You can synchronise data from your on-premises Active Directory with Azure AD using Azure AD Connect. When configuring AD Connect, password sync is enabled by default. This allows on-premises AD users to log in to Microsoft Azure cloud services using a single login.
Passwords are not kept in clear text in Windows Active Directory. They’re saved as a hash, which is calculated from the password using the SHA256 hash technique.
Note. This means that retrieving an AD user’s plain text password from the ntds.dit database is impossible. Only the hash of the password is provided.
Password hashes are encrypted in transit to Azure AD (using SSL/TLS) for enhanced security. The user’s password is synchronised with Azure AD every 2 minutes in a healthy AD infrastructure. In two minutes, if you update your password in on-premises AD, it will be reflected in Azure.
You’ll need to download and install AzureADConnect to set up sync between your Azure AD tenant and on-premises Active Directory.
Hint: AzureADConnect replaces DirSync, which was previously utilised for synchronisation.
The server on which AzureADConnect is installed must meet the following requirements:
Windows Server 2012 R2 or later is required.
Availability of Azure access and a static public IP address; Net Framework 4.5;
AzureADConnect should not be installed on domain controllers or ADFS servers.
Download and run the AzureADConnect.msi;
Accept the terms of the licence;
You can either pick Express installation (which is suggested) or use the Customize button to change the installation parameters. Change the installation directory, specify the SQL server (by default, a local instance of SQL Server Express is installed, and the Azure AD Sync database is stored in the directory C:Program FilesMicrosoft Azure AD Sync), select a service account for the Microsoft Azure AD Sync service, and change directory sync permissions in Customize mode.
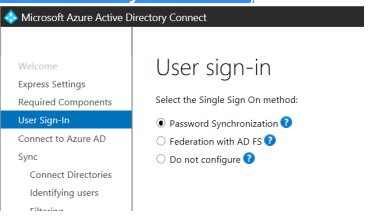
Select Single Sign on method – Password Synchronization;
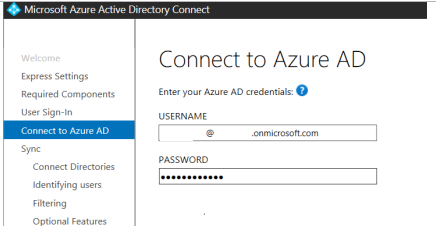
To connect to the tenancy, enter the credentials of an Azure account with Global Admin permissions. Note. Microsoft recommends that you use a tenant.onmicrosoft.com account with a permanent password and no Multi-Factor Authentication (MFA). The Azure AD Connect sync will fail if the password for this account expires in Azure AD.
Choose a way to identify users > Users are represented only once across all directories;
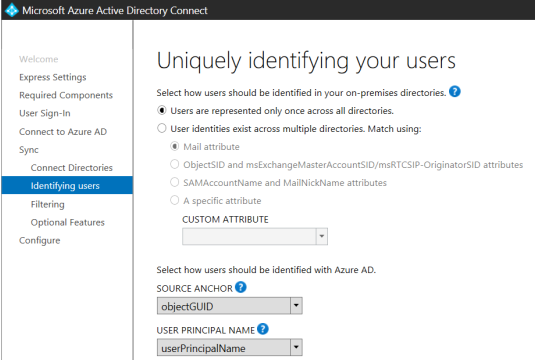
With AzureAD, you can only synchronise one user group (users must be added directly to this group, nested AD groups users are not synchronized). If you choose to sync all users and devices, you may later change sync directory partitions with the Synchronization Service Manager application (which is included in the AzureADConnect installation).
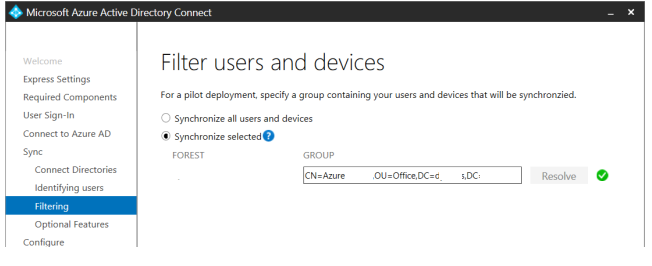
Select additional options. Password hash synchronization is selected by default. Select the Password writeback option if you want to allow your users to reset their on-premises AD passwords from Azure;
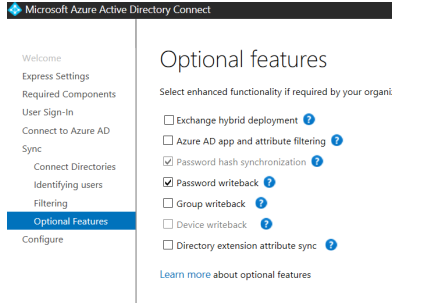
If you want to start an immediate synchronization, enable the Start the synchronization process as soon as the configuration completes option (it may take a significant amount of time depending on the size of your on-premises AD database).
After the AzureADConnect installation is complete, a new Azure AD Sync Scheduler task appears in Task Scheduler.
To verify that the passwords are correctly synchronized with Azure AD, you can use the PowerShell cmdlet from the AAD Connect module:
Import-Module adsyncInvoke-ADSyncDiagnostics -PasswordSync
You also need to pay attention to the events Event ID 611, 657 on the Sync server. When they appear, it is recommended to force synchronization using the following PowerShell script:
$adConnector and $aadConnector are case-sensitive parameters
$adConnector = “solutionviews.com”
$aadConnector = “solutionviews.onmicrosoft.com – AAD”
Import-Module adsync
$c = Get-ADSyncConnector -Name $adConnector
$p = New-Object Microsoft.IdentityManagement.PowerShell.ObjectModel.ConfigurationParameter “Microsoft.Synchronize.ForceFullPasswordSync”, String, ConnectorGlobal, $null, $null, $null
$p.Value = 1
$c.GlobalParameters.Remove($p.Name)
$c.GlobalParameters.Add($p)
$c = Add-ADSyncConnector -Connector $c
Set-ADSyncAADPasswordSyncConfiguration -SourceConnector $adConnector -TargetConnector $aadConnector -Enable $false
Set-ADSyncAADPasswordSyncConfiguration -SourceConnector $adConnector -TargetConnector $aadConnector -Enable $true