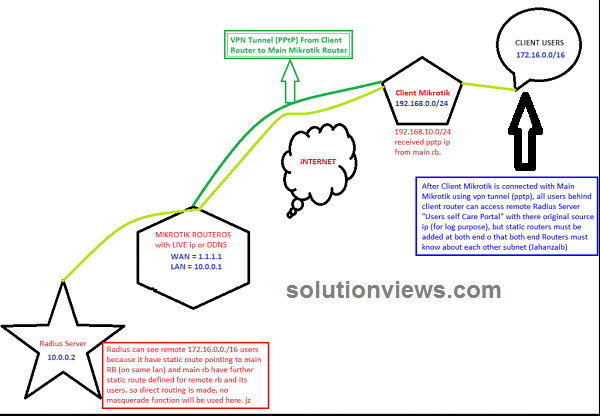
Consider following scenario:
An ISP have multiple locations everywhere the country. Main Mikrotik router at NOC has mounted public information science. Radius asking system is connected with LAN. All remote locations have Mikrotik Router boards as NAS and have dynamic public information science. All locations have their own net property with varied ISP’s however we would like to use our main RADIUS server as a centralized asking resolution for all the REMOTE locations. Therefore this is often a brief guide how to produce central Radius Server and connected all remote branches/nases with it.
Basic Points:
Create PPTP server at your Head workplace Mikrotik.
Create user account on the Q.T. section, nd assign him fix information science address like 172.16.1.50
Now at branch workplace, produce a pptp shopper in mikrotik pptp section, and add head workplace information science / user id passwd, Dont forget to UNCHECK “add DEFAULT ROUTE” button. as a result of if you are doing therefore it’ll override default route and can route each traffic as well as net requests too to move workplace, which is able to overload head workplace net affiliation, since we have a tendency to solely need to route request for specific IP/subnet, therefore we’ll produce a route at each finish in order that request for specific information science subent ought to go via vpn tunnel .
Head workplace Mikrotik Config:
LAN subnet = ten.0.0.1/8
WAN subnet = one.1.1.1/29
Radius = ten.0.0.2/
First add information science pool for VPN users, like same as LAN series however with specific series.
/ip pool
add name=PPP-Pool ranges=172.16.0.1-172.16.1.255
Now add VPN Profile
/ppp profile
set zero change-tcp-mss=yes name=default only-one=default use-compression=default use-encryption=default use-mpls=default use-vj-compression=default
add change-tcp-mss=default dns-server=10.0.0.1 local-address=10.0.0.1 name=vpn-profile only-one=default remote-address=PPP-Pool \
use-compression=default use-encryption=default use-mpls=default use-vj-compression=default
set a pair of change-tcp-mss=yes name=default-encryption only-one=default use-compression=default use-encryption=yes use-mpls=default use-vj-compression=default
Now change VPN server
/interface pptp-server server
set authentication=mschap1,mschap2 default-profile=default-encryption enabled=yes keepalive-timeout=30 max-mru=1460 max-mtu=1460 mrru=disabled
Now add user in order that we’ll be testing from remote location NAS.
/ppp secret
add caller-id=”” disabled=no limit-bytes-in=0 limit-bytes-out=0 name=aa password=aa profile=vpn-profile routes=”” service=any
Now add route for the 192.168.100.0/224 subnet in information science ROUTE section , via pptp entryway.
Remote Branch Mikrotik Config
LAN subnet = 192.168.100.1/8
WAN subnet
= DYNAMIC Public information
science x.x.x.x
Now we would like to attach remote NAS with
head workplace VPN
server in order that it will use central radius server as
a centralized asking system.
In
short: produce a pptp
dialer , inform to move workplace Main rubidium (where
vpn is configured) , enter valid user id secret, check that you take away tick from add default
route, once its connect, merely add a route for ten.0.0.0/8 and its entryway inform to pptp-out1 (pptp link we have a tendency to created above)