Some Active Directory access rights must frequently be granted temporarily, for a set length of time. To avoid having to monitor the validity of the given powers, they can be made temporary at first.
There are unique procedures — Temporary Group Membership — that may be used to create temporary permissions in AD, which will be explained in this post.
There are unique procedures — Temporary Group Membership — that may be used to create temporary permissions in AD, which will be explained in this post.
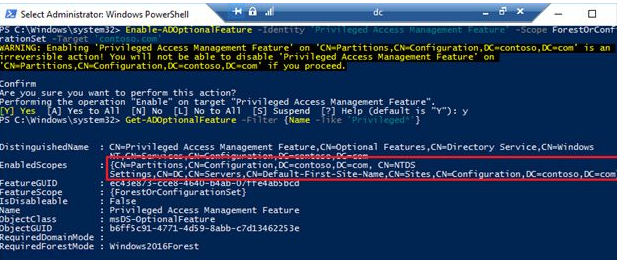
PAM is disabled by default, therefore the first thing you need to do is enable it. Enable-ADOptionalFeature is a PowerShell cmdlet that allows you to achieve this. Run the following command with domain administrator credentials to enable PAM in domain contoso.com:
Enable-ADOptionalFeature -Identity ″Privileged Access Management Feature″ -Scope ForestOrConfigurationSet -Target ″contoso.com″It’s important to note that enabling PAM is an irreversible process; you can’t turn it off after running the previous command. The following command can be used to verify the result:
Get-ADOptionalFeature -Filter {Name -like ″Privileged*″}Make sure your domain name is specified in the EnabledScope parameter. This indicates that Privileged Access Management for this domain is enabled.
When PAM is enabled, the MemberTimeToLive argument in the Add-ADGroupMember cmdlet appears, allowing you to set the group’s membership time. For example, for 5 minutes, add the JSilver user to the Domain Admins group:
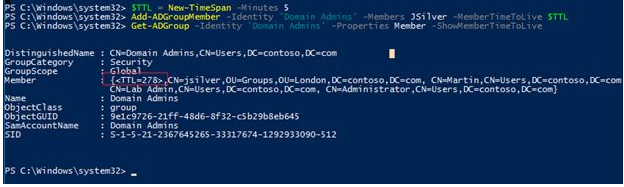
$TTL = New-TimeSpan -Minutes 5
Add-ADGroupMember -Identity ″Domain Admins″ -Members JSilver -MemberTimeToLive $TTLThen you can check the group membership with the command:
Get-ADGroup -Identity ″Domain Admins″ -Properties Member -ShowMemberTimeToLiveJSilver is a member of the Domain Admins group, and its TTL is 278 seconds, as you can see. After this period has passed, you can check the group membership again to ensure that it has been erased.
Because for users with transitory membership in AD groups, a ticket with a lifespan equal to the lesser of the remaining TTL values is issued, the validity period of the user’s Kerberos ticket likewise expires at the end of the TTL.
A Windows Server 2016 domain controller is required for Temporary Group Membership, as well as a forest level of at least Windows Server 2016. Using the following commands, you can get the Active Directory Forest and Domain functional level:
(Get-ADForest).ForestMode
(Get-ADDomain).DomainMode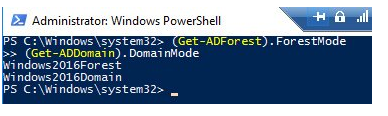
In older versions of Windows Server, you can use the less convenient capabilities of dynamic objects to implement temporary membership in groups (support for dynamic objects appeared since Windows Server 2003).
PowerShell can be used to generate dynamic objects. For example, here’s how to make a temporary AD group called TempGroup with a TTL of 600 seconds:
$OU = [adsi]″LDAP://CN=users,DC=contoso,DC=com″
$Grp = $OU.Create(″group″,″cn=TempGroup″)
$Grp.PutEx(2,″objectClass″,@(″dynamicObject″,″group″))
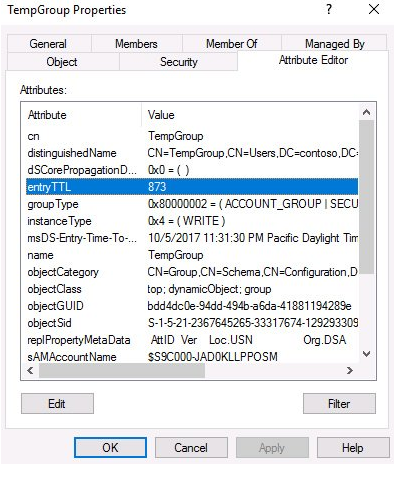
$Grp.Put(″entryTTL″,″600″)
$Grp.SetInfo()As a result, a Group TempGroup with a 10-minute lifetime will be generated in the Groups container (600 seconds). The group’s lifetime is maintained in the attribute entryTTL, which can be adjusted if necessary, for example, by increasing or decreasing it. The group vanishes after the specified amount of time has passed.