LDAP queries can be used to search the Active Directory LDAP database for certain objects (computers, users, and groups) based on a set of criteria. You can use numerous programmes (for example, ldapsearch), PowerShell or VBS scripts, the Saved Queries feature in the Active Directory Users and Computers MMC snap-in, and so on to run an LDAP query against the AD LDAP catalogue.
How do I do an LDAP query?
Let’s start by looking at some LDAP (Lightweight Directory Access Protocol) query examples. You might want to use a basic LDAP query to find Active Directory users who have the “User must change password at next logon” option activated. The following is the code for this LDAP query:
(objectCategory=person)(objectClass=user)(pwdLastSet=0)(!useraccountcontrol:1.2.840.113556.1.4.803:=2)Let’s try to execute this LDAP query using the AUDC console.
- Open the ADUC console and go to the Saved Queries section;
- Create a new query: New > Query;
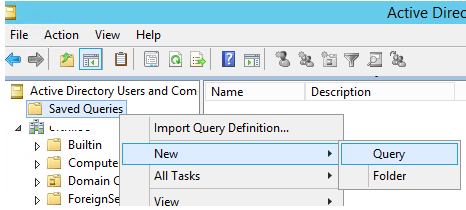
3. Specify a name for the new saved query and click the Define Query button;
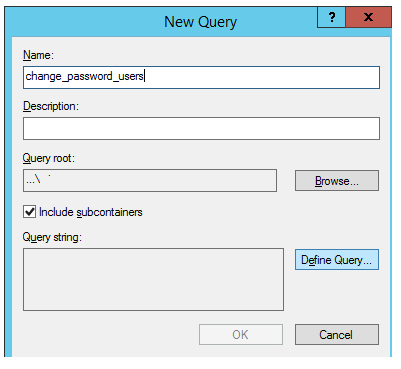
4. Select the Custom Search type, go to the Advanced tab, and copy your LDAP query code into the Enter LDAP query field;
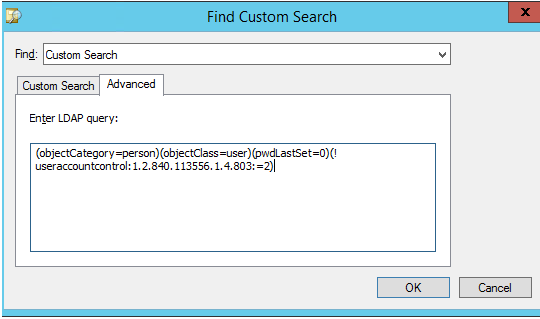
5. Click OK twice, select your new query in the ADUC Saved Queries tree, and press F5;
6. A list of AD users that match this LDAP query should display on the right pane.
You can also utilise the LDAP query filter in the Get-ADUser, Get-ADComputer, Get-ADGroup, and Get-ADObject PowerShell cmdlets (these cmdlets are part of the Active Directory PowerShell module). The LdapFilter option in each of these cmdlets is meant to employ LDAP filters while looking for objects in Active Directory.
To use Get-ADUser to run the aforementioned LDAP search query, launch the powershell.exe terminal and type the following command:
Get-ADUser -LDAPFilter '(objectCategory=person)(objectClass=user)(pwdLastSet=0)(!useraccountcontrol:1.2.840.113556.1.4.803:=2)'To search for computers, use the Get-ADComputer cmdlet:
Get-ADComputer –LDAPFilter ‘your ldap query’To search for Active Directory security and distribution groups in AD, use the Get-ADGroup cmdlet:
Get-ADGroup –LDAPFilter {LDAP_query}If you don’t know the type of Active Directory object you are looking for, you can use the generic Get-ADObject cmdlet:
Get-ADObject -LdapFilter "(cn=*Brion*)"In this example, we found that the given LDAP filter matches the user Jon Brion and the BrionTeam group.
If you need to find objects of a specific type, you can specify the object type using the objectClass parameter. For example:
Get-ADObject -LdapFilter "(&(objectClass=user)(cn=*Brion*))"Windows has several built-in tools such as dgst and dsquery, that allow you to run LDAP queries against Active Directory,
The dsquery utility returns the Distinquished Name of an object that matches the specified parameters, and for LDAP filters it has a filter parameter. For example, to find all users with job title starting with Manager, run the command:
dsquery * OU=Employees,DC=solutionviews,DC=com -filter "(&(objectCategory=person)(objectClass=user)(Title=Manager*))"
LDAP Filter Syntax
The text form of LDAP search filters is defined in RFC 4515. The syntax for an LDAP filter is:
<Filter>=(<Attribute><comparison operator><value>)The following comparison operators can be used in a filter:
| Operator | |
| = | Equal |
| >= | More or equal |
| <= | Less or equal |
| ~= | Approximately equal |
For example, the following filter returns all objects with cn (common name) attribute value Jon:
(cn=Jon)Filters can be combined using boolean operators when there are multiple search conditions.
| Operator | |
| & | AND — all conditions must be met |
| | | OR — any number of conditions can be met |
| ! | NOT — the condition must not be met |
For example, let’s select AD objects with cn equal to Jon and sn (surname) equal to Brion:
(&(cn=Jon)(sn=Brion))You can use several logical operators in one filter at once, the main thing is not to get confused in parentheses. Let’s compose a filter that will return objects with cn equal to Jon or sn equal to Brion, for which cn is not equal to Alex:
(&(|(cn=Jon)(sn=Brion)(!(cn=Alex)))You can refine search objects using the objectCategory and objectClass attributes.
Valid parameters: person, user, contact, computer, groups.
Using the following filter, select all users named Jon:
(&(objectClass=user)(objectCategory=person)(cn=Jon))LDAP Query Examples for Active Directory
Let’s consider some useful examples of LDAP queries that are often used by the AD admins.
Search for administrators in groups Domain Admins, Enterprise Admins:
(objectClass=user)(objectCategory=Person)(adminCount=1)List all AD users except blocked ones:
(objectCategory=person)(objectClass=user)(!useraccountcontrol:1.2.840.113556.1.4.803:=2)Display the list of disabled user accounts:
(objectCategory=person)(objectClass=user)(useraccountcontrol:1.2.840.113556.1.4.803:=16)Select users with the “Password never expires option” enabled:
(objectcategory=user)(userAccountControl:1.2.840.113556.1.4.803:=65536)Users with empty email value:
(objectcategory=person)(!mail=*)List users with the Sales specified in the Department field: (&(objectCategory=person)(objectClass=user)(department=Sales))
You can get a list of users with membership in a specific Active Directory group:
(&(objectclass=user)(samacccountname=*)(MemberOf=CN=UKManagers,OU=Groups,OU=UK,DC=solutionviews,DC=com))You can list the groups the user is a member of:
(&(objectCategory=group)(member=CN=Jon Brion,OU=Employees,DC=solutionviews
,DC=com))List all disabled computer accounts in AD:
(&(objectClass=computer)(userAccountControl:1.2.840.113556.1.4.803:=2))Display all Windows 10 computers:
(objectCategory=computer)(operatingSystem=Windows 10*)You can only select computers with a specific build of Windows 10:
(&(&(objectCategory=computer)(operatingSystem=Windows 10*)(operatingSystemVersion=*19041*)))Hint. You can map Windows 10 build to version according the following table:
| Windows 10 Version | Build number |
| 20H2 | 19042 |
| 2004 | 19041 |
| 1909 | 18363 |
| 1903 | 18362 |
| 1809 | 17763 |
All domain controllers:
(&(objectCategory=computer)(userAccountControl:1.2.840.113556.1.4.803:=8192))All member domain servers (except DCs):
(&(objectCategory=computer)(operatingSystem=*server*)(!userAccountControl:1.2.840.113556.1.4.803:=8192))All MS SQL Server instances in AD:
(&(objectCategory=computer)(servicePrincipalName=MSSQLSvc*))List of groups created for the specified period:
(objectCategory=group)(whenCreated>=20200101000000.0Z&<=20201201000000.0Z&)List all empty AD groups:
https://4d72a04c5d3065427eddf353489dbf7b.safeframe.googlesyndication.com/safeframe/1-0-38/html/container.html(objectCategory=group)(!member=*)List all distribution groups:
(&(objectCategory=group)(!groupType:1.2.840.113556.1.4.803:=2147483648))Print all groups with the *CIO* key in the group name:
(objectCategory=group)(samaccountname=*CIO*)Find all Exchange Servers in the domain:
(objectCategory=computer)(servicePrincipalName=exchangeMDB*)(operatingSystem=Windows Server*)All color printers on a specific print server published in the AD:
(uncName=*lon-prnt*)(objectCategory=printQueue)(printColor=TRUE)