The Azure Ad security defaults are a collection of Microsoft-recommended identity security features. These suggestions will be enforced automatically in your business if you allow them. Identity-related threats will be better safeguarded for administrators and users. Security Defaults replace the Baseline Conditional Access settings and are free for all Microsoft 365 subscriptions.
The Azure tenant’s Security Defaults enable the following settings:
Multi-factor authentication for administrators and users (each user sign-in prompts them to configure MFA);
Old clients and outdated protocols that do not support Modern Authentication (Office 2010, IMAP, POP3, SMTP, ActiveSync), as well as connecting to Exchange Online using Remote PowerShell, are blocked from accessing Office 365 mailboxes.
When using management tools that use the Azure Resource Manager API, force MFA for privileged accounts in Azure AD (Azure Portal Access, Azure PowerShell, Azure CLI).
Security Defaults can be enabled or disabled in your Azure tenant settings:
Log in to the Microsoft Azure Portal using a Global Administrator account for an Azure or Microsoft 365 tenancy.
Select Azure Active Directory > Properties from the drop-down menu.
Click the Manage Security Defaults link at the bottom of the tenant settings page;
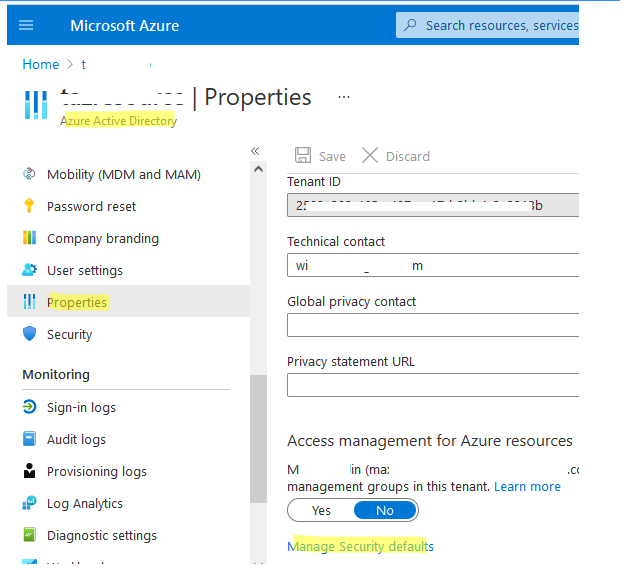
There will be only one Enable Security Defaults (Yes/No) choice available in the window. All new Azure (Microsoft 365) tenants have Security Defaults activated by default. If you want to turn off Security Defaults, choose No and complete the following Microsoft survey:
We’d want to know why you’re disabling Security settings so that we can improve.
– My company uses Conditional Access; – My company is unable to utilise important business apps; – My company is experiencing too many MFA issues; – Other.
Select the Save option;
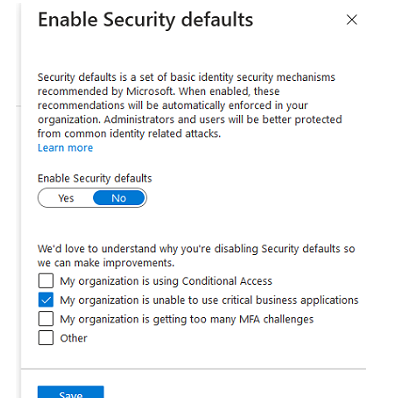
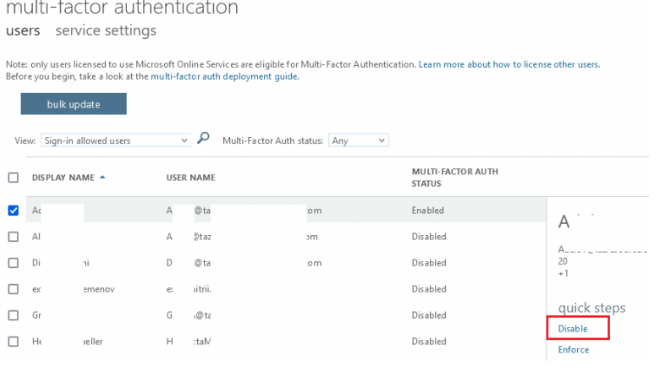
When signing in, users will no longer be requested to configure MFA. You can disable Multi-Factor Authentication if it is already enabled for some users.
Select Users > Active Users from the Microsoft 365 Admin Center (https://admin.microsoft.com/#/users); press the Multi-factor authentication button;
You must do the following to enable the use of older email protocols:
Go to https://admin.microsoft.com and fill out the form.
Choose Settings > Org Settings > Modern Authentication from the drop-down menu.
Choose which legacy protocols you want email clients to be able to utilise;
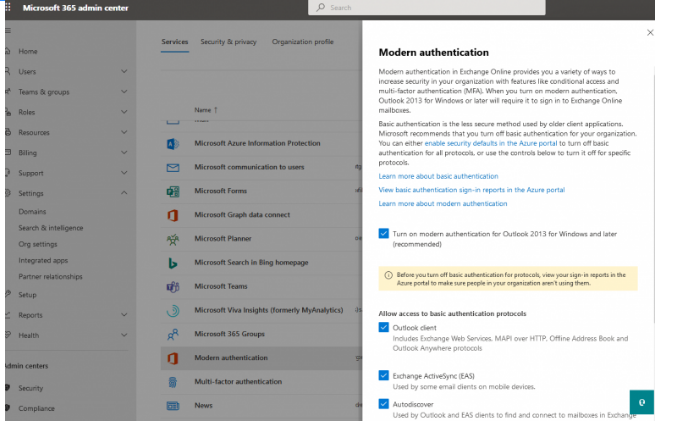
The procedures listed below are available:
Exchange Web Services, MAPI over HTTP, Offline Address Book, and Outlook Anywhere protocols are all included in the Outlook client.
Some email clients on mobile devices use Exchange ActiveSync (EAS).
Outlook and EAS clients use autodiscover to search and connect to mailboxes in Exchange Online.
POP3 — Used by POP email clients; IMAP4 — Used by IMAP email clients; IMAP4 — Used by IMAP email clients; IMAP4 — Used by IMAP email clients; IMAP4 — Used by
POP and IMAP clients use authenticated SMTP to transmit email messages;
PowerShell for Exchange Online — Used to connect to Exchange Online through remote PowerShell.
Legacy email clients will now be able to authenticate.