Protocol file (log file) is expanding rapidly and is occupying storage space:
You may come across the problem of increasing database size due to rapid log file growth.
It could be our mail system exchange or SQL (structured query language) database.
To reduce the log growth, follow some steps which are as follows,
- Turning on or checking circular logging but this is nor suggested by Microsoft office.
- Enhancing the diagnostic logging to find out the reason behind the rapid increase in log file by using event ID.
Detailed process:
Exchange works as to write all the dealings in the protocol files or log files first and then entrust them to data bank whenever is allowed by the system.
Dealing or the transaction can include anything. For example:
Mailbox: Inbox, Outbox, Sent
Increase in transaction journal mainly is due to the expansion of trade-off databases.
Knowing the reason of increase, now we will address the fact that why this abnormal expansion of exchange of databases is occurring
Many of us are not fond of reasons or finding one but it could be very helpful to segregate and settle such problems.
The main cause behind this problem could be one of the following:
Mailbox:
- Mailbox or database corruption.
- Syncing problems
- Misbehaving client or corrupted profile
- Anyone trying to hack or access any specific mailbox
Mail flow:
- Non delivery report or NDR swirling
- Brochures or mail shots or junk.
- Enhanced transaction of mails.
- Any corrupt mail or file been stuck.
Conclusion: the transaction journal growth is majorly due to repeating of the transactions.
How to find out log file growth?
- The tool Exmon is used for tracing the growth of log file. Install Exmon to identify logs.
A user who use CPU(%) greater than 50% than the problem is clear and you have already found it.
Ask the user to quick any client/client activity, or if not possible reach them disable the account for some time..
Keep an eye on your transactions and logs.
- Verification of variables like mail bank should be done by your exchange server ( when you don’t know the database.)
Let’s discuss about using the tool called ExMon and how to use it and download it.
There are many types of this tool but we will talk about some of them in this article which are used for tracking down and recognizing the protocol file growth.
The tools are:
- ExMon
- Strings.exe
- Netmon
Installation and working of the tools:
ExMon its installation and usage:
Installation:
Download ExMon from Microsoft Exchange Server User Monitor
- Select Download or install ExMon.
- Then save the file and click on the option “Run” from the 2 showed below.
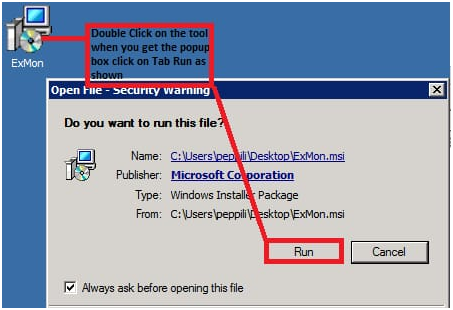
3- Select Run
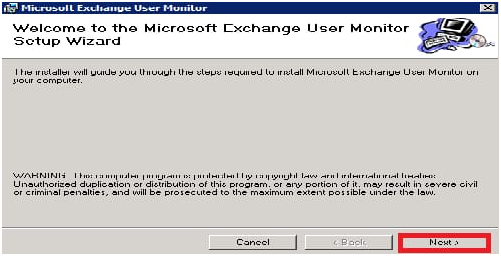
4- Select Next
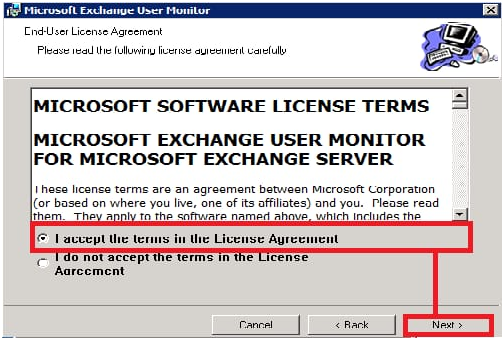
5- Admit to the licensing contract and select Next after it.
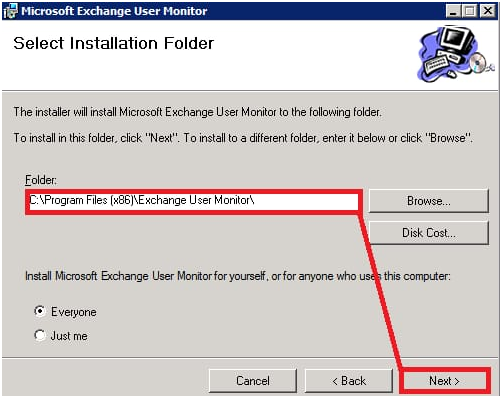
6- Indicate the location and select Next
7- Select Next and then Close
8- Installation of ExMon is confirmed.
Step 1 – Using ExMon
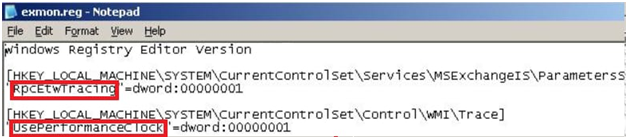
Click install path on ExMon.reg. it will ask for 2 registry keys for starting installation.
1st key: RpcEtwTracing
2nd key: UsePerformanceCloak
Now, when ExMon is installed. Let’s start working with this tool.
Execute the ExMon.exe file from the tab called installation directory (C:Program Files(X86)Exchange User Monitor)
The information collected by ExMon is transferred to a comma-separated text file (.CSV) which can be used or is reached with the help of Excel and Access.
Now turn on ExMon by using the command of ExMon in window with any of them –SU, -SV, -SC.
ExMon.exe –SU “C:Program Files(X86)Exchange User MonitordataUser.csv”
Step 2 – Using String.exe
The problem of these transaction logs can also be resolved by using another tool called Strings.exe which works by analyzing the logs.
IMPORTANT: maximum 100 logs are required to perform this task by strings.exe.
Withdraw it and save in any folder and place the folder at any location you want it to be orf is easily accessible for you. Then open power shell and find the location to the folder.
Use this command:
Syntax:
.strings.exe -q -n 16 D:templogs*.log | foreach-object { ($_.Split(“:”.ToCharArray(),3)[2]) }| group-object | select-object count,name | sort count | export-csv C:tempoutput.csv
On opening CSV file, at the end the most transacted mails and their occurrences with information will be given and we can take action on them and can decrease or even stop the rapid expansion of the logs.
Step 3 – NetMon:
Download the tool.
Before using it we need another tool called hotfix. Please download it then proceed.
Hotfix is used as a feature of Netmon in win 7 and Win server 2008R2
Select start- then Run- CMD (run as administrator)
Use
“Netsh trace start scenario=NetConnection capture=yes report=yes persistent=no maxsize=1024 correlation=yes traceFile=C:LogsNetTrace.etl”
Without the quotation marks and then Enter.