The ldapsearch utility is one of the most significant tools for LDAP (Lightweight Directory Access Protocol) server administrators. It allows you to retrieve any data stored in the LDAP directory. OpenLDAP and Microsoft Active Directory are currently the most popular LDAP implementations. Currently, the ldapsearch program is primarily used on Linux platforms. The Ldapsearch.exe utility was available in Windows 2000, but it was replaced by the dsquery tool in Windows Server 2003. However, you may still use the Ldapsearch tool on Windows by downloading and installing the OpenLDAP client for Windows (by default the ldapsearch is located in the C:\OpenLDAP\bin directory).
Consider the ldapsearch tool’s syntax:
ldapsearch [options] [filter] [attributes]- -n — display actions that will be performed, but not run them;
- -v — verbose, detailed operation mode;
- -A — display attributes only, without values;
- -L (-LL, -LLL) — output format (-L – LDIFv1, -LL – disable comments display, -LLL — disable LDIF version display).
- -x — use plain authentication, not SASL;
- -D — use the username to connect to the server;
- -w [password] — specify password in the command prompt when running LDAP query;
- -h — LDAP server address;
- -p — LDAP server port;
- -b — search start directory;
- -s[base|one|sub] — searchScope:
- -l — timelimit at the search time;
- -z — sizelimit on the data size in the search query result;
- -Z — use TLS.
Let’s try to connect to an Active Directory domain controller using the ldapsearch programme in Linux Debian (target LDAP server).
Domain configurations for Active Directory:
- AD domain name — solutionviews.com;
- FQDN name of the domain controller — dc1. solutionviews .com;
- The AD username that is used to connect to the LDAP: TestLDAPConnUsr and its password — P@ssw0r6; First of all, make sure that the OpenLDAP client is installed on your system:
dpkg -l | grep ldap
Check for the LDAP account ADUser1 in the container with the DN name “OU=Users,OU=London,OU=UK,DC= solutionviews ,DC=com”.
An LDAP server typically accepts incoming connections on port 389 using TCP or UDP protocols. LDAP servers with SSL use port 636.
To check the LDAP connection (TCP port 389), run the command:
ldapsearch -v -x -D "TestLDAPConnUsr@solutionviews.com" -w "P@ssw0r6"
-b "OU=Users,OU=London,OU=UK,DC=solutionviews,DC=com" -H "ldap://dc1.solutionviews.com" sAMAccountName= ADUser1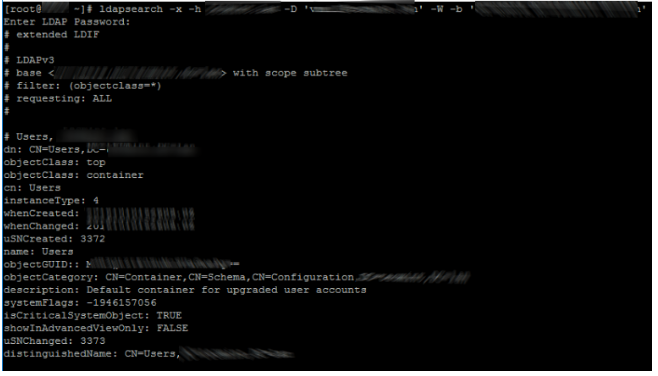
In this situation, ADUser1’s user credentials are sent across the network in clear text, which is not safe.
Over the secured LDAPS protocol, you can connect to an LDAP that uses an SSL certificate (TCP port 636). Create a file with your domain CA’s root certificates in PEM format and Base-64 encoded (for example, /etc/ssl/cert/solutionviewscert.pam) and indicate the path to it in the OpenLDAP client configuration file (/etc/ldap/ldap.conf or /etc/openldap/ldap.conf),
#TLS_CACERT /etc/ssl/certs/ca-certificates.crtTLS_CACERT /etc/ssl/certs/solutionviewscert.pamNow execute the LDAPS query:
ldapsearch -v -x -D "TestLDAPConnUsr@solutionviews.com" -w "P@ssw0r6"-b "OU=Users,OU=London,OU=UK,DC=solutionviews,DC=com" -H "ldaps://dc1.solutionviews.com" sAMAccountName= ADUser1If you entered an incorrect username or password to connect to LDAP, the utility will return:
ldap_bind: Invalid credentials (49)
additional info: Simple Bind Failed: NT_STATUS_LOGON_FAILUREYou can list all users in a specific LDAP directory:
ldapsearch -xLLL -D "TestLDAPConnUsr@solutionviews.com" -w "P@ssw0r6" -H "ldaps://dc1.solutionviews.com" -b "OU=Users,OU=London,OU=UK,DC=solutionviews,DC=com"To search by username:
ldapsearch -W -x --"TestLDAPConnUsr@solutionviews.com" -b "OU=Users,OU=London,OU=UK,DC=solutionviews,DC=com" "(uid=user1)"
Use the command to list all user accounts except disabled users:
ldapsearch -x -D "TestLDAPConnUsr@solutionviews.com" -b "dc=example,dc=com-H "ldaps://dc1.solutionviews.com" -W '(&(proxyAddresses=smtp*)(!(userAccountControl:1.2.840.113556.1.4.803:=2)))'