A password expiration policy can be set up in the Active Directory domain. When a user’s password expires, it is forced to be changed.
When a user’s password in Active Directory expires, what happens? The user account is not blocked, but at the next logon, the user must change his own password: Your password has run out and needs to be replaced.
The user will be unable to access domain resources and computers until he changes his password.
Maximum Password Age in Default Domain Group Policy
Group Policy can be used to specify password expiration settings for domain users:
- Gpmc.msc is the Group Policy Management Console.
- Select Edit from the context menu of the Default Domain Policy.
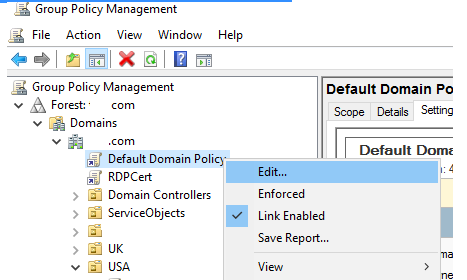
3. Go to the GPO section: Computer Configuration > Windows Settings > Security Settings > Account Policies > Password Policy;
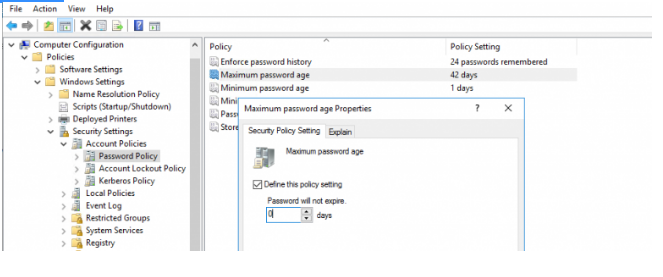
4. The maximum password age in days is set in the “Maximum password age” parameter. If the user password is older than this value, his password is considered expired;
5. You can change max password age or set it to 0 (in this case, user passwords in the domain are never expired).
You can get the user password expiration date with the command Get-ADUser from RSAT AD PowerShell module:
Get-ADUser –Identity username –Properties msDS-UserPasswordExpiryTimeComputed|Select-Object -Property Name, @{Name="ExpiryDate";Expression={[datetime]::FromFileTime($_.msDS-UserPasswordExpiryTimeComputed)}}
You can notify your Active Directory users when their password is about to expire using a special GPO option:
- Switch to the GPMC console and edit the Default Domain Policy;
- Expand the following GPO section: Computer Configuration > Policies > Windows Settings > Security Settings > Local Policies > Security Options;
- Find the policy named “Interactive Logon: Prompt user to change password before expiration”;
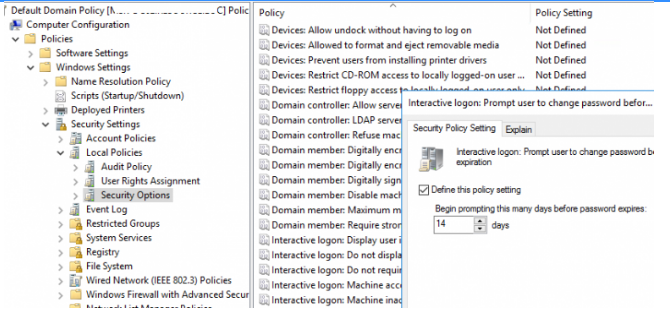
4. Enable this policy and specify the number of days (14 by default) before the user is notified of an impending password expiration.
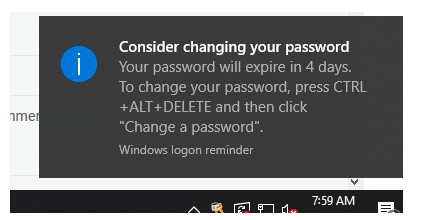
5. After signing in to any domain computer, if the user’s password expires in fewer than the set number of days, he will see the following reminder:
Set Custom Password Expiration Policy for Specific Users Only Using Fine-Grained Password Policy
Prior to Windows Server 2008, all users may have only one domain password policy. Using the Fine-Grained Password Policy in newer versions of Windows Server, you can specify that passwords are not expired for specified users or groups. For example, you might want to make the Domain Admins group’s password never expires policy.
- Start the terminal for Active Directory Administration Center;
2. Select New > Password Settings from the System section’s Password Settings Container;
3. Enter its name in the policy settings and uncheck the option Enforce maximum password age.
4. After that, you must add the group to which the policy should apply in the Direct Applies To area (in this example, Domain Admin group).
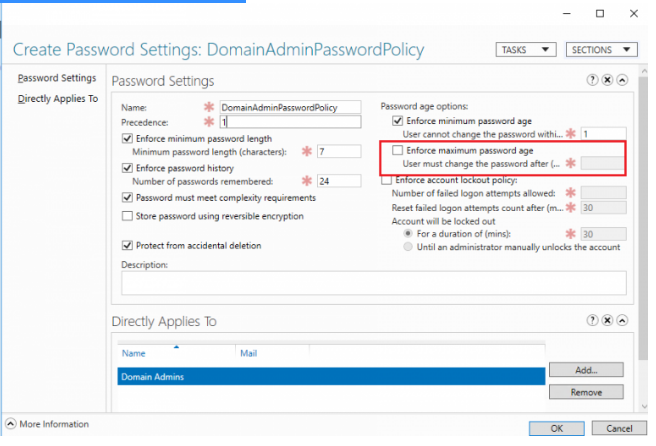
5. Save the policy.
Furthermore, you may utilise PowerShell to build Fine Grained Password Policies with specific password expiration settings and apply new PSOs (Password Setting Objects) to a user group.
Create a domain security group to which the PSO custom object will be applied:
Import-Module ActiveDirectory
New-ADGroup -Path "OU=Groups,OU=Texas,OU=US,DC=solutionviews,DC=com" -Name "grp_StrongPasswordExpirationPSO" -GroupScope Global -GroupCategory SecurityAdd users to the group to which you want to apply your custom PSO:
Add-ADGroupMember grp_StrongPasswordExpirationPSO -Members user1,user2,user3Assume the purpose is to implement tight password policies for a subset of users. We’ll set a maximum password age of 14 days and a minimum password age of 1 day in the password policy’s settings:
New-ADFineGrainedPasswordPolicy -Name "StrongPasswordExpirationPSO" -MinPasswordAge 1 -MaxPasswordAge 14 -Precedence 1 -Verbose
And now for the final step. The new fine-grained password expiration policy must be applied to the security group:
Add-ADFineGrainedPasswordPolicySubject -Identity "StrongPasswordExpirationPSO" -Subjects grp_StrongPasswordExpirationPSO
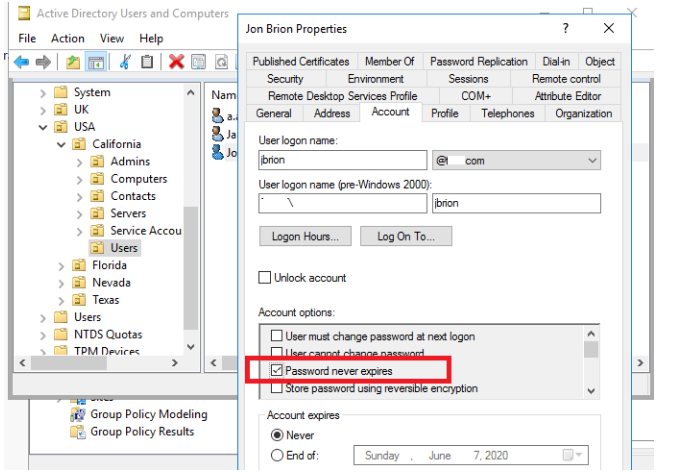
If you set the “Password never expires” option in user properties in AD, you can stop password expiration for a single user. This option can be enabled using the ADUC console (Find user > Properties > Account tab > select the “Password never expires” option under the Account settings section).
You can enable password newer expires flag for a specific user using PowerShell:
Set-ADUser -Identity M.Becker -PasswordNeverExpires $true –verbose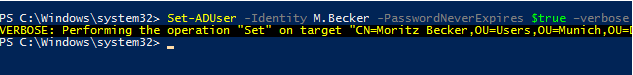
You may also arrange passwords to never expire for numerous user accounts using a simple AD LDAP filter. In this example, the PasswordNeverExpires option is enabled for all US users in the DevOps department:
Import-Module ActiveDirectory
Get-ADUser -LDAPFilter '(Department=*DevOps*)'-SearchBase "OU=US,DC=solutionviews,DC=com" | Set-ADUser -PasswordNeverExpires:$TrueYou can save a CSV file with a list of users that have the password never expires option enabled:
get-aduser -filter * -properties Name, PasswordNeverExpires | where {
$_.passwordNeverExpires -eq "true" } | Select-Object DistinguishedName,Name,Enabled |
Export-csv c:\PS\password_never_expires.csv –NoTypeInformation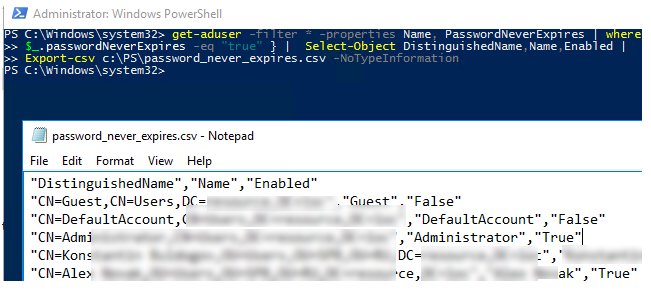
Only domain users, not domain machines, are subject to the domain password expiration policy.
You can set how often a domain member has to change their password using a separate policy for domain machines. Domain member: Maximum machine account password age is the policy’s name. Computer Configuration > Windows Settings > Security Settings > Local Policies > Security Options is where you’ll see it in the GPO section. The procedure of updating the computer password is totally automated and is carried out by the computer’s NETLOGON service once every 30 days by default. This policy can be used to raise or decrease the interval (from 1 to 999 days).
You won’t be able to login to the computer as a domain user if the password on the computer that is saved locally doesn’t match the password in the Active Directory database. This workstation’s trust relationship with the parent domain has broken down.
You must enable the Domain member: Disable machine account password changes policy to totally disable password changes for computer accounts.