Users’ permissions to various domain services and resources are granted using Active Directory security groups. As a result, looking at the groups in which the user account is a member is all it takes to figure out what permissions are allocated to a specific user in the AD domain.
Getting Group Membership via ADUC
Obtaining Group Membership through ADUC
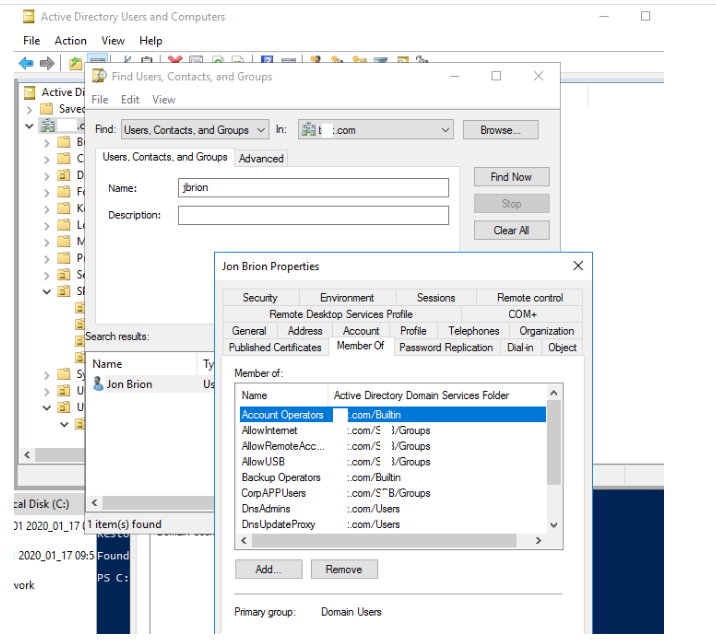
The graphical snap-in Active Directory Users & Computers is the simplest and clearest way to acquire a list of user groups in AD (ADUC).
- Run the dsa.msc snap-in;
- Select Find with a right-click on the domain root;
- Click Find Now after entering a username.
- Go to the Member of tab in the user properties;
- This page displays a list of the groups in which the specified user is a member.
Checking AD Group Membership via Command Line
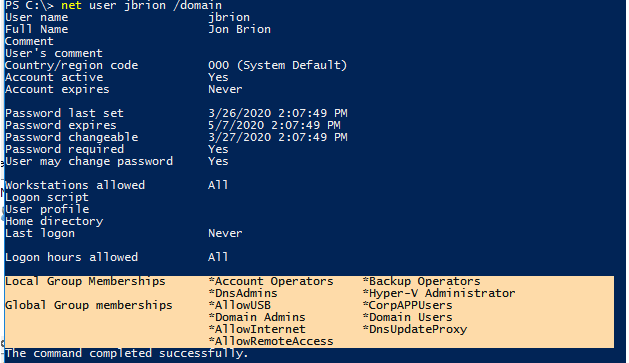
You may also use the command-line to check Active Directory group membership. Execute the following command:
net user USERNAME /domainThe command output, as you can see, includes the user’s domain (Global Group Memberships) and local groups (Local Group Memberships).
Using the following command, you can list the security groups that your account is a member of:
whoami /groupsList the members of the domain group:
Net group "CorpAPPUser" /DOMAIN
The biggest disadvantage of the above solutions is that the nested AD groups are not displayed (when the group is a member of other security groups).
Using the dsget utility, you can see a complete list of user groups (including nested ones). You must supply its distinguishedName instead of a username:
dsget user "CN=Jon Brion,OU=Users,OU=UK,DC=solutionviews,DC=com" -memberof –expand
If you need to get the members of a specific security group, including nested group membership, use the command:
dsget group "CN=NY-Managers,OU=Users,OU=NY,DC=solutionviews,DC=com" –members -expandWhen you need to do the opposite operation and display a list of groups in which the group belongs, run:
dsget group "CN=NY-Managers,OU=Users,OU=NY,DC=solutionviews,DC=com" –memberof
-expand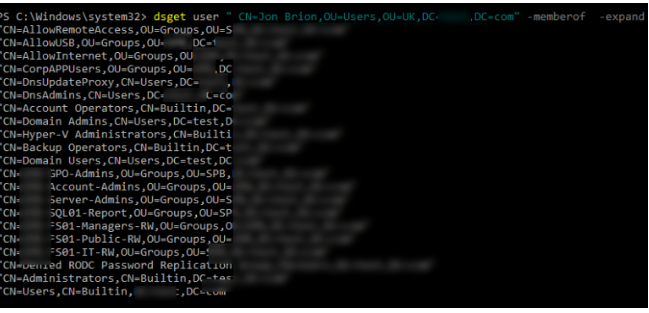
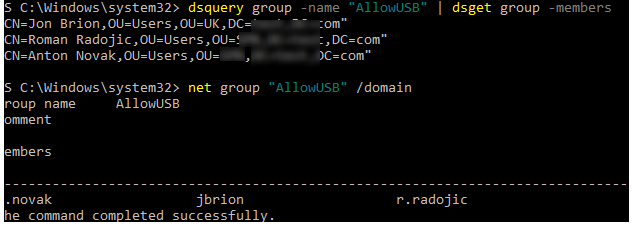
Using dsquery and net group commands, you can display the members of a specific AD group:
dsquery group -name "AllowUSB" | dsget group -membersor:
net group "AllowUSB" /domain
How to List AD Group Members using PowerShell?
The PowerShell cmdlets Get-AdUser and Get-ADPrincipalGroupMembership can also be used to examine user AD group membership. You’ll need the PowerShell Active Directory module installed on your PC in order to perform this.
On Windows 10, you’ll need to install RSAT to use the AD PowerShell Module.
Only usernames that have been added to a specific AD group (including nested groups) will be displayed:
Import-module Activedirectory
Get-ADGroupMember -Identity AllowUSB -Recursive | ft nameDisplay group members with detailed information on each member:
Get-ADGroupMember -Identity AllowUSB | foreach { Get-ADUser $_ -Properties * }You can display only certain attributes of users in a group:
Get-ADGroupMember -Recursive GroupName" | ForEach {Get-ADUser -filter {samaccountname -eq $_.SamAccountName} -Properties displayName, company, title, department } | Format-Table displayName,company,department,title -AutoSizeThe list of Active Directory groups in which the user is a member can be displayed using the following commands:
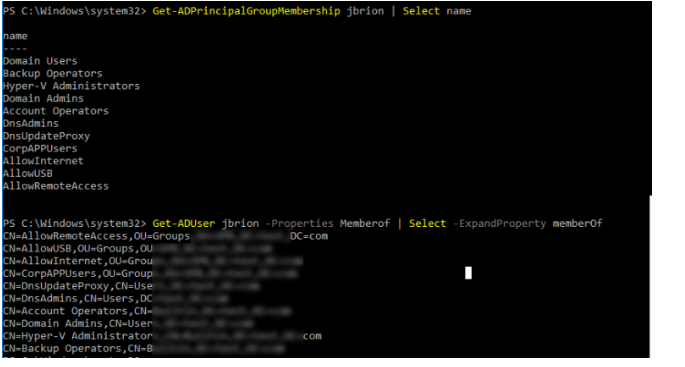
Get-ADPrincipalGroupMembership jbrion | Select nameor
Get-ADUser jbrion -Properties Memberof | Select -ExpandProperty memberOfHint. If you need to export the resulting list of groups or users to a text CSV file, add the following line to the end of any of the PowerShell commands discussed here:
| Export-Csv -NoTypeInformation .\ad_group.csv -Encoding UTF8
Another way to get a list of all members of a group (explicit or implicit) is to use the –RecursiveMatch operator:
Get-ADUser -Filter {MemberOf -RecursiveMatch "CN=NY-Sales,OU=Groups,OU=NY,DC=solutionviews,dc=com"}If we are interested only whether a certain user belongs to a certain group, we can proceed as follows:
Get-ADUser -Filter {MemberOf -RecursiveMatch "CN=NY-Sales,OU=Groups,OU=NY,DC=solutionviews,dc=com"} -SearchBase "CN=User,OU=Users,OU=NY,DC=solutionviews,DC=com"You can use the filter by group name:
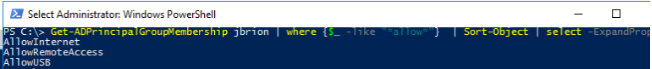
Get-ADPrincipalGroupMembership jbrion | where {$_ -like "*allow*"} | Sort-Object | select -ExpandProperty name
You can use complex LDAP filters to get nested group membership. For instance, to get a full list of the groups to which a user account belongs (including nested groups), use the command:
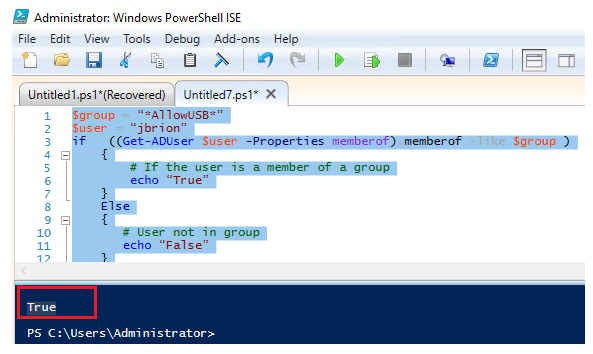
Get-ADGroup –LDAPFilter (member:1.2.840.113556.1.4.1941:=CN=John Brion,OU=Employees,OU=NY,DC=solutionviews,DC=co,)The following PowerShell script template can be used to check a user’s membership in a specific Active Directory group and perform some actions depending on group membership (the group name must be specified between the * characters):
$group = “*AllowUSB*”
$user = “jbrion”
if ((Get-ADUser $user -Properties memberof).memberof -like $group )
if ((Get-ADUser $user -Properties memberof).memberof -like “*$group*” )
{
# If the user is a member of a group
echo “True”
}
Else
{
# User not in group
echo “False”
}