Active Directory Federation Services (ADFS) is a Windows Server component that serves as an authentication provider for web applications. Federation Services are used in a variety of applications to authenticate remote users.
Active Directory Federation Services (ADFS) is a Windows Server component that serves as an authentication provider for web applications. Federation Services are used in a variety of applications to authenticate remote users.
Why do I need ADFS if I already have Active Directory? The fact is that Active Directory’s authentication mechanisms were not designed to work over the Internet. Kerberos will not function properly since it requires a web server and a client to be members of the AD domain. Authentication protocols such as NTLM and LM are likewise insecure.
ADFS is a service that manages access tokens. Its objective is to issue digital identities (Claims—CBA) to users who have successfully authenticated with Active Directory. These credentials will suffice for successful external user authentication and authorisation in the web app.
Active Directory Federation Services (ADFS) and Web Application Proxy are the two components of federation services (WAP). WAP takes Internet queries and forwards them to ADFS servers for processing. ADFS server responses are forwarded to WAP, which then forwards them to the Internet client. WAP can also be used to publish web applications via the Internet as a reverse proxy server. WAP, for example, can be used to quickly publish Exchange Web Access (OWA), internal SharePoint, and other content. The SSL 3.0 protocol encrypts data delivered over the network.
We’ll teach you how to install and configure the ADFS role on Windows Server 2016 in this article. It is advised that AD FS be installed on a dedicated server rather than being combined with RDS or RADIUS roles.
You’ll need to select a domain service account (from which ADFS services will run) and an SSL certificate when installing ADFS.
It is advised that a domain account, such as Group Managed Service Accounts, be created and used (gMSA). Using PowerShell, create a gMSA account in AD:
$server1 = Get-ADComputer adfs1
New-ADServiceAccount -Name "gMSAADFS" -DNSHostName gMSAADFS.test.com -Enabled $True -ManagedPasswordIntervalInDays 30 -PrincipalsAllowedToRetrieveManagedPassword $server1By default, gMSA accounts are created in the special OU—Managed Service Accounts
Then, through your internal CA (ADCS) or an external commercial Certificate Authority, obtain an SSL certificate with the EKU (extended key usage) “Server Authentication” and the ability to export the private key. A complete list of published FQDNs should be included in the certificate’s Subject name and Subject alternate name. The certificate must be saved in.pfx format.
Server Manager or a single PowerShell command can be used to deploy the ADFS 3.0 role on Windows Server 2016:
Add-WindowsFeature ADFS-Federation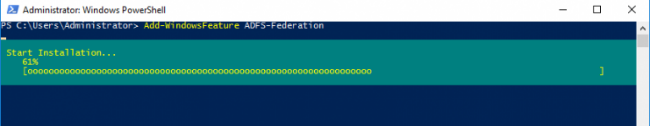
After installing ADFS, run the ADFS post-deployment task by pressing “Configure the federation services on this server” through the Server Manager snap-in.
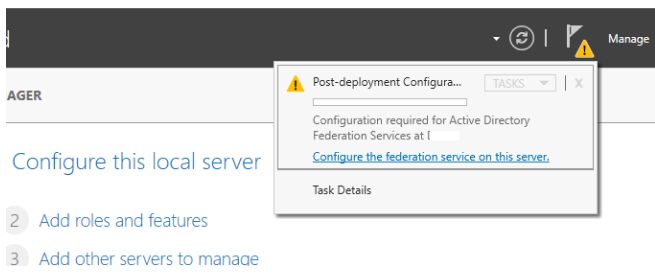
Choose the option “Create the first federation server in a federation farm”.
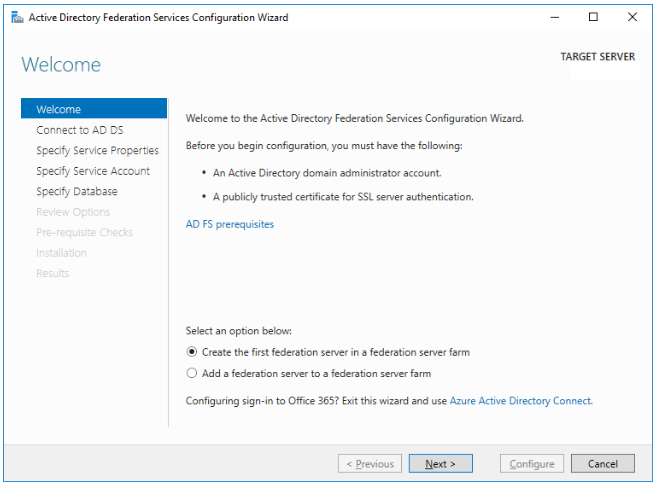
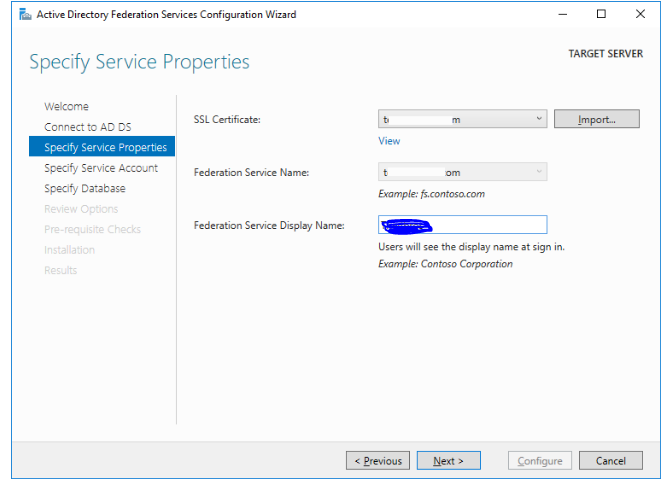
Select your pfx certificate file by pressing Import button.
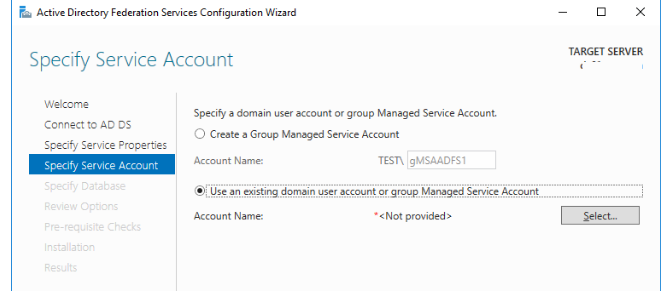
In the next step, specify the name of the gMSA account created earlier (gMSAADFS).
Choose whether you want to use a separate MS SQL Server or an internal Windows database (WID).
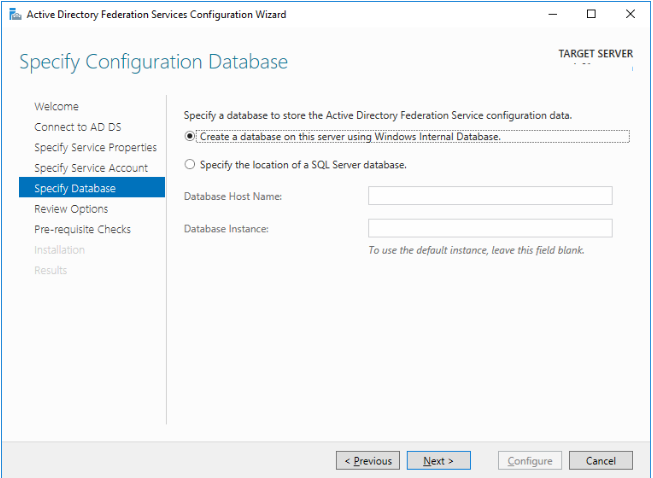
Then click Next > Next > Configure. That’s all, your ADFS server is deployed.
To check the availability of ADFS through a dedicated web page on Windows Server 2016, enable the IdpInitiatedSignOnPage option. Enable the test page with the PowerShell command:
Set-AdfsProperties -EnableIdpInitiatedSignonPage $trueYou must utilise the AD FS Management console to configure other ADFS options.