Auditing helps you collect activities performed by totally different elements of an energetic Directory domain controller. Microsoft provides auditing configuration for domain controllers to assist Active Directory directors audit events like Active Directory replication events, Active Directory configuration events, Active Directory changes events, and different events that a website controller would perform. Whereas Active Directory provides the capabilities to audit events, audit configuration should be enabled on the domain controllers. Another vital item, as a part of your Active Directory medical, is to make sure the audit configuration is consistent on all domain controllers in an energetic Directory forest. As an example, if you’re auditing Directory Services Access, you want to make sure that all domain controllers have Directory Service Access auditing enabled. Inconsistent audit configuration would cause confusion. you will additionally not be able to troubleshoot a difficulty if a specific auditing class isn’t enabled on a website controller.
Why alter auditing on domain controllers?
There area unit many reasons on why you ought to alter auditing on domain controllers. One among the explanations is to keep up a record of activities performed by the domain controllers just in case you wish to research a difficulty. Another excuse would be to stay auditing events generated by domain controllers for compliance and security reasons. Finally, if you propose to implement a happening collector product that collects events from domain controllers and stores during a central location, you may be needed to alter audit configuration on the domain controllers.
Four varieties of audit configuration for domain controllers:
There are a unit four varieties of audit configuration out there for an energetic Directory domain controller as listed below:
Directory Service Access: permits you to audit directory service audits low-level changes to things in Active Directory. As an example, by sanctionative Directory Service Access, you’ll determine that fields of a user or laptop account were accessed. The Directory Service Access setting should be enabled for compliance and security functions.
Directory Service Changes: Directory Service Changes auditing determines whether or not the domain controller generates audit events once changes area unit created to users, computers, or any active directory objects in Active Directory. sanctionative Directory Service Changes auditing will give data regarding the previous and new properties of the objects that were modified.
Directory Service Replication: Directory Service Replication auditing determines whether or not the domain controller generates audit events once replication between 2 domain controllers begins.
Detailed Directory Service Replication: elaborate Directory Service Replication determines whether or not the domain controller generates audit events that contain elaborate chase data regarding replication information.
Which auditing configuration must you alter on domain controllers?
There are a unit four varieties of audit configuration settings that may be enabled on domain controllers as explained within the earlier section of this text, however not essentially you wish to alter all audit configuration settings on domain controllers. As an example, sanctionative Directory Service Replication audit configuration setting makes no sense during a massive production setting. it’s as a result of an oversized production setting may see a lot of changes to occur in Active Directory inflicting a lot of changes to be replicated, which, in turn, may fill the event logs if Directory Service Replication auditing is enabled. Similarly, sanctionative elaborate Directory Service Replication would cause elaborate replication information to be logged. Thus, it’s counseled that you just alter Directory Service Access and Directory Service Changes audit configuration to be able to track changes created by Active Directory directors and it’s additionally needed for compliance functions.
How does one check audit configuration?
A PowerShell script may be handy to visualize auditing configuration on domain controllers, however it’s vital to grasp that Microsoft PowerShell modules don’t give any cmdlets to visualize the auditing configuration on domain controllers. Instead, you want to use AuditPol.exe. Whereas it sounds a small amount freaky, there’s so no PowerShell cmdlet out there to visualize audit configuration on domain controllers!
Checking auditing configuration on one domain controller:
AuditPol.exe provides many parameters through that you’ll check totally different elements of the auditing configuration. However, to visualize audit configuration on one domain controller and see what all auditing classes area unit enabled, execute below command:
Auditpol /get /Category:* /r
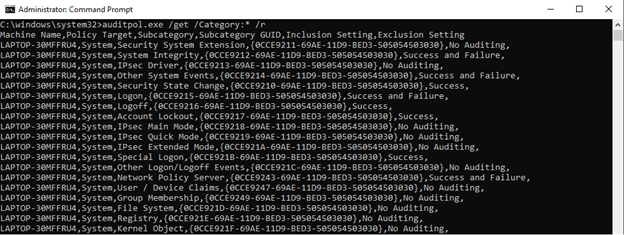
As you’ll see within the output higher than generated by the higher than command, it shows class being audited and current setting that’s designed for auditing on a specific auditing class. “No auditing” implies that a specific class isn’t being audited. Since AuditPol.exe output is in CSV, you’ll use a redirector within the command higher than to store the output during a CSV file because it shows within the command below:
Auditpol /get /Category:* /r > C:\Temp\AuditOutput.CSV
Note that the higher than command fetches audit configuration on the native laptop. thus if you’re associate attempt|attempting} to urge an audit configuration for a specific domain controller, you may be needed to go online to it domain controller so run the command higher than.
Checking auditing configuration on an overseas domain controller
If you’d prefer to get an inventory of audit classes from an overseas domain controller, you may got to execute AuditPol command remotely victimization “Invoke-Command” PowerShell methodology. Sadly, AuditPol.exe doesn’t ship with a parameter that may be accustomed specify a laptop name as most of the PowerShell cmdlets do. to urge an inventory of audit classes from an overseas domain controller, you may execute below command:
$ItemName = “DC1.Solutionviews.com.com”
$AuditStatus
= Invoke-Command -ComputerName $ItemName -Script { auditpol.exe /get
/Category:* /r
As you’ll see within the command higher than, i’m victimization “Invoke-Command” PowerShell cmdlet, that supports execution a command on an overseas laptop laid out in -ComputerName parameter. you wish to exchange “DC1.Solutionviews.com.com” with the name of the domain controller before execution the command. The command connects to the target domain controller and lists the classes within the PowerShell window on the native laptop.
Collecting auditing configuration from all domain controllers and generating a report:
If you wish to gather audit configuration from all domain controllers in an energetic Directory forest to make sure audit configuration is consistent across all domain controllers. The PowerShell script below may be dead to gather audit configuration and generate a report in CSV format.
$GDCList="C:\Temp\DCList.CSV"
$TestCSVFile ="C:\Temp\AuditReport.CSV"
Remove-Item $TestCSVFile
$UniqueTest = "RC"
$CurrentLoc="C:\Temp"
$STR = "Domain Controller, Directory Service Access, Directory Service Changes, Directory Service Replication, Detailed Directory Service Replication"
Add-Content $TestCSVFile $STR
$TotNo=0
$ItemCount=0
$TestText = "Please check result"
$TestStatus="Completed"
$SumVal = "NA"
$AnyGap = "No"
Foreach ($ItemName in Get-Content "$GDCList")
{
$IntOnOrNot = ""
Remove-item $DataFileLocation -ErrorAction SilentlyContinue
$Error.Clear()
$AuditStatus = Invoke-Command -ComputerName $ItemName -Script { exe /get /Category:* /r }
IF ($Error.Count -eq 0)
{
$AuditStatus > $DataFileLocation
$CSV = Import-CSV $DataFileLocation
ForEach ($Item in $CSV)
{
$MName = $Item.Subcategory
$IncSet = $Item.'Inclusion Setting'
IF ($MName -eq "Directory Service Access")
{
$DirSuccessOrNot = "Enabled"
IF ($IncSet -eq "No Auditing")
{
$DirSuccessOrNot = "Not Enabled"
}
}
IF ($MName -eq "Directory Service Changes")
{
$DirChangesOrNot = "Enabled"
IF ($IncSet -eq "No Auditing")
{
$DirChangesOrNot = "Not Enabled"
}
}
IF ($MName -eq "Directory Service Replication")
{
$DirReplOrNot = "Enabled"
IF ($IncSet -eq "No Auditing")
{
$DirReplOrNot = "Not Enabled"
}
}
IF ($MName -eq "Detailed Directory Service Replication")
{
$DirReplDOrNot = "Enabled"
IF ($IncSet -eq "No Auditing")
{
$DirReplDOrNot = "Not Enabled"
}
}
}
$STR = $ItemName+","+$DirSuccessOrNot+","+$DirChangesOrNot+","+$DirReplOrNot+","+$DirReplDOrNot
Add-Content $TestCSVFile $STR
}
else
{
$STR = $ItemName+", ERROR: NOT Reachable"
Add-Content $TestCSVFile $STR
}
}
$AnyGap = "Yes"
IF ($AnyGap -eq "Yes")
{
$TestText = "Please check Domain Controller Auditing result."
$SumVal = ""
$TestStatus="High"
}
else
{
$TestText = " "
$SumVal = ""
$TestStatus="Passed"
}
Once the PowerShell script has finished execution you’ll see a report below “C:\Temp\AuditReport.CSV,” that contains the name of the cluster Policy Object, message and also the domain to that GPO belongs to. this is often additionally shown within the screenshot below
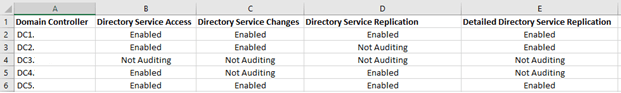
By observing the output generated by the script you’ll simply determine the domain controllers that don’t some a part of the auditing enabled. As you’ll notice, DC3.Solutionviews.com.com doesn’t have auditing enabled for “Directory Service Access,” “Directory Service Changes,” “Directory Service Replication,” and “Detailed Directory Service Replication.” equally, DC4.Solutionviews.com.com doesn’t have auditing enabled for “Directory Service Changes” and “Detailed Directory Service Replication.” This inconsistency might cause confusion if you’re trying to find a specific event on a website controller wherever the corresponding auditing isn’t enabled.
The PowerShell script was obtained from “Active Directory Domain Controller Auditing medical Test” Dynamic Pack from Dynamic Packs IT Health Profiler. Dynamic Packs IT Health Profiler is capable of reportage health on many elements of Active Directory. to urge audit configuration for all domain controllers by victimization Dynamic Packs IT Health Profiler, execute the “Domain Controller DS Audit Policy” Dynamic Pack as shown within the screenshot below:
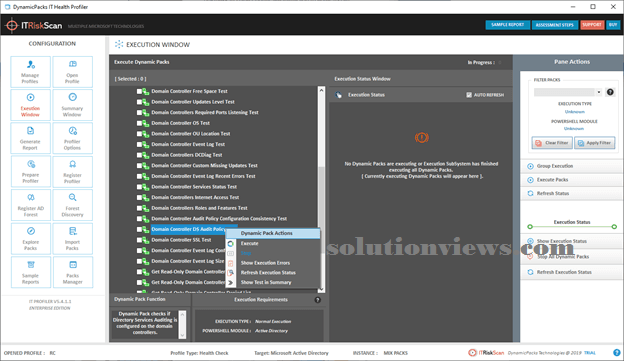
Once you’ve got dead the Dynamic Pack, you’ll visit “Summary Window” to ascertain the audit configuration settings for all domain controllers.