Realmd makes it simple to set up authentication and domain membership (on Active Directory or IPA/FreeIPA). The domain information is discovered automatically. SSSD is used by Realmd to validate and authenticate user accounts.
To join an Active Directory domain successfully, your CentOS server must meet the following requirements:
- Set up time synchronization with the domain controller in Active Directory (and your DC with the PDC role must synchronize time with the external NTP server). Otherwise, SSSD will not function properly. Only Kerberos is supported by this service (and cannot be used for authentication using the NTLM). As a result, the disparity in time between the DC and the Linux client should not exceed 5 minutes.
- . On Linux Centos, you must configure DNS client to use the domain controllers’ DNS service.
On CentOS, install the NTP client (chrony):
# yum install -y chrony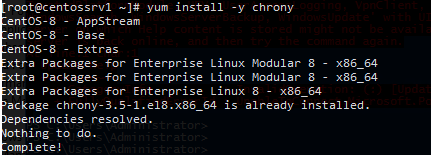
Then, in the /etc/chrony.conf configuration file, specify the FQDNs or IP addresses of the NTP servers for synchronization (these may be your AD domain controllers):
# nano /etc/chrony.conf
server dc01.test.com iburstStart the NTP service and add it to autostart:
# systemctl start chronyd
# systemctl enable chronydNow add the addresses of DNS servers that are responsible for resolving names in your Active Directory domain to your /etc/resolv.conf file:
# nano /etc/resolv.conf
search test.com
nameserver 192.168.1.201
nameserver 192.168.1.200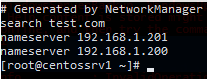
Now install the necessary packages from the CentOS repos:
# yum install adcli krb5-workstation realmd sssd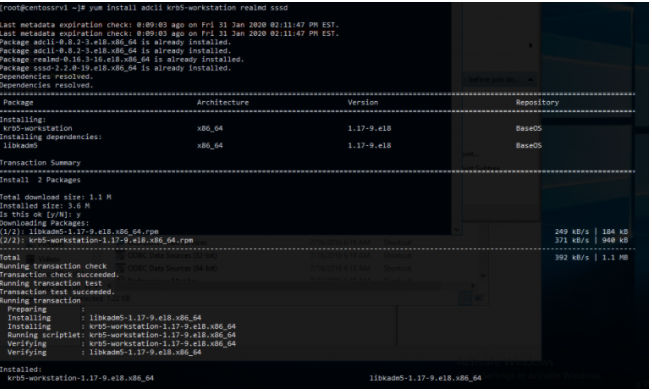
Note. If you are using another Linux distro or an older version of CentOS, make sure that the version of the SSSD package is newer than 1.9.0. Full support for AD in the SSDD appeared only since this version. In our example, sssd-2.2 is used.
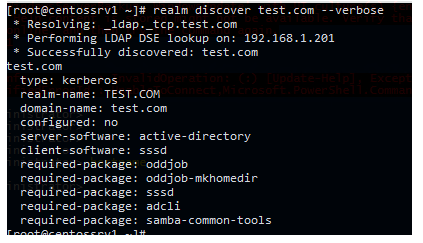
Verify that rearm tool can discover your AD domain:
# realm discover test.com --verbosIf the utility successfully detects your AD domain, the following response will appear:
* Resolving: _ldap._tcp.test.com
* Performing LDAP DSE lookup on: 192.168.1.201
* Successfully discovered: test.com
test.com
type: kerberos
realm-name: TEST.COM
domain-name: test.com
configured: no
server-software: active-directory
client-software: sssd
required-package: oddjob
required-package: oddjob-mkhomedir
required-package: sssd
required-package: adcli
required-package: samba-common-tools
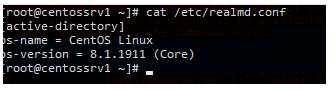
Now specify the values of the AD attributes operatingSystem and operatingSystemVersion in the configuration file /etc/realmd.conf:
# nano /etc/realmd.conf
[active-directory]
os-name = CentOS Linux
os-version = 8.1.1911 (Core)
Your CentOS server can now be added to the Active Directory domain. Use the realm join command to accomplish this. The username with permissions to add the machine to the domain and the Organizational Unit in which you want to put the account of your Linux computer were supplied in the following command.
# realm join --user=jbrion --computer-ou="OU=Servers,OU=UK,DC=test,DC=com" test.com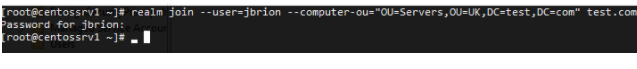
The utility will prompt you for the AD user password. After running the command, open the Active Directory Users and Computers console (dsa.msc), and make sure that the account of your CentOS server appears in the specified AD container.
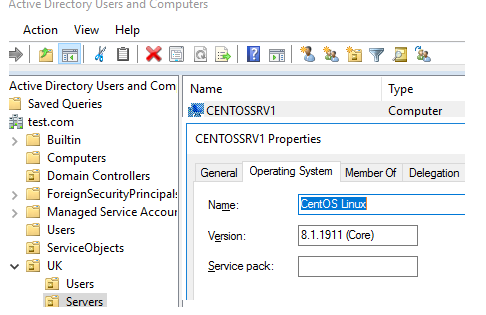
Run the realm list command and verify that the server-software: active-directory line appears. This means that this server is a member of an Active Directory domain.
In order to not to specify the full domain name when users log in, you can add the line to the /etc/sssd/sssd.conf file:
use_fully_qualified_names = False
