We’ll demonstrate how to set up and use the Windows PowerShell Active Directory Module today. You may use AD cmdlets to acquire information about domain users, machines, groups, and other objects, as well as conduct AD management operations. This PowerShell module is installed as a separate feature on the server OS. The module is part of the Remote Server Administration Tools on desktop OS versions (Windows 10, 8.1, and 7). (RSAT). To administer Windows Server infrastructure, RSAT contains all necessary management tools, command-line utilities, and Windows PowerShell modules. The RSAT package for your Windows version must be downloaded from the Microsoft website (how to install RSAT on Windows 10?).
PowerShell gives administrators a lot of flexibility when it comes to working with Active Directory objects and automating tasks (this is especially useful when performing bulk actions aimed at a large number of AD objects).
In Windows PowerShell, there are three basic ways to communicate with Active Directory.
Interfaces for Active Directory Services (ADSI). This solution is the most complicated, but it works in any PowerShell installation and does not require the installation of any additional modules. It’s also “closest” to the VBScript scripting language’s controlling method of using the Active Directory Provider provided in PowerShell extensions. This method allows you to mount an Active Directory as a drive on your PC and travel across it with commands like dir, cd, and others.
Using the RSAT-AD-PowerShell module to manage Active Directory. This is the most convenient method of manipulating AD objects, but it necessitates the installation of a separate module.
To manage objects in Azure Active Directory, a different PowerShell module is used — Azure Active Directory Module for Windows PowerShell.
On Windows Server, install the PowerShell Active Directory Module.
Windows PowerShell’s Active Directory module debuted with Windows Server 2008 R2. It appears on the Windows Server after installing the ADDS role (Active Directory Domain Services) and then promoting a server to domain controller. In order to use the Active Directory module’s cmdlets, your domain must have at least one domain controller running Windows Server 2008 R2 or above. You must download and install the Active Directory Management Gateway Service if your network’s lone DC is running Windows Server 2003 or 2008. The Active Directory module’s cmdlets interface with the ADDS or ADMGS role’s web service, which is part of the domain controller.
- You can install the Active Directory module for PowerShell on the domain controller, on any Windows server or workstation;
- In Windows Server 2019/2016/2012 R2, you can install the Active Directory module for Windows PowerShell. You can do it by using the Add Roles and Features Wizard from the Server Manager. It is enough to start the wizard and at the step when selecting features, you need to select the item Remote Server Administration Tools > Role Administration Tools > AD DS and AD LDS Tools > Active Directory module for Windows PowerShell
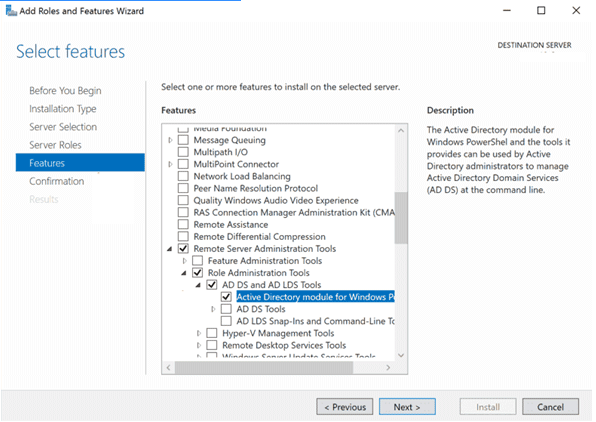
You can also install this module using PowerShell. Open the PowerShell console as an administrator and run the following commands:
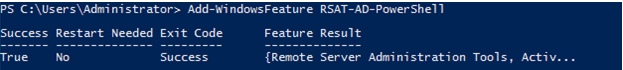
Import-Module ServerManager
Add-WindowsFeature -Name "RSAT-AD-PowerShell" –IncludeAllSubFeature
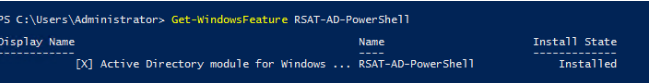
To check the installation status of a module, use the command:
Get-WindowsFeature RSAT-AD-PowerShell
Hint. If you are using the PowerShell Core 7.0 or higher, keep in mind that the Active Directory module is fully natively compatible with this version of PoSh. But first, you need to install the WindowsCompatibility module:
Install-Module -Name WindowsCompatibilityInstalling the AD PowerShell Module on Windows 10
In Windows 10, Windows 8.1, and Windows 7, to install the RSAT-AD-PowerShell module, at first you must install the appropriate version of RSAT. You can install RSAT only in the Professional, Education, and Enterprise Windows editions. The installation of RSAT on Windows Home or Single Language is not available.
- You can install the RSAT module on Windows 7, 8.1, and Windows 10 (up to build 1803) using a special MSU package which can be downloaded from the Microsoft website;
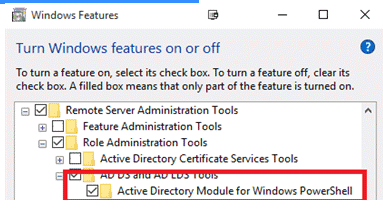
- Then you need to enable the module (Control Panel > Programs > Turn Windows Features On or Off > Remote Server Administration Tools > Role Administration Tools > AD DS and AD LDS Tools > Active Directory module for Windows PowerShell).
- Or using PowerShell:Enable-WindowsOptionalFeature -Online -FeatureName RSATClient-Roles-AD-Powershell
- On Windows 10 1809 and newer builds the RSAT became a part of Features on Demand (FoD). You can install AD RSAT Tools from the Settings menu (Settings > Apps > Manage Optional Features > Add features > RSAT: Active Directory Domain Services and Lightweight Directory Tools > Install).
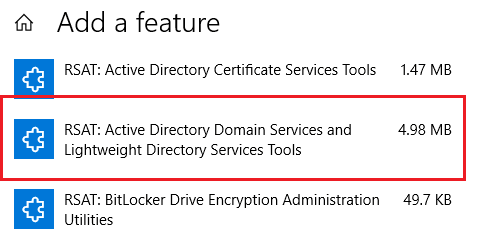
- Or from the PowerShell console:Add-WindowsCapability –online –Name “Rsat.ActiveDirectory.DS-LDS.Tools~~~~0.0.1.0”
Importing PowerShell Active Directory Module on Windows
In Windows 7 and Windows Server 2008 R2 with PowerShell 2.0 installed, to start using the Active Directory module, you need to import it into the PowerShell session with the command:
import-module activedirectory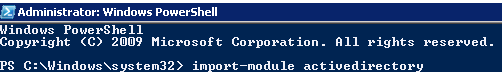
Also, you can export the module from a remote computer/server and import it into your PowerShell session (using the PSRemoting):
$S =New-PSSession -ComputerName MyDomainController
Export-PSsession -Session $S -Module ActiveDirectory -OutputModule RemoteAD
Remove-PSSession -Session $S
Import-Module RemoteADNow you can use the Active Directory module remotely without installing it on your computer.
If the AD module is installed on Windows Server 2016/2016/2012 R2 and Windows 8.1/Windows 10, it will be immediately imported into the PowerShell session.
Run the following command to verify that the AD PoSh module is installed and imported into the PowerShell session on Windows:
Get-Module ActiveDirectory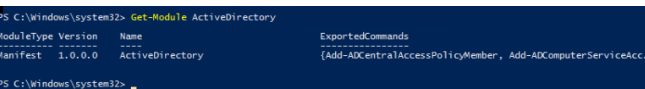
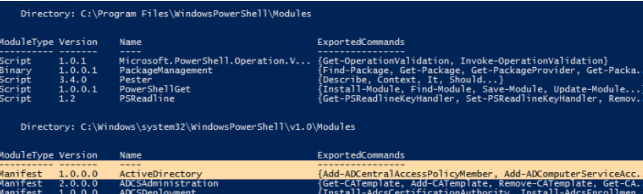
Hint. You can list all imported modules in a PowerShell session with the command:
Get-Module –ListAvailable
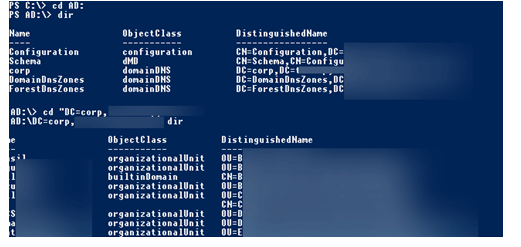
When a computer joins an AD domain, a secondary disc with the name AD: is created by default. You can traverse this disc by using the CD command and the typical methods for working with the file system. The paths are formatted in X500. You can use the AD Provider to navigate the AD as if it were a symbolic drive.
PS C:\> cd AD:
PS AD:\>
PS AD:\> dir
PS AD:\> cd “DC=contoso,DC=com”
PS AD:\> dir
You can display the list of available cmdlets for working with Active Directory as follows:
Get-Command -Module ActiveDirectory
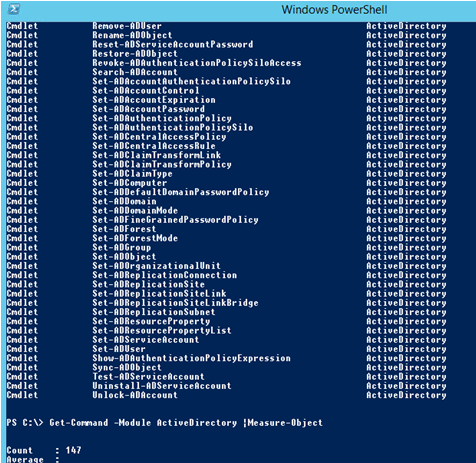
The amount of cmdlets accessible in different versions of Windows (RSAT) varies:
Windows Server 2008 R2 — 76 cmdlets;
Windows Server 2012 — 135 cmdlets;
Windows Server 2012 R2/2016 — 147 cmdlets.
The following is a complete list of AD PowerShell Module cmdlets in Windows Server 2016:
Add-ADCentralAccessPolicyMember
Add-ADComputerServiceAccount
Add-ADDomainControllerPasswordReplicationPolicy
Add-ADFineGrainedPasswordPolicySubject
Add-ADGroupMember
Add-ADPrincipalGroupMembership
Add-ADResourcePropertyListMember
Clear-ADAccountExpiration
Clear-ADClaimTransformLink
Disable-ADAccount
Disable-ADOptionalFeature
Enable-ADAccount
Enable-ADOptionalFeature
Get-ADAccountAuthorizationGroup
Get-ADAccountResultantPasswordReplicationPolicy
Get-ADAuthenticationPolicy
Get-ADAuthenticationPolicySilo
Get-ADCentralAccessPolicy
Get-ADCentralAccessRule
Get-ADClaimTransformPolicy
Get-ADClaimType
Get-ADComputer
Get-ADComputerServiceAccount
Get-ADDCCloningExcludedApplicationList
Get-ADDefaultDomainPasswordPolicy
Get-ADDomain
Get-ADDomainController
Get-ADDomainControllerPasswordReplicationPolicy
Get-ADDomainControllerPasswordReplicationPolicyUsage
Get-ADFineGrainedPasswordPolicy
Get-ADFineGrainedPasswordPolicySubject
Get-ADForest
Get-ADGroup
Get-ADGroupMember
Get-ADObject
Get-ADOptionalFeature
Get-ADOrganizationalUnit
Get-ADPrincipalGroupMembership
Get-ADReplicationAttributeMetadata
Get-ADReplicationConnection
Get-ADReplicationFailure
Get-ADReplicationPartnerMetadata
Get-ADReplicationQueueOperation
Get-ADReplicationSite
Get-ADReplicationSiteLink
Get-ADReplicationSiteLinkBridge
Get-ADReplicationSubnet
Get-ADReplicationUpToDatenessVectorTable
Get-ADResourceProperty
Get-ADResourcePropertyList
Get-ADResourcePropertyValueType
Get-ADRootDSE
Get-ADServiceAccount
Get-ADTrust
Get-ADUser
Get-ADUserResultantPasswordPolicy
Grant-ADAuthenticationPolicySiloAccess
Install-ADServiceAccount
Move-ADDirectoryServer
Move-ADDirectoryServerOperationMasterRole
Move-ADObject
New-ADAuthenticationPolicy
New-ADAuthenticationPolicySilo
New-ADCentralAccessPolicy
New-ADCentralAccessRule
New-ADClaimTransformPolicy
New-ADClaimType
New-ADComputer
New-ADDCCloneConfigFile
New-ADFineGrainedPasswordPolicy
New-ADGroup
New-ADObject
New-ADOrganizationalUnit
New-ADReplicationSite
New-ADReplicationSiteLink
New-ADReplicationSiteLinkBridge
New-ADReplicationSubnet
New-ADResourceProperty
New-ADResourcePropertyList
New-ADServiceAccount
New-ADUser
Remove-ADAuthenticationPolicy
Remove-ADAuthenticationPolicySilo
Remove-ADCentralAccessPolicy
Remove-ADCentralAccessPolicyMember
Remove-ADCentralAccessRule
Remove-ADClaimTransformPolicy
Remove-ADClaimType
Remove-ADComputer
Remove-ADComputerServiceAccount
Remove-ADDomainControllerPasswordReplicationPolicy
Remove-ADFineGrainedPasswordPolicy
Remove-ADFineGrainedPasswordPolicySubject
Remove-ADGroup
Remove-ADGroupMember
Remove-ADObject
Remove-ADOrganizationalUnit
Remove-ADPrincipalGroupMembership
Remove-ADReplicationSite
Remove-ADReplicationSiteLink
Remove-ADReplicationSiteLinkBridge
Remove-ADReplicationSubnet
Remove-ADResourceProperty
Remove-ADResourcePropertyList
Remove-ADResourcePropertyListMember
Remove-ADServiceAccount
Remove-ADUser
Rename-ADObject
Reset-ADServiceAccountPassword
Restore-ADObject
Revoke-ADAuthenticationPolicySiloAccess
Search-ADAccount
Set-ADAccountAuthenticationPolicySilo
Set-ADAccountControl
Set-ADAccountExpiration
Set-ADAccountPassword
Set-ADAuthenticationPolicy
Set-ADAuthenticationPolicySilo
Set-ADCentralAccessPolicy
Set-ADCentralAccessRule
Set-ADClaimTransformLink
Set-ADClaimTransformPolicy
Set-ADClaimType
Set-ADComputer
Set-ADDefaultDomainPasswordPolicy
Set-ADDomain
Set-ADDomainMode
Set-ADFineGrainedPasswordPolicy
Set-ADForest
Set-ADForestMode
Set-ADGroup
Set-ADObject
Set-ADOrganizationalUnit
Set-ADReplicationConnection
Set-ADReplicationSite
Set-ADReplicationSiteLink
Set-ADReplicationSiteLinkBridge
Set-ADReplicationSubnet
Set-ADResourceProperty
Set-ADResourcePropertyList
Set-ADServiceAccount
Set-ADUser
Show-ADAuthenticationPolicyExpression
Sync-ADObject
Test-ADServiceAccount
Uninstall-ADServiceAccount
Unlock-ADAccountUnlike prior tools that communicated with AD via LDAP, the AD PowerShell module communicates with a domain controller via Active Directory Web Services (ADWS). The ADWS role is installed on a domain controller during the promotion from a domain member server to a domain controller in Windows Server 2008 R2 and newer. You must install ADWS individually on Windows Server 2008 or Windows Server 2003. (included with the Active Directory Management Gateway Service).
Using RSAT-AD-PowerShell Module
PowerShell allows you to perform basic operations with the AD directory:
Get all AD properties and object attributes, modify object properties, manage AD groups, and create new directory objects, among other things.
Let’s look at some instances of how to use the RSAT-AD-PowerShell module’s cmdlets.
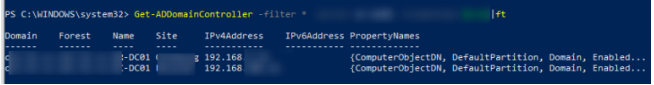
Run the command to retrieve a list of AD domain controllers.
Get-ADDomainController –filter *| format-table
You can create several AD users at once by importing the user list from CSV file Use it together with the New-ADUser cmdlet.
To get information about an AD user, use the Get-ADUser cmdlet:
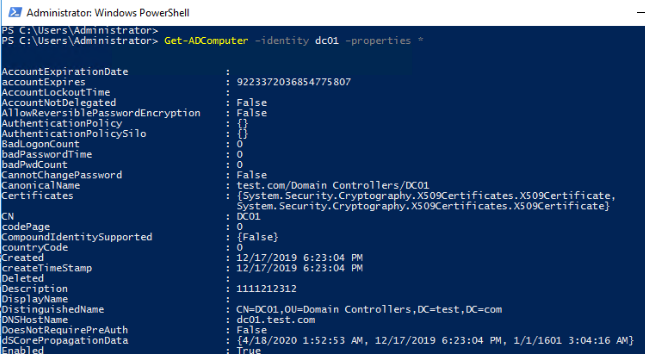
Get-ADUser –identity t.muller –properties *The similar cmdlet to display all computer attributes in AD:
Get-ADComputer –identity dc01 –properties *
To create an AD group, use the New-ADGroup cmdlet. To create a new group named ItalyUsers in a given OU, for example, run the command:
New-ADGroup -Path "OU=Groups,OU=Italy,DC=solutionviews,DC=com" -Name "ItalyUsers" -GroupScope Global -GroupCategory Distribution
To get the AD group info, use the Get-ADGroup cmdlet:
Get-ADGroup ItalyUsersIf you want to add a user or computer to an AD group, use the Add-ADGroupMember cmdlet:
Add-ADGroupMember –Identity ‘NY_Managers’ -Members s.adams,d.thumb,p.mullerUse the New-ADOrganizationalUnit cmdlet to create active directory organizational unit
New-ADOrganizationalUnit -Name "France"Use the Unlock-ADAccount cmdlet to unlock user account in active directory domain:
Get-ADUser -Identity bjackson | Unlock-ADAccountOr you can use the Set-ADAccountPassword to change or reset the user’s password:
$newPass=Read-Host "Enter the new user password" –AsSecureString
Set-ADAccountPassword bjackson -NewPassword $newPass
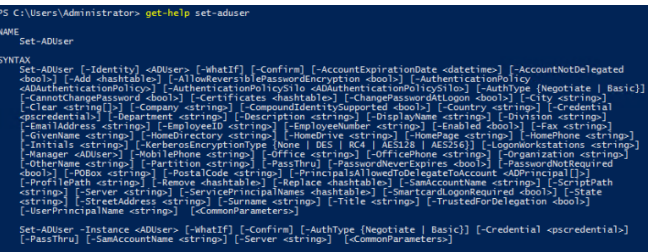
For detailed help on any cmdlet from the AD-PoSh module, use the Get-Help command:
get-help set-aduser
If the computer is not a part of the Active Directory domain, the following warning appears when you try importing the AD-PoSh module:
WARNING: Error initializing default drive: ‘Unable to find a default server with Active Directory Web Services running’.
In this case, you need to specify the AD domain controller and user credentials to connect to it.
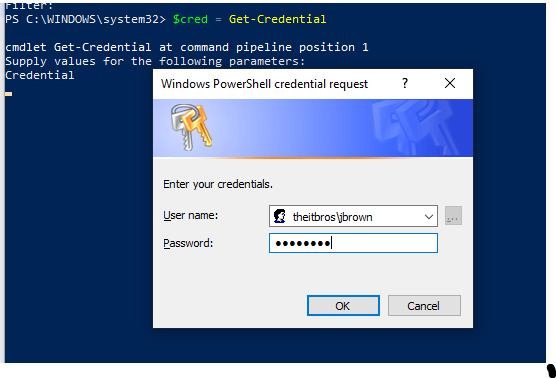
First of all, you need to get the user’s credentials to access the domain. Any authenticated domain user can view almost all AD objects properties (excluding protected Active Directory attributes).
$cred = Get-Credential
For example, to get the user’s info from the DC named TOR-DC01 under saved credentials, use the command:
get-aduser postfixsrv –server tor-dc01 -Credential $cred
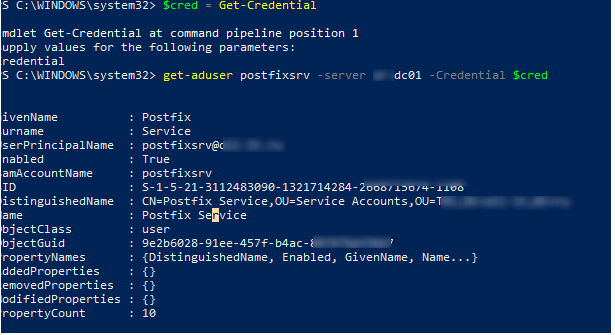
As you can see, the AD account information has been sent to you.
So now you can manage and query Active Directory using PowerShell cmdlets.