If a user password has been brute-forced, the account lockout policy in the Active Directory domain allows you to automatically lock the user account. Using Group Policy, an AD domain administrator can set account lockout policies (GPO).
In an AD domain, you can only create one password and lockout policy by default. Expand your domain and look for the GPO called Default Domain Policy in the Group Policy Management console (gpmc.msc). Select Edit from the context menu by right-clicking on the object.
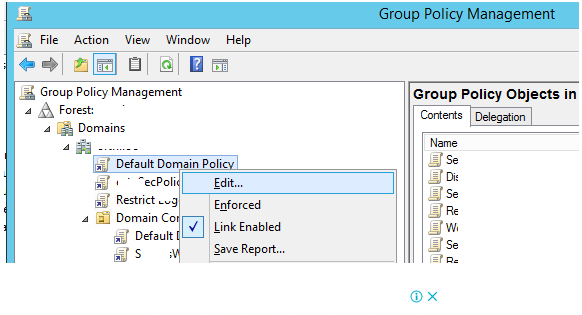
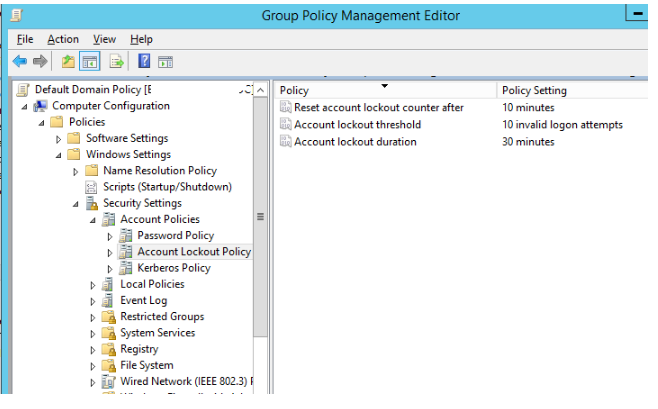
Go to the section Computer Configuration > Windows Settings > Security Settings > Account Policy > Account Lockout Policy in the Group Policy Editor.
There are three account lockout policies to choose from:
- Reset account lockout counter after – this option determines how long the counter of failed authorisation attempts is kept after it is reset (in minutes from 1 to 99999). In this case, we’ll use a value of 10 minutes.
- Account lockout threshold – the number of failed password tries before the Windows account is locked out (from 0 to 999). The account will never be locked if this value is set to 0. We use the following value: ten failed logon attempts;
- Account lockout time – the time it takes for an Active Directory user account to be locked out (from 0 to 99999 minutes). If you provide 0, the account will be locked until the administrator unlocks it using the Unlock-ADAccount cmdlet or the Active Directory Users and Computers GUI.
You must wait up to 2 hours after making changes to the Default Domain Policy before applying the policy to the domain, or you can manually update the policy on the DCs with the gpupdate command.
When the user enters the proper password after locking the account in AD, the computer displays the following message:
The account in question is now locked out and cannot be accessed.
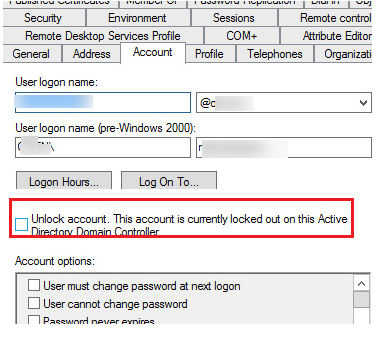
If you open the ADUC snap-in (dsa.msc), locate the user account, and then click the Account tab, you’ll see the following caption:
Account must be unlocked. On this Active Directory Domain Controller, this account is now locked out.
You can define additional password and lockout restrictions for individual accounts or groups in Windows Server 2008 and newer. Fine Grained Password Policy is the name of this technology. This feature eliminates a constraint in prior versions of Windows, which allowed only one password policy to be configured per domain.
The specific password setting objects in the container System > Password Settings Container are used to configure these FGGP policies in the Active Directory Administration Center.
From PowerShell, you may establish a PSO and set a separate lockout policy to a specified group of users:
New-ADFineGrainedPasswordPolicy -Name “Sales_PSO” -Precedence 2 -Description “Account Lockout policy for Sales dept” -DisplayName “Sales_PSO“ - LockoutDuration "8:00" -LockoutObservationWindow "8:00" - LockoutThreshold 20After that, you can assign a security group to a policy:
Add-ADFineGrainedPasswordPolicySubject -Identity "Sales_PSO" -Subjects "Sales Dept"Use the dsquery and dsget commands on the domain controller to see which password policy is applied to the user:
dsquery user -samid username | dsget user -effectivepso