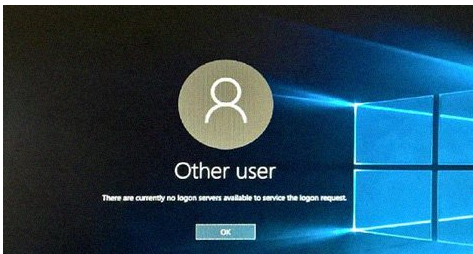
When a user logs on to a computer using a domain account, they enter credentials that are sent to the nearest domain controller for authentication. If there are no active domain controllers in the network, no one can verify the credentials, and the user is unable to log on to the system, and the following message appears after entering the password:
There are no log-on servers available to support the logon request at this time.
To circumvent this, the user’s credentials can be saved in the computer’s local cache after a successful login. This allows users to log on with domain cached credentials and access the computer’s local resources even if the domain controller connection is unavailable.
To be precise, only the MD5 hash of the password, modified with salt, which is generated based on the user name, is cached, not the credentials (login and password). The HKLMSECURITYCache registry key, which is only accessed by the SYSTEM account, stores cached data. It’s also worth noting that the cache’s lifetime on the computer is unrestricted.
Cached Credentials in Active Directory on Windows 10
This key contains information on the user (username, profile path, home directory, and so on), the domain (name, SID, last access time, and so on), and a hashed user password.
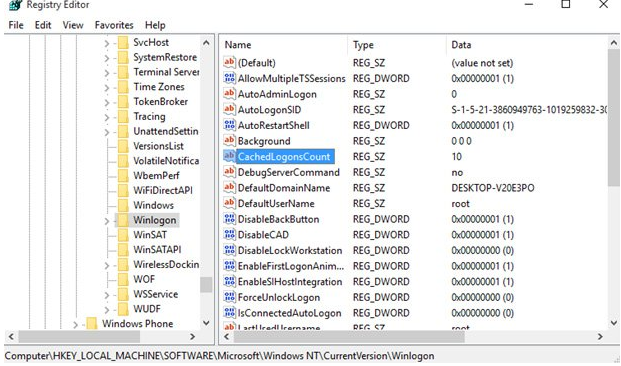
The caching capability is controlled by the CashedLogonsCount registry key. The registry key HKLMSoftwareMicrosoftWindows NTCurrentVersionWinlogon contains this option. The number of unique users whose credentials are saved locally is specified by this option. The parameter’s default value is 10, which implies that the credentials for the past 10 users logged on to the system are cached, and when the eleventh person connects on to the computer, the cached credentials of the first user are replaced.
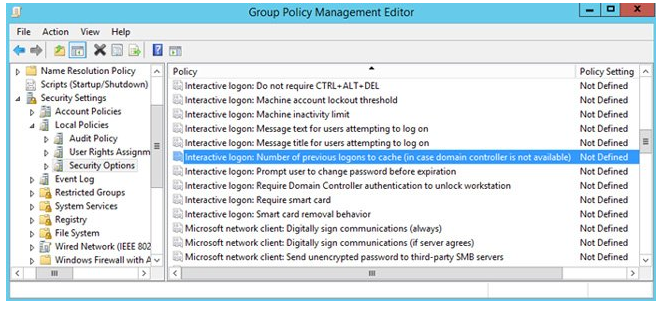
Using Group Policy, you can control the value of CashedLogonsCount from a central location. To do so, open an existing GPO and proceed to the Computer Configuration > Policies > Windows Settings > Security Settings > Local Policies > Security Options section, where you’ll find the Interactive logon: The number of prior logons that should be cached (in case domain controller is not available).
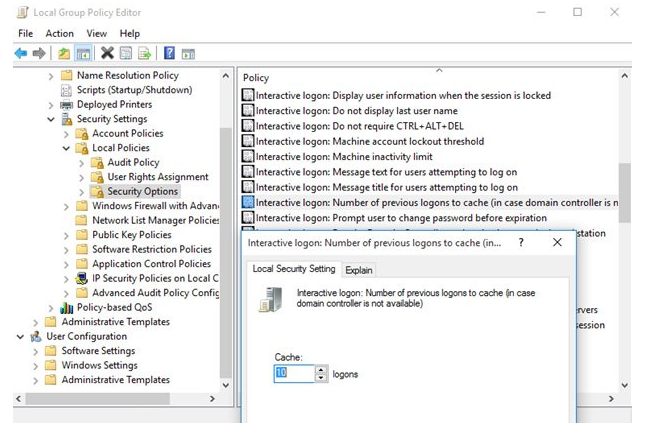
This policy is not defined by default, thus the default value is utilised on all computers. You must enable this policy and specify the needed value in the range of 0 to 50 to update it. When the domain controller is unavailable or the computer is disconnected from the network, a value of 0 signifies that credential caching is prohibited. At this value, logon to the local system is not allowed.
Because an attacker can utilise saved credentials if they have physical access to the computer, it is recommended to disable local caching for greater security. Mobile devices (laptops, tablets, etc.) that are utilised both within and outside the corporate network are an exception. The number of saved cached credentials for such systems can be set to 1. Only the most recent user is allowed to log on to the system.