In our Active Directory domain, let’s say we have two Windows Server 2012 R2 domain controllers.
dc1.root.contoso.com is the primary DC, while dc2.root.contoso.com. is the secondary DC.
Following the failure of DC1, the FSMO roles must be transferred from DC1 to a backup domain controller. Then we must remove all references to the previous controller dc1.root.contoso.com from DC2.
In Active Directory, there are two ways to reassign FSMO roles:
- Transferring FSMO responsibilities — is used when a domain controller is intended to be decommissioned (for example, when a server is decommissioned) or when a DC is temporarily disconnected while performing maintenance work on a physical server.
Seizing FSMO roles — used when a physical server fails (and you don’t have an up-to-date Active Directory backup of this DC to perform a non-authoritative restore of Active Directory Domain Services) or Windows Server fails; or after you’ve forcibly demoted a domain controller to a member server using the dcpromo /forceremoval command.
Important! Before you start, ensure sure your account is a member of the Domain Admins and Schema Admins AD groups.
Connect to a DC2 and run a command prompt with elevated privileges (it is recommended to perform all steps on the domain controller, to which you want to transfer FSMO roles). Ascertain that this domain has two domain controllers:
dsquery server -forest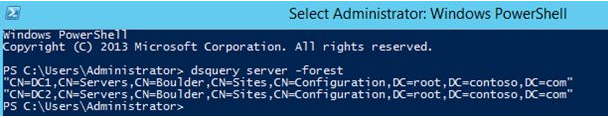
Then check which domain controller is the owner of FSMO roles:
netdom query fsmoAll FSMO roles are owned by dc1.root.contoso.com, as you can see.
All FSMO roles are allocated to the first domain controller in the forest when you create a new Active Directory domain.
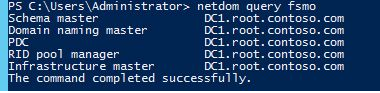
NTDSUTIL is a console utility that is used to transfer roles (ADDS service and management tool).
Administrators should exercise caution when securing FSMO roles. Only use the FSMO role as a last resort if you are unable to back up your previous DC with the FSMO role online. Don’t worry if the domain controller hosting the FSMO role is temporarily unavailable. For a day or two, your Active Directory network will function without it.
Before you transfer the FSMO roles on the additional domain controller, you must register the Active Directory schema management library. In case you don‘t, then you won‘t be able to transfer the Schema master role. In the Command prompt, run:
regsvr32 schmmgmt.dll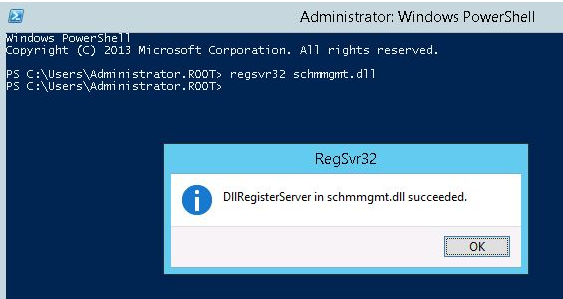
You’re now ready to take over a failed DC1’s roles. Run the following command as an Administrator at the command prompt:
ntdsutilSwitch to the role management namespace and connect to the server (DC2), which will seize the roles:
roles
connections
connect to server DC2
q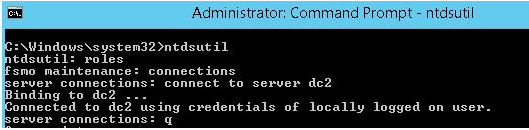
After connecting to the server DC2, seize all 5 FSMO roles:
seize naming master
seize infrastructure master
seize rid master
seize schema master
seize pdc
qDuring the seizing of each role, you will be prompted to confirm.
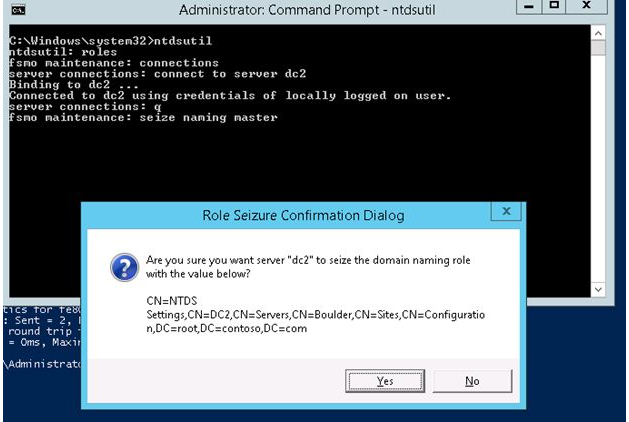
Role Seizure Confirmation Dialog
Are you want server dc2 to seize the domain naming role with the value below?
Enter the clearing of meta-data mode and connect to the server (DC2):
metadata cleanup
connections
connect to server DC2
q
List the existing Active Directory sites:
select operation target
list sites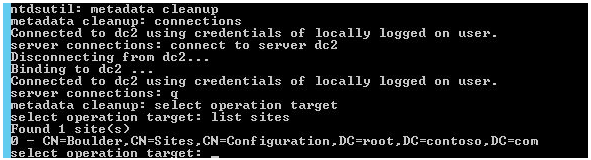
This domain has only one AD site called Boulder. Select a site, which is located on the failed domain controller DC1, and display a list of domain controllers in the site:
select site 0
list servers in site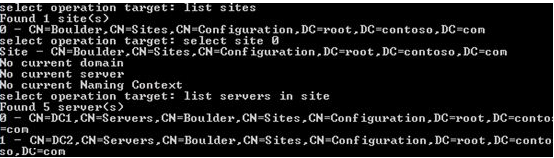
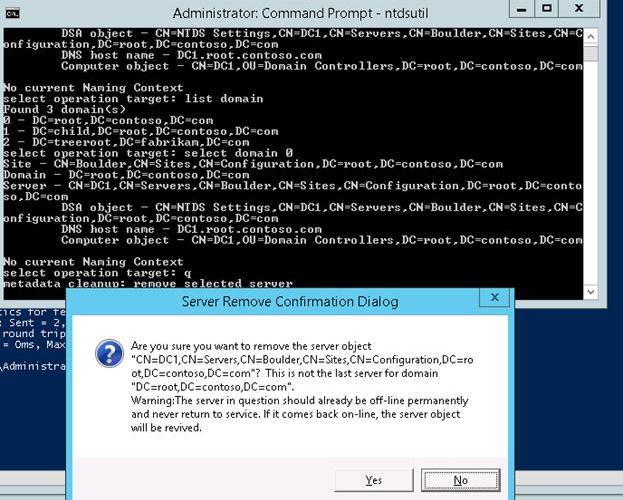
Select the failed controller (DC1) and display the list of domains:
select server 0
list domainsReturn to the metadata cleanup menu by selecting the domain:
Hint: On previous versions of Windows Server, cleaning up metadata in Active Directory is only necessary. It is sufficient to remove the domain controller account using the graphical ADUC snap-in in Windows Server 2012 R2 and newer.
select domain 0 qDelete the selected server (DC1):
remove selected serverIn the “Are you sure you want to remove the server object …“ dialog box, confirm the removal of a domain controller.
Now we must clear up the AD of any lingering entries from DC1 that has been erased.
Open the Active Directory Sites and Services snap-in from Administrative Tools > Active Directory Sites and Services (dssite.msc). Expand the site that includes the DC1 that was removed, select it, and delete it. Double-check that a DC1 has been removed.
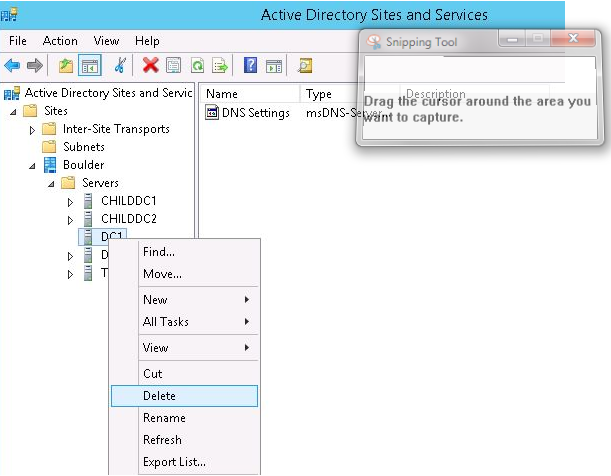
Then, under the DNS mmc snap-in (dnsmgmt.msc), delete the remaining PTR and A records from the DC1 server.
Expand “Domain Controllers” Organizational Unit in the Active Directory Users and Computers mmc snap-in (dsa.msc) (OU). Everything is good if only DC2 is displayed there. Also, if DC1 is present in that container, it must be removed from Active Directory (unlikely, but check it out).
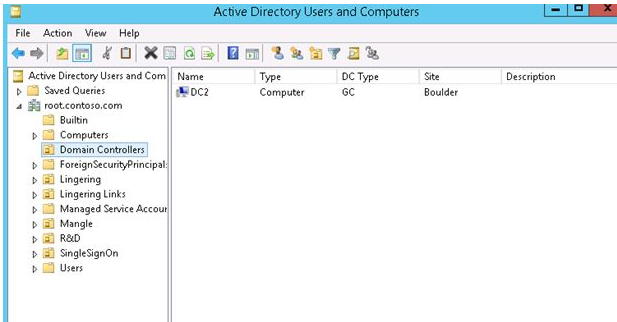
As a result, we removed the force FSMO roles from DC1 and deleted their records from DNS and Active Directory. DC2 was elevated to the position of major domain controller (the owner of all FSMO roles).
Seizing FSMO Roles Using PowerShell
The Active Directory PowerShell module has a specific cmdlet that makes securing FSMO roles more easier without having to use the ntdsutil tool. Any domain controller may be utilised to transfer or seize FSMO roles using the Move-ADDirectoryServerOperationMasterRole cmdlet.
On domain controllers running Windows Server 2008 R2 or higher, the Move-ADDirectoryServerOperationMasterRole cmdlet is available in Active Directory module 2.0 or newer.
To add the ActiveDirectory module to your PowerShell session, do the following:
Import-Module ActiveDirectory
Use the following commands to find out which DC holds the FSMO role in your AD forest:
Get-ADDomain | Select PDCEmulator, RIDMaster, InfrastructureMaster | Format-ListGet-ADForest | Select SchemaMaster, DomainNamingMaster | Format-List
The following PowerShell command is used to seize FSMO roles from the original non-operational DC to a different operational DC:
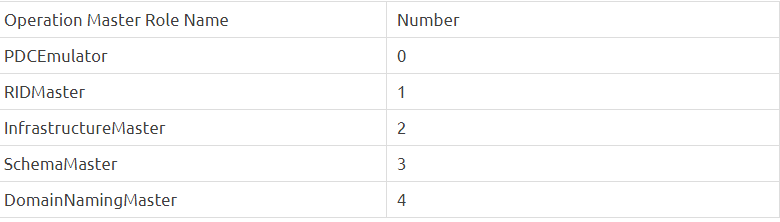
Move-ADDirectoryServerOperationMasterRole -Identity dc02 –OperationMasterRole 0,1,2,3,4 -Force- -Identity — indicates which DC the FSMO role should be assigned to.
- -OperationMasterRole — this specifies which FSMO roles should be transferred (you can use role numbers or their names from the table below)
- When the source DC is down, the -Force — option is used to seize the FSMO roles.
- To accept a role transfer, press A > Enter.
If FSMO duties are taken over, the domain controller that formerly held those roles should never come online again and communicate with the AD forest’s existing domain controller. Otherwise, a conflict will occur, potentially causing major issues in the domain.
Check the Directory Services and DNS logs in the Event Viewer for issues after capturing the FSMO roles. If you’re having trouble, use the following instructions to automatically correct the most common errors:
dcdiag /v /fix
netdiag /v /fixOnce you have completed the seize of the FSMO roles, you need to close the Command prompt, and wait for the changes to replicate throughout the AD forest. The transfer of FSMO roles from the failed domain controller is now complete.