A client account in Active Directory is being locked if the password was erroneously composed a few times in succession and surpasses the greatest number permitted by the account password strategy. In this article, we will tell you the best way to discover and open the AD record of one client or all locked AD area user immediately.
Account Lockout Policy
The limit an incentive for the quantity of endeavors to enter unacceptable password and the record licking time is characterized in the Default Domain Policy in the GPO area Computer Configuration > Windows Settings > Security Settings > Account Policy > Account Lockout Policy.
In our Active Directory domain, this policy is arranged as follows:
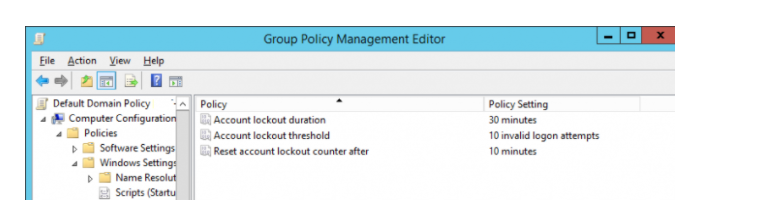
- Record lockout limit — 30 minutes;
- Record lockout length — 10 invalid logon endeavors;
- Reset account lockout counter after — 10 minutes.
For our situation, after 10 endeavors to include some unacceptable password, the client account is locked for 30 minutes. As of now, the client can’t sign in to the domain under a record with the error “1909: The referred to account is right now locked out and may not be signed on to”.
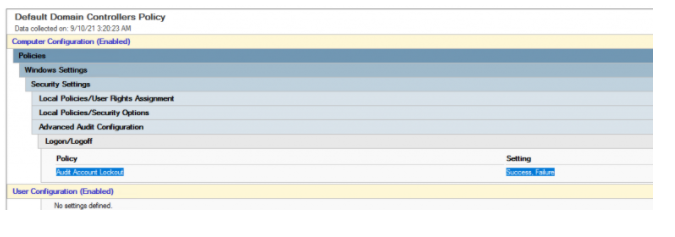
You can discover client account lockout occasions in the Security sign on a domain controller with FSMO PDC Emulator role. To do this, you need to enable inspecting of account lockout occasions in the GPO Default Domain Controller Policy.
Open the Group Policy Management Console (gpmc.msc), select the Default Domain Controller Policy, and empower the Audit Account Lockout policy (Success and Failure) under the GPO segment Computer Configuration > Policies > Windows Settings > Security Settings > Advanced Audit Policy > Logon/Logoff.
Subsequent to refreshing the GPO settings on domain controllers, when an account is locked, the 4740 occasion shows up in the Security sign in the Event Viewer:
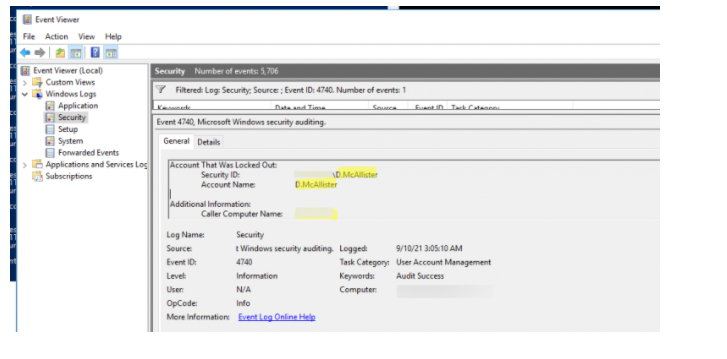
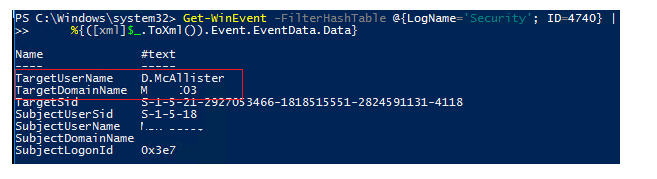
The occasion contains the locked client account name and the PC from which the lock occasion happened. The PC name is indicated in the Caller Computer Name field.
You can rapidly show the most recent lock occasions for your domain clients with PC names utilizing a straightforward PowerShell one-liner:
Get-WinEvent -FilterHashTable @{LogName=’Security’; ID=4740} | %{([xml]$_.ToXml()).Event.EventData.Data}
How to Unlock AD User Accounts Via of ADUC or PowerShell?
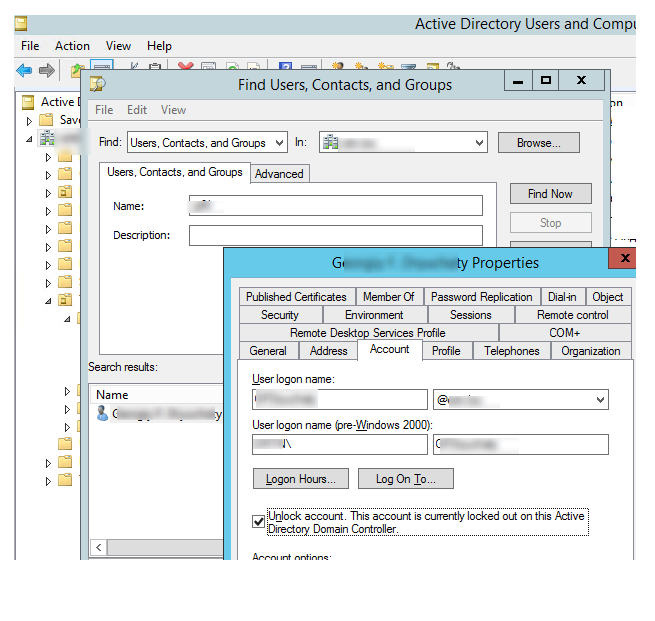
The domain administrator can rashly open the client’s account so he will not have to stand by 30 minutes. You can open a client account utilizing the Active Directory Users and Computers console (ADUC).
To open a client’s account, discover the client object in the ADUC snap-in, open its properties, go to the Account tab and check the option “Unlock Account. This account is at present locked out on this Active Directory Domain Controller” and press OK.
Nonetheless, you can unlock a client account in Active Directory a lot quicker utilizing PowerShell CLI.
To do this, you should introduce the Active Directory module for Windows PowerShell.
On Windows Server, you can install it with the command:
Add-WindowsFeature RSAT-AD-Powershell
Import the RSAT-AD-Powershell module into your session:
Import-module Active Directory
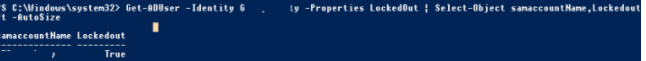
Check if the client account is locked. To do this, run the accompanying PowerShell one-liner:
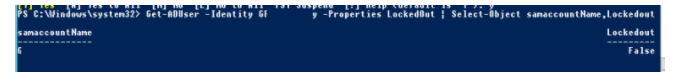
The account is locked (Lockedout=True).
Get-ADUser – Identity bjackson – Properties LockedOut | Select-Object samaccountName,Lockedout| ft – AutoSize
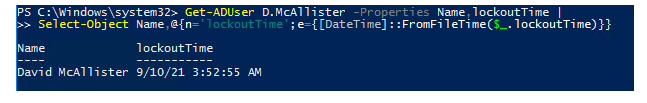
The client lock time can be seen in the worth of the lockoutTime client quality:
Get-ADUser D.McAllister – Properties Name,lockoutTime |
Select-Object Name,@{n=’lockoutTime’;e={[DateTime]::FromFileTime($_.lockoutTime)}}
To open a client account, you can utilize the cmdlet:
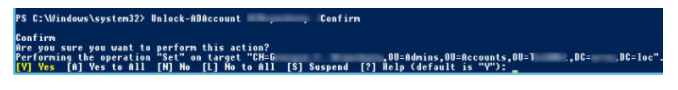
Unlock ADAccount bjackson – Confirm
Press Y to affirm the Unlock of the account, then, at that point Enter.
You can likewise utilize the accompanying order:
Get-ADUser – Identity bjackson | Unlock-ADAccount
Get-ADUser – Identity bjackson – Properties LockedOut | Select-Object samaccountName,Lockedout
Presently the client can sign in to the domain PC or server under his account.
You can rapidly discover all secured client accounts in the domain. Utilize this PowerShell command:
Search-ADAccount -lockedout | Select-Object SamAccountName, LastLogonDate, LockedoutHow to Delegate Permissions to Unlock Accounts in Active Directory?
You can delegate to non-administrator client permission to unlock AD accounts. To do this:
- Make another allowUnlockAccount security group in the domain;
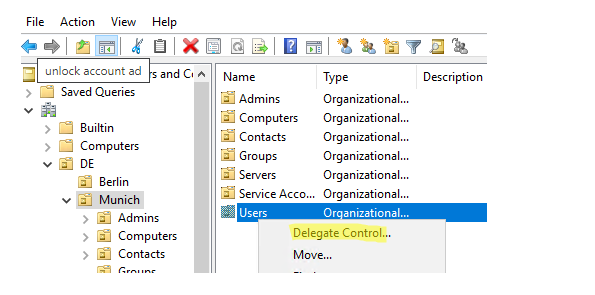
- Open the ADUC console and right-click on the clients’ OU;
- Select the item Delegate Control;
4. Click Add and select the allowUnlockAccount group. Click Next;
5. Select Create a custom undertaking to designate > Only the following object in the folder > User objects;
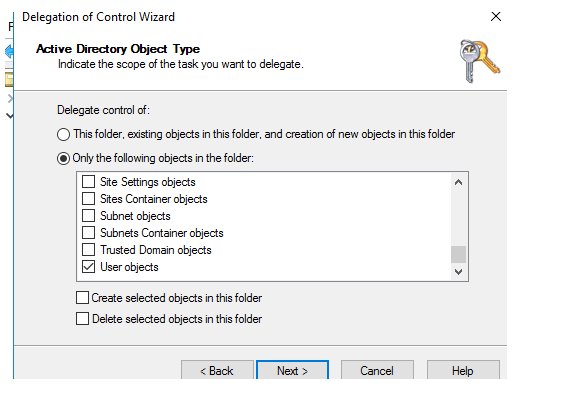
6. Select Property-specific and check two permissions in the list: Read lockoutTime and Write lockoutTime;
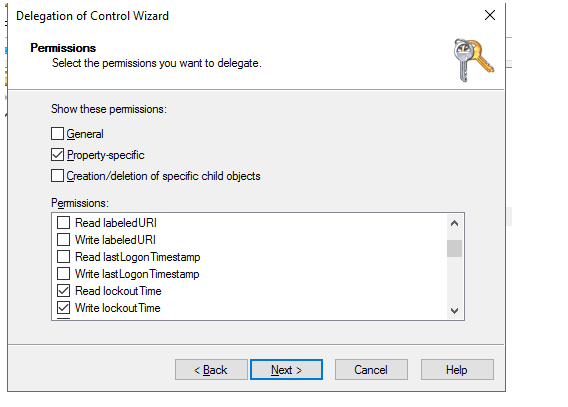
7. Save your changes.
Clients in the allowUnlockAccount gathering would now be able to unlock account from the selected OU utilizing the ADUC console or the Unlock-ADAccount PowerShell cmdlet.
To get data concerning who opened a client, you need to empower the Audit User Account Management strategy for domain regulators (Computer Configuration > Policies > Windows Settings > Security Settings > Advanced Audit Policy Configuration > Audit Policies > Account Management).
After refreshing the GPO, you can channel the Security Log by the Event ID 4767 (A client account was unlocked) to distinguish the client who opened the AD account.