wherever VPNs area unit blocked (such as China and Iran), their use is sort of ne’er really dirty. this implies that evading VPN blocks can nearly ne’er get you into hassle with the law.
A notable exception to the current general rule is that the UAE, that has recently declared that anyone caught employing a VPN risk a fine of up to a pair of Million UAE Dirham (over US$500,000) and/or jail time. however strictly this is often implemented in apply remains to be seen, however caution is powerfully suggested once making an attempt to evade VPN blocks within the UAE.
Of course, even supposing employing a VPN and bypassing VPN restrictions don’t seem to be typically dirty, per se, the content you access once mistreatment the VPN is also.
Safety concerns:
When employing a personal LAN or LAN network, the owner of that network has each right to limit what you’ll be able to do once connected to their network. This includes faculty, university, office, and residential networks, etc.
The chances of obtaining caught evading VPN restrictions on such networks is sometimes quite slim, however will doubtless end in suspension, sacking, and alternative disciplinary measures.
It is, therefore, value fastidiously considering whether or not the advantage of evading VPN blocks justifies the potential issues, do you have to get caught.
How VPN blocks work:
VPN use are often prevented during a range of the way, and organizations that area unit serious regarding block VPNs typically mix techniques.
Note that with the exception of China (where all net traffic to and from China is restricted to merely three government controlled access points), government VPN blocks (and censorship) is sort of invariably really performed by ISPs at the government’s instruction.
Common techniques for VPN blocks include:
Blocking access to VPN websites:
If you can’t access a VPN provider’s web site then you can’t sign-up for its service or transfer its package. This manner of censorship typically extends to VPN review websites (such as ProPrivacy.com) and alternative websites dedicated to strategies of evading censorship.
Although seldom the sole plan of action used, block access to VPN websites could be a quite common addition to alternative strategies used.
Blocking IPs of familiar VPN servers:
It is not too troublesome to find the scientific discipline addresses of the VPN servers employed by VPN suppliers. and so block access to them.
This is far and away the foremost common technique of preventing VPN use, and once used along with block access to VPN websites, is sometimes the extent of most VPN blocks.
Given the massive range of VPN suppliers out there, and therefore the problem of keeping track of fixing server scientific discipline addresses, most organizations accept ban simply the additional in style VPN services. this implies that users of smaller and fewer well-known VPN services will typically “slip beneath the radar”.
Port block:
By default, OpenVPN uses port 1194 (UDP, though this will be simply modified to TCP). alternative VPN protocols use completely different ports. an easy however effective thanks to block VPNs, therefore, is to use a firewall to dam these ports.
Deep packet scrutiny (DPI)
Deep packet scrutiny is “a kind of network packet filtering that examines the info half (and probably conjointly the header) of a packet because it passes Associate in Nursing scrutiny purpose.” numerous technologies area unit used for DPI, with variable levels of effectiveness.
Data encapsulated by VPN protocols, however, is pretty straightforward to identify mistreatment even fairly basic DPI techniques. The content of the packets remains firmly encrypted, however DPI will verify that it’s been encrypted employing a VPN protocol.
Using DPI to observe VPN traffic is certainly a maximize in seriousness on the a part of the organization playacting the DPI.
Simple Solutions:
Use a mobile association:
Ok, therefore this won’t work for evading government blocks, however it’ll work faculties, colleges, at work, etc. And it’s typically far and away the best answer. instead of employing a VPN to access content blocked on the native network, simply access it on your mobile device mistreatment your mobile (cellular) association.
This will mean that you simply can ought to pay your usual mobile information charges, however it permits you to envision your Facebook account while not with very little effort and tiny likelihood of entering into hassle for it.
Try a distinct VPN supplier and/or servers:
As already noted, keeping track of all scientific discipline addresses happiness to any or all VPN suppliers could be a big task. change to a lower-profile VPN service is so typically enough to evade blanket scientific discipline blocks. though some IPs happiness to a specific VPN blocked, merely dynamic to completely different ones pass by an equivalent supplier may work.
Some VPN suppliers often recycle their scientific discipline addresses. This makes keeping track of the changes and block the new IPs a serious headache. This plan of action is commonly said as a game of “whack-a-mole”. it’s value asking your supplier if this is often one thing that it will.
Not several VPN suppliers presently totally support IPv6 (Mullvad is that the only 1 i do know of). this is often nearly absolute to modification, however, as new IPv4 addresses become inaccessible. scientific disciplinev6 massively expands the quantity of IP addresses accessible. this implies that as IPv6 becomes additional wide adopted, easy scientific discipline blocks can decrease and fewer effective.
Roll your own VPN:
A additional extreme however extremely effective possibility is to run your own VPN server and so hook up with it from the expurgated location.
As the VPN server belongs to you, this doesn’t give the standard privacy edges of employing a business VPN service. It does, however, give you together with your terribly own distinctive VPN scientific discipline address, which cannot be blocked.
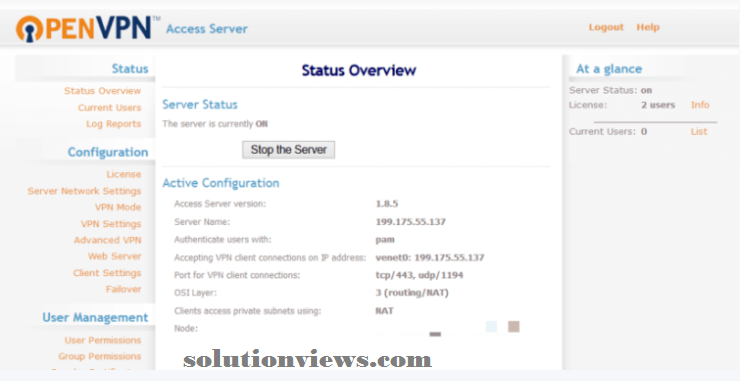
You can setup a home laptop to act as your personal VPN server, or rent and set up a VPS (which is additionally nice for geospoofing). If rolling your own VPN on a VPS appears too onerous, PrivatePackets.io will do the work for you.
Dedicated scientific discipline addresses:
Some VPNs provide dedicated scientific discipline addresses. this implies that rather than sharing Associate in Nursing scientific discipline with several alternative users, you’re allotted a novel scientific discipline (much like if you roll your own VPN ). as a result of this scientific discipline is exclusive to you, it’s impossible to be blocked by websites like Netflix and BBC iPlayer. like rolling your own VPN, though, it doesn’t have the privacy edges of employing a shared scientific discipline address.
Unblock iPlayer with a VPN
Come ready:
When visiting places like China, one amongst the foremost effective techniques is solely return prepared! Signup for a VPN service and transfer its package before your visit. Even once access to access to VPN providers’ websites is blocked, VPN connections themselves area unit typically not.
If you have got did not return ready (or ne’er had the opportunity), various censorship-busting technologies are often accustomed access VPN websites. you’ll be able to then sign-up and transfer their package.
Tor network:
Tor is best at providing obscurity than it’s at censorship-busting. {this is|this is often |this are often} thanks to the benefit with that access to Tor nodes can be blocked. Tor bridges are often accustomed bypass scientific discipline blocks on Tor nodes, and obfsproxy (see below) are often accustomed hide Tor traffic from Deep packet scrutiny.
Shadowsocks (Chinese: 影梭):
This “is Associate in Nursing ASCII text file proxy application, wide employed in Communist China to bypass net censorship.” it’s Associate in Nursing open supply anti-GFW tool/protocol/server created by a Chinese developer. Essentially it’s a SOCKS5 proxy that’s accessible for many major platforms.
Surge:
This is the same as Shadowsocks, however is barely accessible for iOS.
Lahana:
Derived from Tor, Lahana is intended to resolve Tor’s downside with simply blocked exit nodes by creating it “stupidly easy” to setup new nodes. Lahana was designed to defeat censorship in Turkey, however ought to conjointly work well in several alternative censorship things.
Psiphon:
This uses a mix of VPN, SSH and obfuscation technologies to bypass censorship. If you encounter a block once mistreatment VPN, as an example, you’ll be able to switch to SSH or obfuscated SSH (SSH+) instead. one amongst the simplest things regarding Psiphon is that if you discover the Psiphon web site blocked, you’ll be able to request the package be sent to you via email.
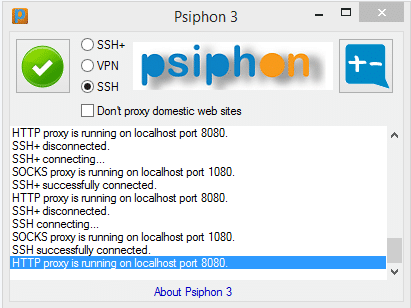
In fact, most VPN suppliers also will be happy allow you to sign on and transfer their package via email. Just ask.
Change port numbers:
Many custom VPN shoppers enable you modify the port they use. this is often a decent thanks to defeat port block. The 2 preferred selections of port to use are:
TCP port eighty – this is often the port uses by all “normal” unencrypted net traffic. In alternative words, it’s the port employed by communications protocol. Block this port effectively blocks the net, and is so nearly ne’er done. The drawback is that even the foremost primitive DPI techniques can spot VPN traffic mistreatment this port.
TCP port 443 – this is often the port employed by HTTPS, the encrypted protocol that secures all secure websites. While not HTTPS no kind of on-line commerce, like searching or banking, would be doable. it’s so terribly rare for this port to be blocked.
And as another bonus, VPN traffic on TCP port 443 is routed within the TLS cryptography employed by HTTPS. This makes it abundant more durable to identify mistreatment DPI. TCP port 443 is so the favored port for evading VPN blocks.
Many VPN suppliers provide the power to vary port numbers mistreatment their custom package (especially once mistreatment the OpenVPN protocol).
Even if yours doesn’t, several VPN suppliers do really support OpenVPN mistreatment TCP port 443 at the server level. You’ll be able to switch to that with an easy edit to your OpenVPN configuration (.ovpn) file. It’s so value asking your VPN supplier regarding this.
Another option is to use the SSTP protocol (if available), that uses TCP port 443 by default.
Advanced solutions:
Some VPN suppliers provide additional advanced VPN block solutions designed to defeat additional sensitive DPI techniques. Such techniques analyze packet size and/or temporal order to observe OpenVPN’s rather distinctive acknowledgment, even once hidden behind HTTPS.
Very sensitive (and so conjointly terribly dear, and barely used) DPI could even observe VPN use once mistreatment the techniques printed below. There area unit a pair of basic approaches to advanced VPN concealment:
stunnel / SSL tunneling:
stunnel is Associate in Nursing open supply multi-platform program that makes TLS/SSL tunnels. TLS/SSL is that the cryptography employed by HTTPS, therefore VPN connections (usually OpenVPN) routed through these TLS/SSL tunnels area unit so terribly troublesome to inform aside from regular HTTPS traffic.
This is as a result of the OpenVPN information is wrapped within an extra layer of TLS/SSL cryptography. As DPI techniques area unit unable to penetrate this “outer” layer of cryptography, they’re unable to observe the OpenVPN cryptography “inside”.
SSL tunnels area unit typically created mistreatment the stunnel package. This should be organized on each the VPN server and your laptop. It is, therefore, necessary to debate the case together with your VPN supplier if you wish to use SSL tunneling (a setup guides are out there here for reference).
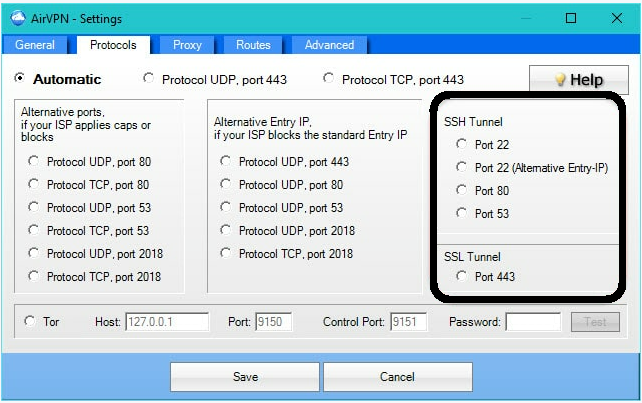
AirVPN is that the solely VPN supplier i do know of to supply stunnel practicality “out of the box” mistreatment its custom open supply package. i’m not otherwise acquainted with Anonyproz, however it are often organized for stunnel, and alternative suppliers may additionally provide this feature.
SSH tunneling:
This is the same as SSL tunneling, except that the VPN information is wrapped within a layer of Secure Shell (SSH) cryptography instead. SSH is employed primarily for accessing shell accounts on UNIX operating system systems. Its use is especially restricted to the business world, and is obscurity close to as in style as SSL.
As with SSL tunneling, you may ought to confer with your VPN supplier to urge it operating.
Obfsproxy (and similar technologies):
Obfsproxy could be a tool designed to wrap information into Associate in Nursing obfuscation layer. This makes it troublesome to observe that OpenVPN (or the other VPN protocol) is being employed.
It has been adopted by the Tor network, mostly as a response to China block access to public Tor nodes. it’s freelance of Tor, however, and may be organized for OpenVPN .
To work, obfsproxy has to be put in on each the client’s laptop (using, as an example, port 1194), and therefore the VPN server. However, all that’s then needed is that the subsequent statement be entered on the server:
obfsproxy obfs2 –dest=127.0.0.1:1194 server x.x.x.x:5573
This tells obfsproxy to pay attention on port 1194 (for example), to attach domestically to port 1194 and forward the de-encapsulated information to that (x.x.x.x ought to get replaced together with your scientific discipline address or zero.0.0.0 to pay attention on all network interfaces). it’s in all probability best to line up a static scientific discipline together with your VPN supplier therefore the server is aware of that port to pay attention in on.
Compared to stunnel and SSH tunneling, obfsproxy isn’t as secure. this is often as a result of it doesn’t wrap the traffic in cryptography. It is, however, somewhat easier to line up and set up, and contains a abundant lower information measure overhead since it’s not carrying an extra layer of cryptography. this will be significantly relevant for users in places like Syria or Yaltopya, wherever information measure is commonly a important resource.
Some suppliers could use various technologies that area unit the same as obsfproxy. BolehVPN , as an example, uses XOR obfuscation for its “xCloak” servers.
Addendum:
A note on the UAE:
The on top of advanced solutions to VPN block can in all probability stop VPN use being detected by DPI techniques (although the United Arab Emirates has been finance heavily in advanced net police work systems).
It is believed, however, that UAE ISP may maintain an in depth information of VPN server IPs. They’ll be simply ready to verify that you simply area unit employing a VPN just by the scientific discipline you hook up with (much as websites like Netflix do).
In reality, it appears unlikely that you simply are prosecuted only for employing a VPN to observe Netflix within the UAE. If you piss the authorities off in how, however, the very fact that you simply use a VPN could offer them a dangerous weapon to use against you.
We invariably advocate extreme caution once considering mistreatment VPN in UAE.
A note on websites that block VPN users:
This form of block are often difficult to beat. Selecting a lower-profile VPN supplier, or one that often recycles its IPs, are often effective. Trial and error is that the key here.
We powerfully advise that you simply take full advantage of any free trials and money-back guarantees that area unit on provide. this can enable you to seek out out for yourself that VPN services work for the content you wish to stream.
Remember that a service that works nowadays may well be blocked tomorrow. therefore it’s a decent plan to get a month’s subscription at a time. this is often nearly always dearer than paying annually. however if the service becomes blocked (through no fault of its own), you may not be left with a year’s subscription that’s useless to you!
It might even be value gazing good DNS solutions, rather than employing a VPN. good DNS services can even be blocked, however this is often harder to try and do and is a smaller amount doubtless to happen. Fewer good DNS services area unit illegal than VPN services.
Some VPN services, like AirVPN, use fancy DNS routing. this enables you to attach to services like United States of America Netflix and iPlayer, even after you don’t seem to be connected to servers within the United States of America or United Kingdom of Great Britain and Northern Ireland (respectively)! this is often not invariably 100% effective, however is nonetheless spectacular.
Conclusion:
The overwhelming majority of VPN blocks area unit fairly straightforward to beat employing a very little heuristic. Even wherever refined and sensitive Deep packet inspections techniques area unit used, technologies like stunnel and obfsproxy area unit extremely effective.