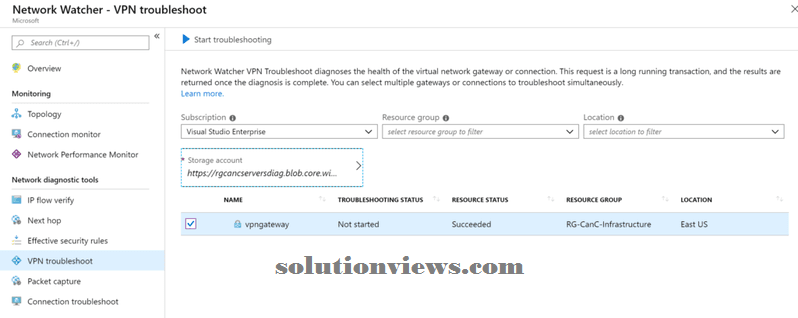
VPN and affiliation troubleshoot:
When troubleshooting hybrid cloud, the virtual network entryway part is significant to know what’s occurring between Azure and on-premises. once victimization VPN troubleshoot, the cloud administrator must choose a Storage Account and a instrumentality then choose one or a lot of network gateways. at the moment simply click on the beginning Troubleshooting button.
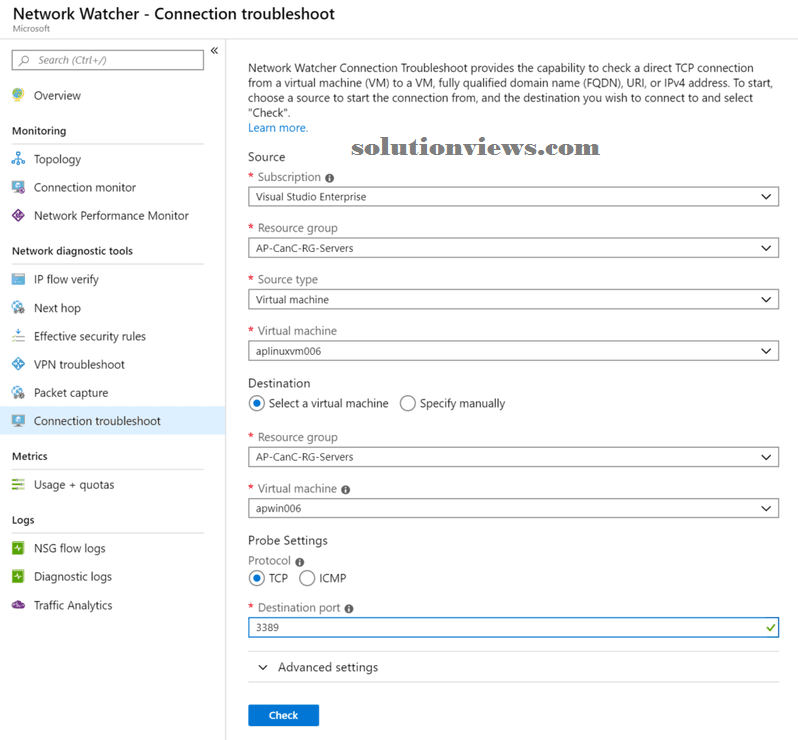
In the affiliation troubleshoot item, we will choose and opt for 2 VMs in our Azure for supply and target. Associate agent extension is needed, and it’ll be put in as a part of the method. The response of this tool is amazing, and it provides loads of knowledge that may facilitate the cloud administrator establish the foundation reason for the property issue. The tool shows the VMs, their informatics addresses, Next Hop, the numbers of a search sent and unsuccessful, in addition as topology read.
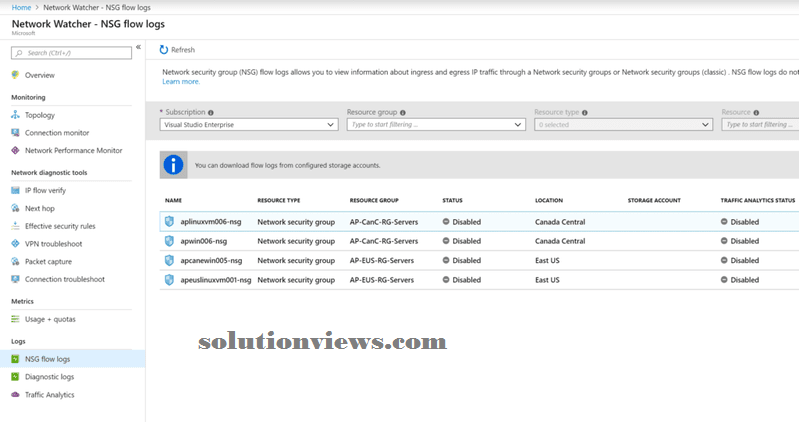
Logs section in Network Watcher:
To alter Traffic Analytics, we want to start out by enabling NSG flow logs. The method is straightforward. Click on NSG flow logs item on the left aspect, and an inventory of Network Security teams are going to be listed. Click on the required NSG.
An NSG will have flows (status column) being designed and conjointly Traffic associatealytics standing (Traffic Analytics standing column). We will see at a look all the Network Security teams and their current configuration while not the requirement to ascertain individual properties.
In the new blade, we will alter the flow logs and choose that version. Each versions log egress informatics traffic for each styles of traffic, that area unit allowed or denied. Version two adds bytes and packet to the combination.
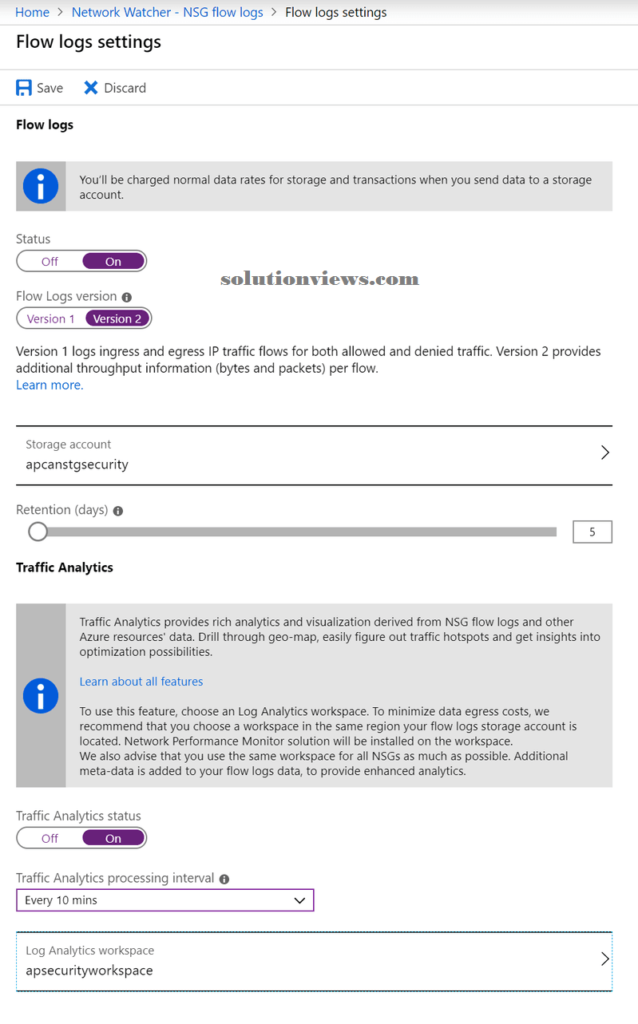
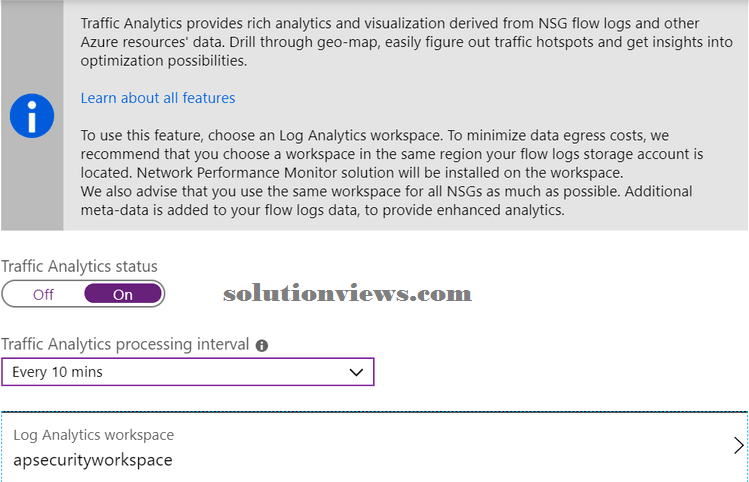
For the flows, we want to outline the retention in an exceedingly variety of days and storage account. For the Traffic Analytics, we want to see the frequency (1 hour or ten minutes) and therefore the Log Analytics that’s getting to be used.
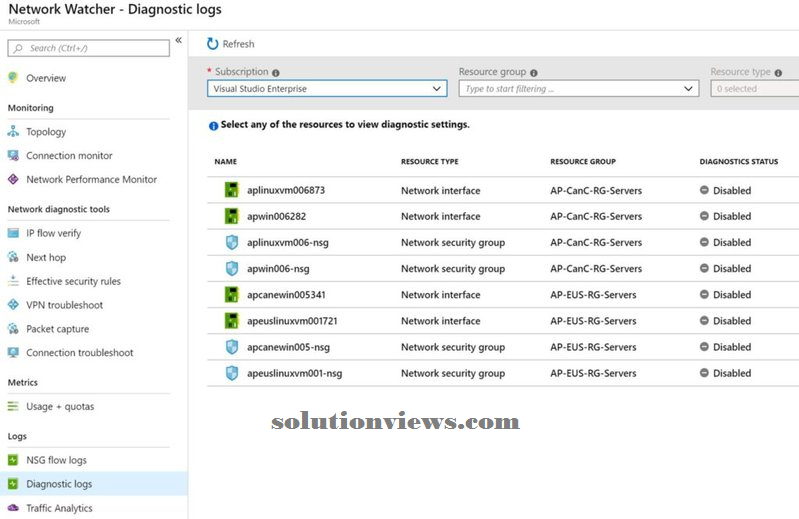
The other part of this space is nosology Logs, and it’ll list all network parts on the chosen subscription. We will slim down by resource cluster and resource sort.
Note: If you utilize Azure Monitor to put together diagnostic settings, you’ve got a similar interface, however the distinction is that Network Watcher lists all network-related resources in an exceedingly single location.
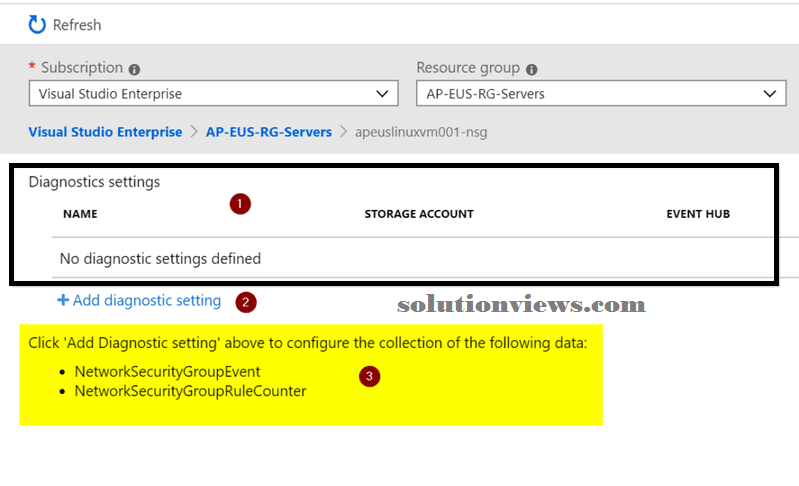
When we click on any of the resources that we wish to alter nosology, a replacement blade are going to be displayed. At first, it looks like an easy and annoying page that needs an extra click, however there are unit some delicate details on that. Here may be an outline of what’s accessible on this straightforward page:
We can see any existing diagnostic settings already designed for this resource (Item 1).
We can set a replacement diagnostic setting entry (Item 2).
We can check all attainable settings accessible even before you are attempting to feature a diagnostic setting (Item 3).
Keep in mind that diagnostic logs will send log data to event hubs, storage or log analytics. We will have quite one diagnostic log entry per resource. If you’re thinking that that the method is tedious victimization Azure Portal, you’ve got many choices to manage diagnostic logs, here are a unit a couple of choices available:
Use scripting (PowerShell or Azure CLI) when the actual fact.
Define the diagnostic log settings throughout the ARM example readying method.
Use Azure Policies to enforce/enable settings.
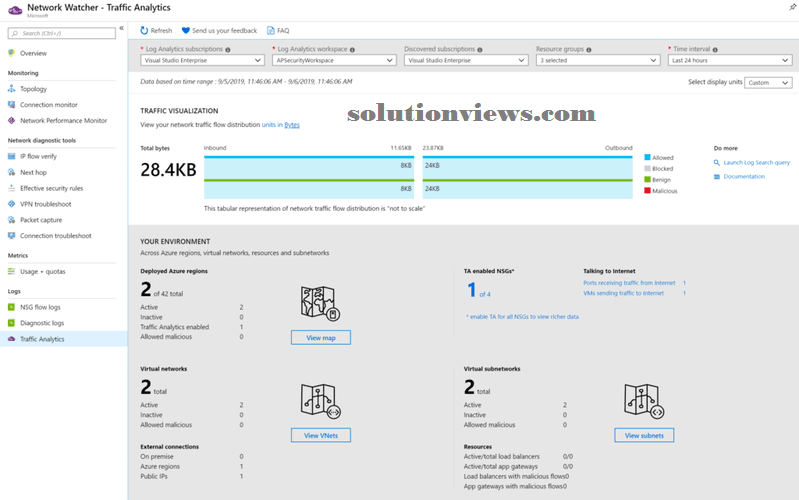
Time to explore Traffic Analytics. The initial page contains a prime bar wherever we want to pick out the log analytics that’s being employed by the Traffic Analytics (we outlined that within the NSG flows) and therefore the interval. The initial page has many sections, as follows:
- Traffic image.
- Your setting.
- Traffic distribution.
- Network Security teams hits
The traffic image section provides a graphical read of the network traffic flow distribution (in Item one, we will choose from bytes and flows). We tend to even have a little section referred to as “do a lot of,” wherever we’ve got a link to the log search (log analytics) and therefore the documentation.
The “your environment” section is that the outline of all objects, together with Azure regions, virtual networks, VPN gateways, Network Security teams, and subnet. All of them have links that may bring interactive dashboards.
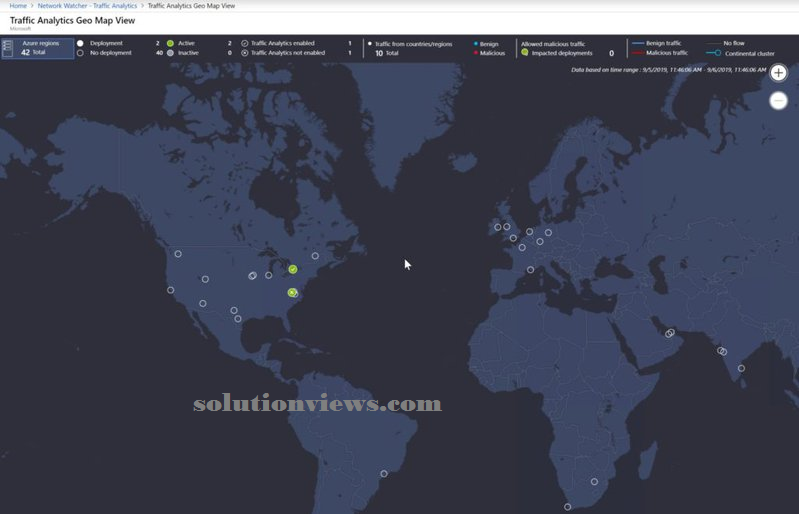
My favorite feature is that the Geo Map, that provides the world map. The administrator will choose choices from the highest bar and therefore the map can modification interactively. We will see the Azure regions, traffic supply by country/region, color-coded to spot if the traffic is benign or malicious. All points within the map permit the administrator to hover the mouse over and click on them to retrieve a lot of data.
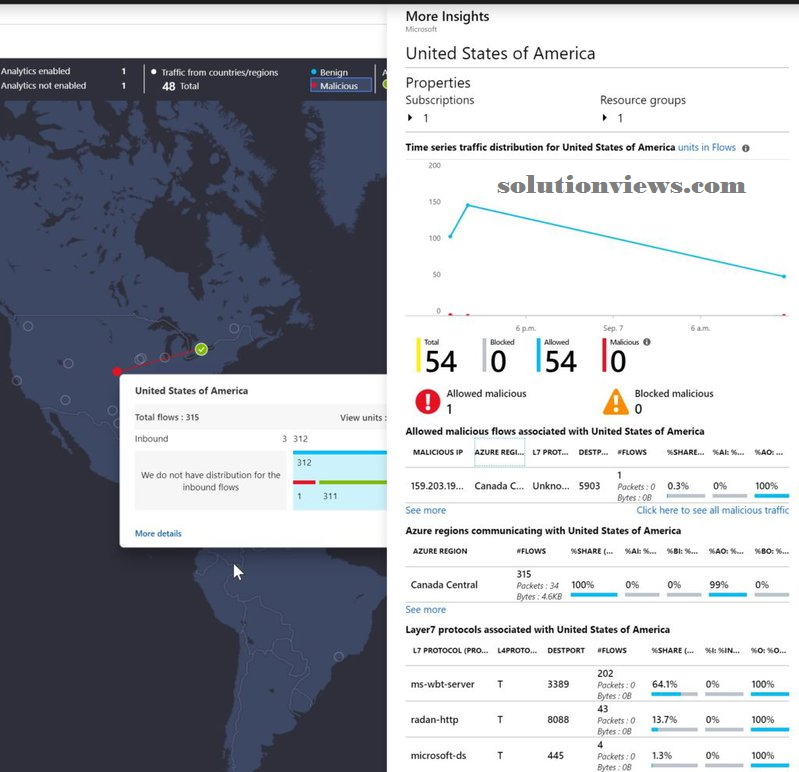
By clicking on one in all the links accessible on the map, we’ll have access to a range of knowledge. Within the example below, we tend to click on one supply informatics and from that initial window; we tend to get a lot of insights into the U. S. traffic to our readying in Canada Central region. We tend to were ready to see the malicious informatics, variety of flows, Layer seven data, then forth.
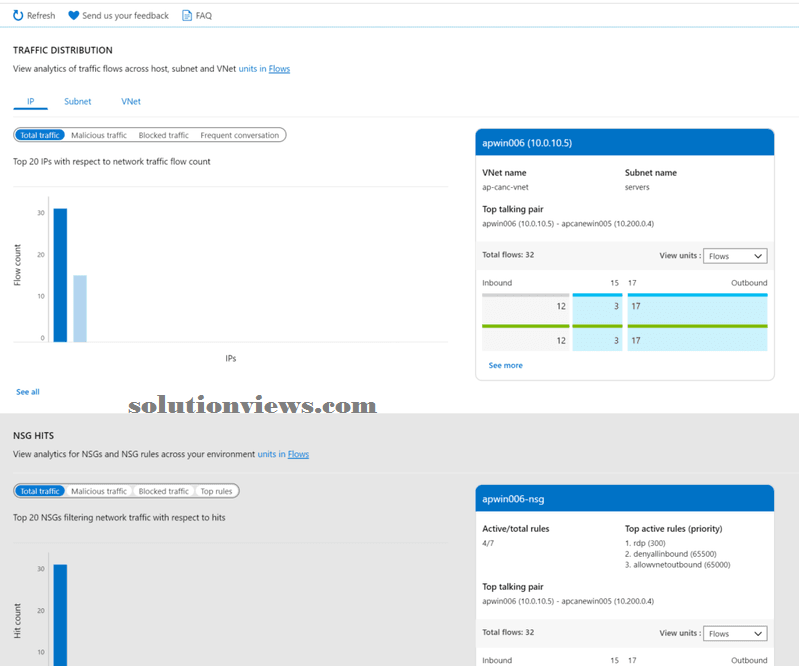
In the traffic distribution section, we will have interactive graphics of many styles of traffic (total, malicious, blocked, and frequent). We will conjointly see the numbers per informatics, subnet, and virtual web work net.
In the NSG hits section, {we can we will we area unit able to} check however the Network Security teams and its rules knowledge are being effective. The highest active rules are going to be displayed mechanically on the proper aspect.
Traffic Analytics: A key a part of your Azure network:
In this second article, we tend to coated Traffic Analytics, that helps to spot potential risks and perceive what’s occurring the network piece of the Azure readying. We tend to conjointly coated 2 alternative tools: the VPN and affiliation troubleshoot.