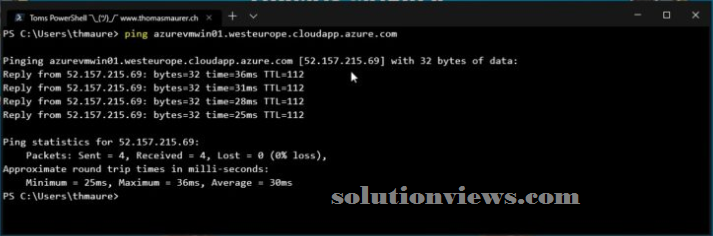
This is simply an awfully fast diary post as a result of I got the question from a few of individuals. During this diary post need to point out you ways you’ll be able to change ping (ICMP) on a public scientific discipline address of AN Azure virtual machine (VM). First, simply let Pine Tree State say that assignment a public scientific discipline address to a virtual machine is a security risk. Thus if you are doing that, confirm you recognize what you’re doing. If you wish admin access to virtual machines just for a particular time, there square measure services like Azure Just-in-Time VM Access (JIT) and Azure Bastion you ought to have a glance at. Currently back to the subject, Azure by default denies and blocks all public inward traffic to an Azure virtual machine, and conjointly includes ICMP traffic. This can be a decent issue since it improves security by reducing the attack surface.
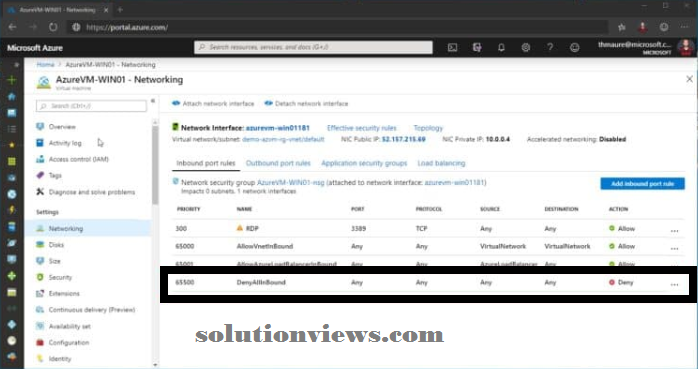
This conjointly applies to pings or ICMP echo requests sent to Azure VMs.
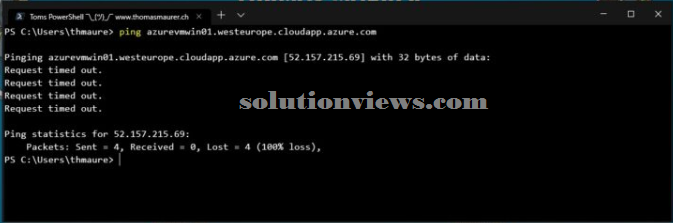
However, if you wish to access your application from a public scientific discipline address, you ought to permit the precise ports and protocols. Identical applies to the ICMP (Internet management Message Protocol) protocol. The ICMP protocol is often used for diagnostic and is usually accustomed troubleshoot networking problems. one in every of the diagnostic tools mistreatment ICMP is ping, that we have a tendency to all grasp and love.
What do I would like to try and do to be able to ping my Azure virtual machines (VMs):
Overall we’d like to try and do 2 main steps:
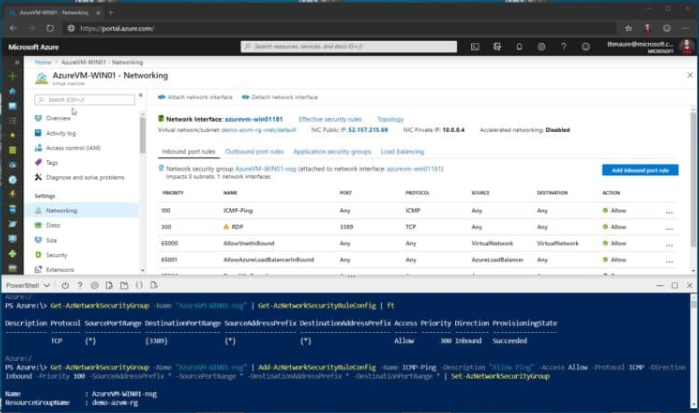
Configure the Network Security cluster (NSG) to permit ICMP traffic:
So here is however you change or permit ping (ICMP) to AN Azure VM. Click on add a replacement inward port rule for the Azure network security cluster (NSG).
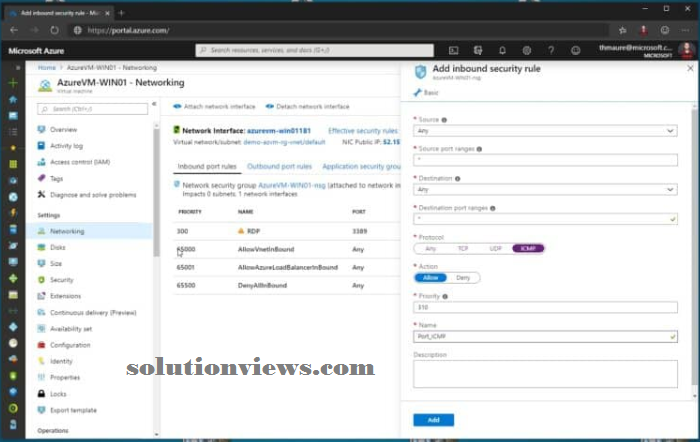
Change the protocol to ICMP. As you’ll be able to see, you’ll be able to conjointly limit the sources which might create use of that rule, yet as modification the name and outline. You’ll be able to conjointly use the subsequent Azure PowerShell commands to feature the inward security rule to your NSG.
Get-AzNetworkSecurityGroup -Name "AzureVM-WIN01-nsg" | Add-AzNetworkSecurityRuleConfig -Name ICMP-Ping -Description "Allow Ping" -Access Allow -Protocol ICMP -Direction Inbound -Priority 100 -SourceAddressPrefix * -SourcePortRange * -DestinationAddressPrefix * -DestinationPortRange * | Set-AzNetworkSecurityGroup
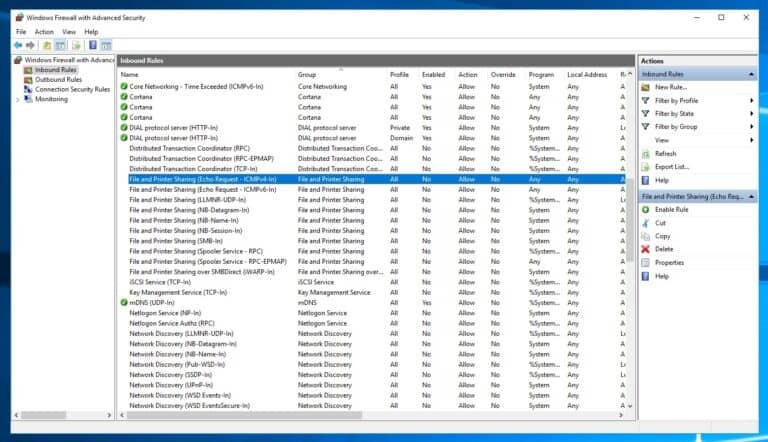
Set up the software package to answer to Ping/ICMP echo request:
If you haven’t already designed the software package that approach, you may ought to permit ICMP traffic, therefore the software package response to a ping. On Windows Server, this can be disabled by default, and you wish to piece the Windows Firewall. You’ll be able to run the subsequent command to permit ICMP traffic within the Windows Server software package. Within the Windows Firewall with Advanced Security, you’ll be able to change the Echo Request – ICMPv4-In or Echo Request ICMPv6-In rules, betting on if you wish IPv4 or IPv6.
You can conjointly run the subsequent command to try and do that:
# For IPv4
netsh advfirewall firewall add rule name="ICMP Allow incoming V4 echo request" protocol="icmpv4:8,any" dir=in action=allow
#For IPv6
netsh advfirewall firewall add rule name="ICMP Allow incoming V6 echo request" protocol="icmpv6:8,any" dir=in action=allow
After doing each step, you ought to be able to ping your Azure Virtual Machine (VM) employing a public scientific discipline address.
I hope this helps you be able to ping your Azure VMs. If you have got any queries, please let us know within the comments.

