Execution Policy is one of the Windows security measures that determine whether PowerShell scripts can run on a computer or not.
Let’s take a clean Windows 10 as an example. Create a text file test_script.ps1 (with the PS1 extension) and with the following code:
Get-service bits, wuauserv
This simple PowerShell script should display the state of BITS and Windows Update services.
Open an elevated PowerShell console; go to the script folder and run:
PS C:\Windows\system32> cd C:\PS
PS C:\PS> .\test_script.ps1
An error should appear:
\test_script.ps1 : File C:\PS\test_script.ps1 cannot be loaded because running scripts is disabled on this system.
For more information about_Execution_Policies at http://go.microsoft.com/fwlink/?LinkID=135170.
At line:1 char:1
+ .\test_script.ps1
+ ~~~~~~~~~~~~~~~~~
+ CategoryInfo : SecurityError: (J [], PSSecurityException
+ FullyQualifiedErrorId : UnauthorizedAccess
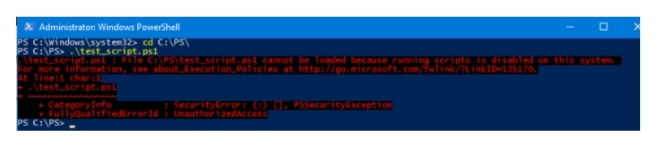
As you can see, PowerShell scripts are not allowed to run on Windows by default (even for an administrator). This security policy that controls the ability to run PowerShell scripts on Windows is called Execution Policy.
You can check the current Execution Policy value in Windows 10 using the command:
Get-ExecutionPolicy
Or directly from the registry:
Get-erty -path HKLM:\SOFTWARE\Microsoft\PowerShell\1\ShellIds\Microsoft.PowerShell -name “ExecutionPolicy”
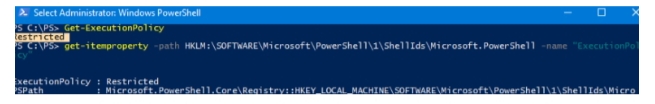
By default in Windows 10, this parameter is set to Restricted, which prevents any PowerShell scripts from executing.
You can set one of the following values in the PowerShell Execution Policy:
Restricted — this default value blocks the execution of any scripts and allows only to run interactive commands in the PowerShell console;
All Signed — allows execution of PowerShell scripts with a digital signature;
Remote Signed — allows running local scripts without a signature. A digital signature is required to run PS1 files downloaded from the Internet or received from a local network;
Unrestricted — any PowerShell scripts are allowed. When you run an unsigned script that was downloaded from the Internet, a confirmation prompt will appear;
Bypass — in this mode, nothing is blocked, no warnings or prompts appear.
Note that you can configure PowerShell execution policy in Windows at different levels:
Get-ExecutionPolicy -list
MachinePolicy
UserPolicy
Process
CurrentUser
LocalMachine
By default, the LocalMachine = Restricted policy is set at the computer level.
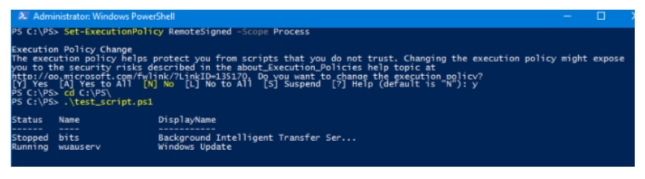
To allow PowerShell scripts to run only in the current session, you can run the commands:
Set-ExecutionPolicy RemoteSigned –Scope Process
Hint. Only an administrator can change the PowerShell Execution Policy settings.
The execution policy helps protect you from scripts that you do not trust. Changing the execution policy might expose you to the security risks described in the about_Execution_Policies help topic at http://go.microsoft.com/fwlink/?LinkID=135170. Do you want to change the execution policy?
[Y] Yes [A] Yes to All [N] No [L] No to All [S] Suspend [?] Help (default is “N”):
Press Y > Enter.
You can now run your PS1 script.
Powershell running scripts is disabled on this system
However, if you close the current PowerShell.exe console and open a new one, it will prevent PS1 scripts from running again. The most secure setting for the PowerShell Execution Policy parameter, which will allow you to run PS1 scripts and provide a sufficient level of security, is RemoteSigned.
To enable this mode at the computer level, run:
Set-ExecutionPolicy RemoteSigned
Now, even if you restart your PowerShell console, the scripts won’t be blocked from running.
To allow any PowerShell scripts to run, set the mode to Unrestricted (but this is not recommended from a security point of view):
Set-ExecutionPolicy RemoteSigned
You can also configure PowerShell Execution Policy in Windows via GPO. To do this, run the Local Group Policy Editor (gpedit.msc) and enable the Turn on Script Execution policy in the section Computer Configuration > Administrative Templates > Windows Components > Windows PowerShell.
Execution of scripts is disabled on this system
The following values are available in the policy:
- Allow only signed scripts;
- Allow local scripts and remote signed scripts;
- Allow all scripts.
- Update your GPO settings in order to apply the changes.
