Introduction:
In my last article here I delineate intimately a way to implement a client-based remote access VPN resolution victimization Windows Server 2012 R2. The article lined preparation of the sever and initial configuration of the Routing and Remote Access Server (RRAS) service to support client-based remote access VPN connections. However, the initial configuration is somewhat incomplete and not entirely secure nonetheless.
Remote Access Protocols:
RRAS VPN in Windows Server 2012 R2 supports the subsequent remote access protocols.
PPTP – The Point-to-Point Tunneling Protocol has been around since the start of your time it looks. It needs no further configuration and works right out of the box. Because it is absolutely easy to deploy and supported by nearly all VPN purchasers, it’s in wide use nowadays. However, PPTP in its default configuration in Windows RRAS is basically insecure. In fact, while not further configuration, communication that takes place over PPTP ought to be thought-about to unprotected.
L2TP – The Layer 2 Tunneling Protocol has conjointly been around a protracted time and is usually deployed to supply higher security and protection than PPTP offers. L2TP is best deployed victimization certificates for authentication. However, it conjointly supports authentication victimization pre-shared keys (passwords). This can be the foremost common preparation model and one that works moderately well for many organizations.
SSTP – The Secure Sockets Tunneling Protocol may be a comparatively newcomer to remote access. It uses communications protocol as a transport tunnel protected with Secure Socket Layer (SSL) and Transport Layer Security (TLS) coding. SSTP was initial introduced in Windows visual image SP1 as is enclosed altogether supported Windows operative systems nowadays. SSTP is a superb selection once supporting Windows remote access purchasers completely. The advantage of victimization SSTP is that it’s easy to put together and is firewall friendly, as outward-bound protocol port 443 is usually hospitable the general public net.
IKEv2 – the net Key Exchange version a pair of protocol may be a fashionable remote access protocol that’s secure and resilient. It includes support for Network Address Translation (NAT) traversal, permitting the protocol to taste a footing device playacting NAT. It conjointly includes increased quality support with session commencement, sanctionative remote connections to drop intermittently while not terminating the session and prompting the user to reconnect. This eliminates the requirement for a user to enter their credentials every time their association drops off momentarily, which regularly happens once victimization unreliable connections or change Wi-Fi access points once roaming.
Disable PPTP:
For security reasons it’s suggested that the PPTP protocol not be enabled on a Windows Server 2012 R2 VPN server. To disable PPTP, open the Routing and Remote Access management console, expand the VPN server, and so right-click Ports and opt for Properties. Highlight WAN Miniport (PPTP) and click on put together.
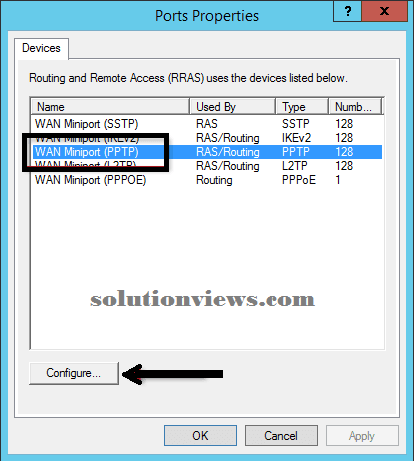
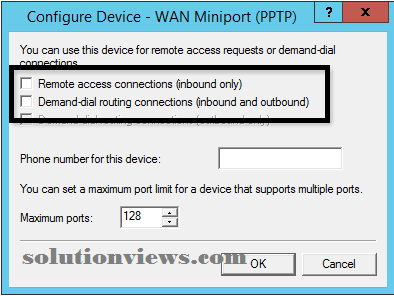
Uncheck the boxes next to Remote access connections (inbound only) and Demand-dial routing connections (inbound and outbound) and click on OK and Apply.
Configure SSTP:
To put together the SSTP protocol, right-click the VPN server within the Routing and Remote Access management console and opt for Properties. Choose the safety tab and opt for the SSL certificate from the Certificate drop-down list and click on OK.
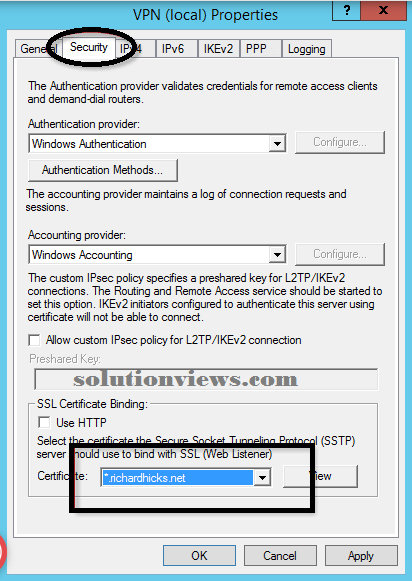
Note:
It is suggested that the SSL certificate be issued by a trustworthy public certification authority (CA). AN SSL certificate will be issued by an enclosed Public Key Infrastructure (PKI) as long because the Certificate Revocation List (CRL) is out there in public. Additionally, the SSL certificate should be put in within the native pc certificates store. Make sure to import the personal key, in conjunction with any intermediate certificates provided by the CA. Finally, make sure that the topic name on the SSL certificate matches the general public hostname that purchasers can use to attach to the VPN server remotely. Multi-SAN and wildcard certificates area unit supported.
When configuring SSTP, the changes need that the RRAS service be restarted. Click affirmative to continue.
Configure L2TP:
Note:
It is suggested to use certificate authentication for L2TP for the best level of security. However, careful steering for configuring certificate authentication with L2TP is outside the scope of this text. A lot of data on configuring certificate authentication will be found here.
To put together the L2TP protocol employing a presaged key, right-click the VPN server within the Routing and Remote Access management console and opt for Properties. Choose the safety tab and check the box next to permit custom IPsec policy for L2TP/IKEv2 Connections. Enter a presaged key and click on OK.
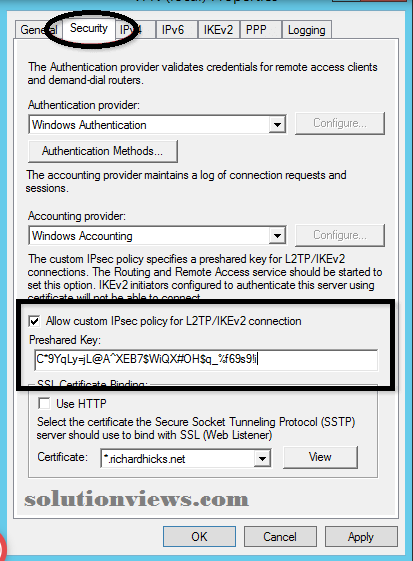
When configuring L2TP, the changes need that the RRAS service be restarted.
Click affirmative to continue.
Configure IEv2:
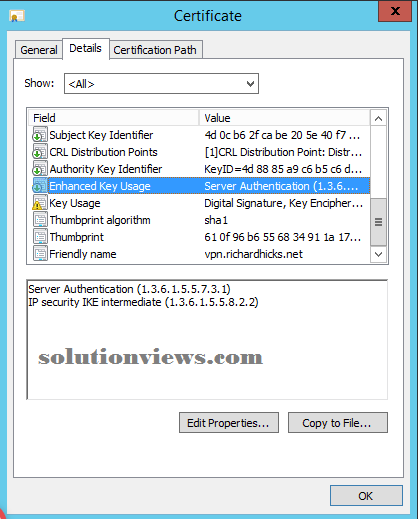
IKEv2 needs a certificate to be issued to the VPN server by an enclosed PKI. The certificate should be put in within the native pc certificates store and should embrace the Server Authentication (1.3.6.1.5.5.7.3.1) increase Key Usage (EKU). To avoid potential problems associated with certificate choice on the shopper facet for IPsec, it’s suggested that the certificate conjointly embrace the science security President intermediate (1.3.6.1.5.5.8.2.2) EKU.
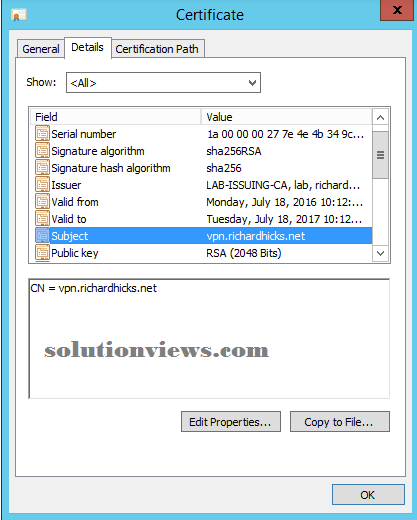
In addition, the topic name on the certificate should match the general public hostname utilized by purchasers to attach remotely to the VPN server. the topic name should NOT be the VPN server’s hostname. for instance, if the server’s hostname is RRAS01, however purchasers on the general public net use the FQDN vpn.example.com to resolve the general public science address of the VPN server, then vpn.example.com ought to be designed because the subject name for the certificate.
Additional Security issues:
After disabling PPTP and sanctionative support for L2TP, SSTP, and IKEv2, the safety of remote VPN connections is improved greatly. However, there area unit some further steps that ought to be taken to confirm the best levels of security and protection for remote purchasers.
The SSTP remote access protocol depends on SSL and TLS for authentication and coding of knowledge from remote purchasers. The default configuration of SSL and TLS in Windows isn’t ideal. Additionally, SSL and TLS security may be a moving target and may be evaluated on a daily basis. It’s suggested to check the VPN server’s SSL and TLS configuration victimization the Quays SSL Labs Server check web site. Right any findings uncovered by the check.
The use of robust user authentication is extremely suggested for VPN connections. The configuration of multifactor authentication for VPN is outside the scope of this text. However, integration a multifactor authentication resolution on-premises or cloud-based like Microsoft Azure Multifactor Authentication is a superb thanks to improve the security posture of the remote access resolution.
Final Thought:
After playacting the initial installation and configuration of the RRAS service on Windows Server 2012 R2, the VPN server was solely designed to support PPTP. Whereas purposeful, this configuration wasn’t fascinating for a spread of reasons. First, PPTP is inherently insecure. Second, none of the fashionable, a lot of sturdy, and secure remote access protocols were designed. Following the steering during this article, the VPN server is currently way more secure. additionally, it currently provides support for a broader vary of purchasers, together with Windows PCs, Macs, Linux, iPhone, Android, Windows Phones and tablets, and far a lot of.
