The Microsoft Local Administrator Password Solution (LAPS) is a free solution that lets you manage local administrator passwords on domain-joined workstations. The LAPS agent is installed on domain computers and changes the local administrator’s password to a randomly generated one automatically (according to a schedule). Computer passwords are kept in Active Directory’s protected attributes of Computer objects.
In this post, we’ll teach you how to install and configure LAPS in an Active Directory domain running Windows Server 2016 on a functional level.
Installing LAPS Management Components
First, you need to install the LAPS components on the Active Directory administrator computer. Download LAPS version for your Windows version. In our example, we will install LAPS.x64.msi.
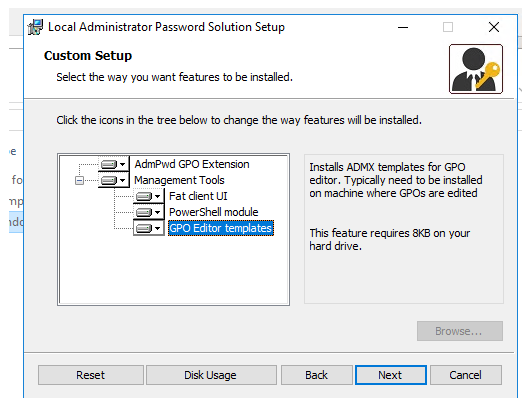
Run the LAPS.x64.msi file. MSI installer will prompt you to install the following components:
- AdmPwd GPO Extension — this is a LAPS agent that need to be installed on all computers;
- Fat Client UI — GUI tool for viewing the local administrator password;
- PowerShell Module — allows you to manage LAPS using PowerShell;
- GPO Editor templates — admx/adml GPO templates for configuring LAPS.
Extending the LAPS to the Active Directory Schema
LAPS stores its data using two new AD properties. The password is stored in the ms-Mcs-AdmPwd attribute, and the password expiration period is stored in the ms-Mcs-AdmPwdExpirationTime attribute. The schema must be modified in order for these properties to exist on computers in Active Directory.
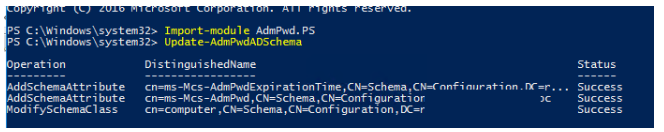
Open a PowerShell console as a member of the Schema Admin group with the admin account. Install the PowerShell LAPS module as follows:
Import-module AdmPwd.PSExtend your Active Directory schema:
Update-AdmPwdADSchema
In this example, we will apply LAPS policies to a single OU with computers in AD. Check which AD groups are allowed to access LAPS attributes:
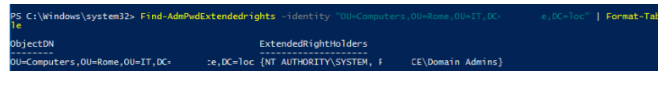
Find-AdmPwdExtendedrights -identity
“OU=Computers,OU=Rome,OU=IT,DC=solutionviews,DC=loc” | Format-TableThis command will return a list of accounts and groups that are allowed to view the passwords of computers in AD.
In our example, only NT AUTHORITY\SYSTEM and SOLUTIONVIEWS\Domain Admins have access to ExtendedRightHolders.
If you need to delegate the permissions to view computer passwords to other users, use the command:
Set-AdmPwdReadPasswordPermission -OrgUnit “OU=Computers,OU=Rome,OU=IT,DC=solutionviews,DC=loc” -AllowedPrincipals it_adm_viewerThen you need to allow computers to change the values of their own attributes in AD:
Set-AdmPwdComputerSelfPermission -OrgUnit “OU=Computers,OU=Rome,OU=IT,DC= solutionviews,DC=loc”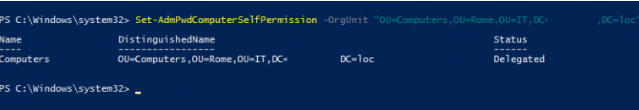
GPO Installation of LAPS Agent on Domain Computers
On domain machines, the LAPS extension must be installed. A GPO is the simplest way to install this software.
- Open the snap-in gpmc.msc;
- Make a new GPO and assign it to the OU that contains machines.
- Copy the LAPS.x64.msi installation file to the domain computer’s NETLOGON directory;
- Go to the GPO section after that. Computer Configuration > Policies > Software Settings > Software Installation;
- Create a package installation rule with the path to the MSI file in the NETLOGON share as the parameter.
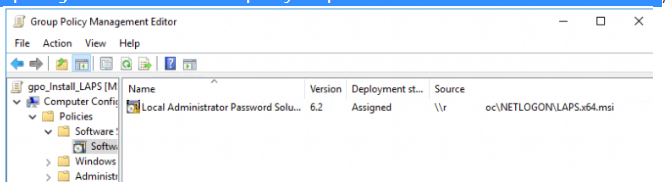
After rebooting, the LAPS extension will be installed on all computers in this OU.
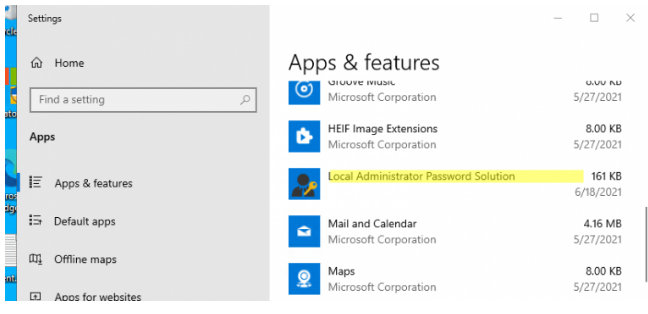
You can check that LAPS is installed on Windows 10 device through the Add/Remove programs.
LAPS Group Policy Configuration
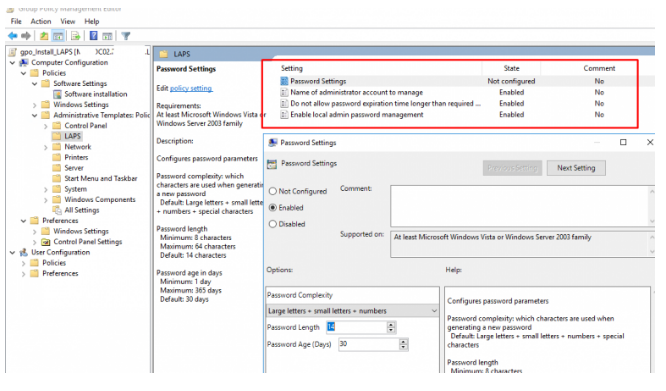
The LAPS parameters can be configured in the same policy. Computer Configuration > Policies > Administrative Templates > LAPS contains its parameters, which are contained in a distinct area of the GPO. Configure the policies in the following manner:
- Enable password management for local administrators: Enabled;
- Allow no more time for passwords to expire than is necessary by policy: Enabled;
- To manage, create a new administrator account with the following name: If you utilise an administrator account other than the built-in Administrator, you should apply this policy.
- Password Configuration: If enabled, set the complexity, length, and frequency of password changes here.
At the next GPO UPDATE LAPS will generate a new password for the local administrator, apply it on the computer, and save it to AD attributes.
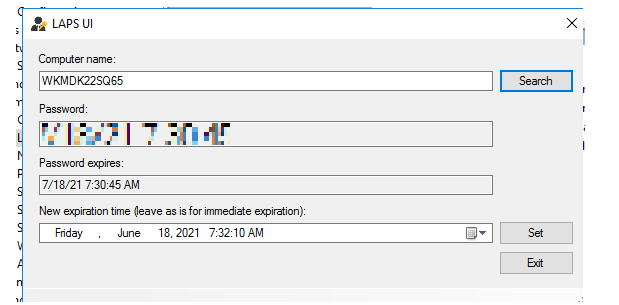
To view the local administrator password on a computer, use the LAPS UI tool. Just provide a computer name and click Search. The tool will connect to AD and get the current computer password.