OVERVIEW:
In this
post we have a tendency to are aiming to link associate Azure
Virtual Network to on associate premise
network via a Cisco ASA. We’ll be making a route based mostly affiliation exploitation IKEv2 and a VTI
interface.
We also are aiming to specialize
in a way to accomplish this exploitation ASDM.
PREREQUISITES:
- I am aiming to assume you’re already exploitation Azure and you have already got a Virtual Network in situ.
- You ASA must be running a minimum of nine.7 but 9.8 or higher is most well-liked. I will be able to be exploitation nine.8
- You will want ASDM, i will be able to be exploitation seven.9
THE AZURE aspect
VIRTUAL NETWORK entry:
If you
Virtual Network already features a “Virtual
network gateway” check you settings match then you’ll skip this section.
- Under “Create a resource” within the high left seek for and choose “Virtual network gateways”
- Click produce
- Complete the form;
- Name: no matter matches your naming convention.
- Gateway Type: VPN
- VPN Type: Route based
mostly
SKU: VpnGW1 (or higher, basic doesn’t support IKEv2) - Virtual Network: no matter Azure network we have a tendency to are connection over the VPN.
- Public IP: produce new unless you have already got an area and provide it a reputation.
- Subscription: Your subscription
- Location: usually your virtual networks location.
- Click produce
LOCAL
NETWORK entry:
Next we’d like a neighborhood Network entry to outline our
ASA public information processing address and also the list of on premise
network(s) we would like over
the VPN.
- Under “Create a resource” within the high left seek for and choose “Local network gateway”
- Click the Add button
- Complete the form:
- Name: no matter matches your naming convention.
- IP Address: this is often the skin public information processing address of your ASA
- Address space: This wherever you add you om premises subnets/vlan’s exploitation the networks CIDR for instance ten.0.100.0/24
- Subscription: Your subscription
- Resource Group: your required resource cluster
- Location: usually your virtual networks location.
- Click produce
A affiliation:
Navigate into your antecedently created Virtual
network entry and click on Connections
Click Add
Complete
the form:
Name: no matter matches your naming
convention.
Connection
Type: Site-to-Site (IPSec)
Virtual
network entry: ought to be pre-filled with you
Virtual network gateway
Local
network entry: choose the antecedently created native network gateway
Shared key
(PSK): choose as befittingly complicated string and build a note of it for later
Click OK
THE ASA aspect:
Connect to
your ASA exploitation ASDM.
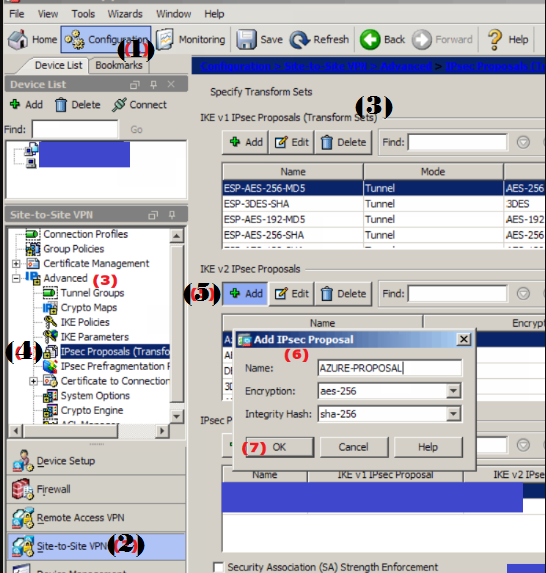
IKE V2 IPSEC PROPOSAL
- Navigate to Configuration -> Site-to-Site-VPN -> Advanced -> IPSEC Proposals (Transformation Sets)
- Add a internet proposal within the Dwight D. Eisenhower v2 section
- Name: AZURE-PROPOSAL (Or no matter matches your naming convention)
- Encryption: aes-256
- Integrity Hash: sha-256
- Click OK
- Click Apply
Or the CLI would be:
crypto IPsec ikev2 IPsec-proposal AZURE-PROPOSAL
protocol ESP cryptography aes-256
protocol ESP integrity sha-256
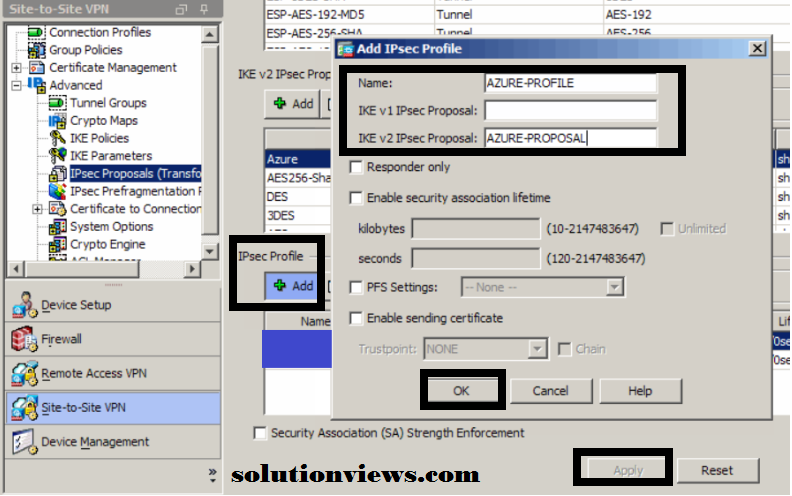
IPSEC PROFILE:
Still underneath Configuration -> Site-to-Site-VPN -> Advanced -> IPSEC Proposals (Transformation Sets)
Add a replacement IPsec Profile
Name: AZURE-PROFILE (Or no matter matches your naming convention)
IKE v2 IPSEC Proposal: AZURE-PROPOSAL (what we have a tendency to simply created)
Click OK
Click Apply
Or the CLI would be:
crypto IPsec profile AZURE-PROFILE
set ikev2 IPsec-proposal AZURE-PROPOSAL
VTI INTERFACE:
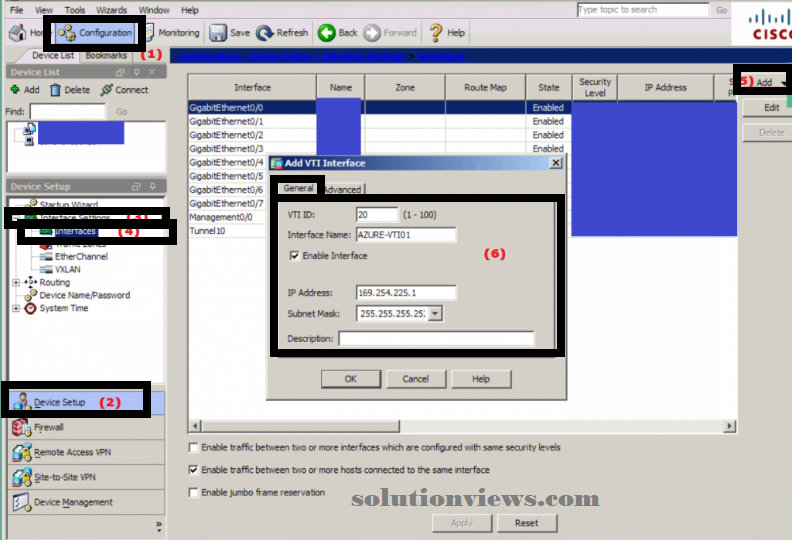
Navigate to Configuration -> Device Setup -> Interface Settings -> Interfaces
Click Add on the proper and choose “VTI Interface” from the change posture
On the final tab:
VTI ID: Any range you wish that isn’t already in use 1-100
Interface Name: AZURE-VTI01 (Or no matter matches your naming convention)
Enable Interface: Checked
IP Address: 189.124.124.1 (Or no matter you like)
This is the information processing of the VTI interface therefore it can’t be used anyplace else in your ASA’s configuration.
I have gone with associate APPIPA address as I don’t use them anyplace else.
It solely must be a non-public address.
Later once we get into routing .2 are going to be our next hop to Azure.
Subnet Mask: 255.255.255.252 (we solely want 2 addresses)
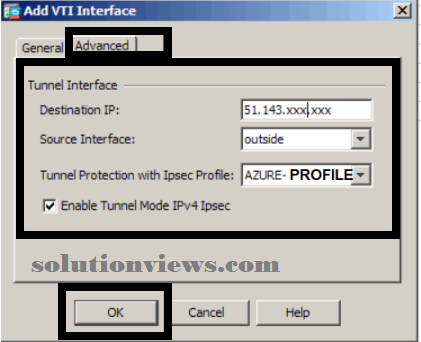
On the Advanced tab
Destination information processing: the general public IP address of your Azure Virtual Network entry, that on be found on the summary pane for the entry.
Source Interface: outside (typically)
Tunnel protection with IPsec profile: AZURE-PROFILE (what we have a tendency to antecedently created)
Enable Tunnel Mode IPv4 IPsec: Checked
Click OK
Click Apply
Or
the CLI would be:
Interface
Tunnel20
no ending
nameif
AZURE-VTI01
ip address
169.254.225.1 255.255.255.252
tunnel
destination fifty one.143.xxx.xxx
tunnel supply interface outside
tunnel
protection ipsec profile AZURE-PROFILE
tunnel mode
ipsec ipv4
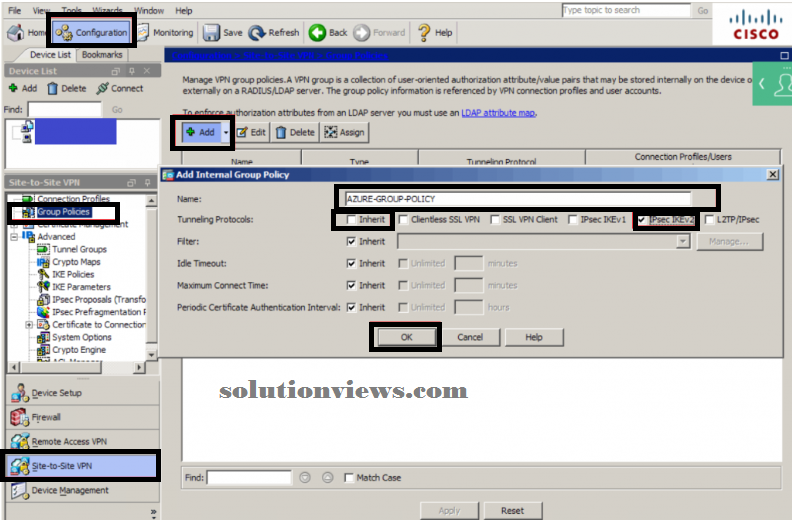
GROUP POLICY: Navigate to Configuration-> Site-to-Site VPN -> cluster Policies
Click Add
Name: AZURE-GROUP-POLICY
Tunneling Protocols: Un-check inherit and check IPsec IKEv2
Click OK
Click Apply
Or
the CLI would be:
group-policy
AZURE-GROUP-POLICY internal
group-policy
AZURE-GROUP-POLICY attributes
vpn-tunnel-protocol
ikev2
exit
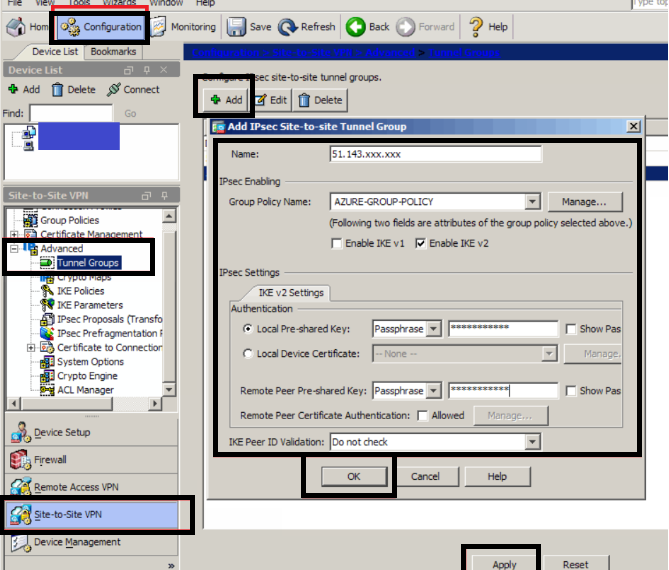
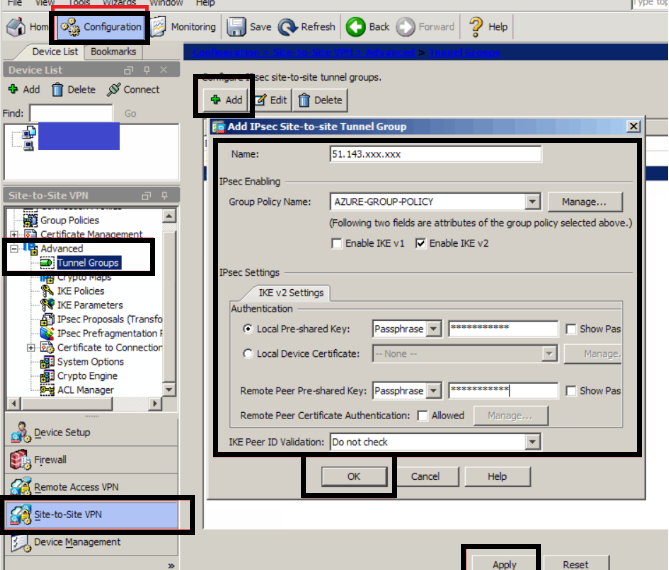
TUNNEL cluster:
Navigate to
Configuration -> Site-to-Site VPN -> Advanced -> Tunnel teams
Click Add
Name: the general public information processing address of
your Azure Virtual Network entry.
As we have a tendency to used
on the advanced tab once fitting the VTI interface
AZURE-GROUP-POLICY (what we have a tendency to simply created)
Local and Remote Pre-Shared Keys: The PSK we have a tendency to set once making the affiliation on the Azure Virtual entry.
IKE Peer ID Validation: don’t Check
Click OK
Click Apply
Or
the CLI would be:
Interface
Tunnel20
no ending
nameif
AZURE-VTI01
ip address
169.254.225.1 255.255.255.252
tunnel
destination fifty one.143.xxx.xxx
tunnel supply interface outside
tunnel
protection ipsec profile AZURE-PROFILE
tunnel mode
ipsec ipv4
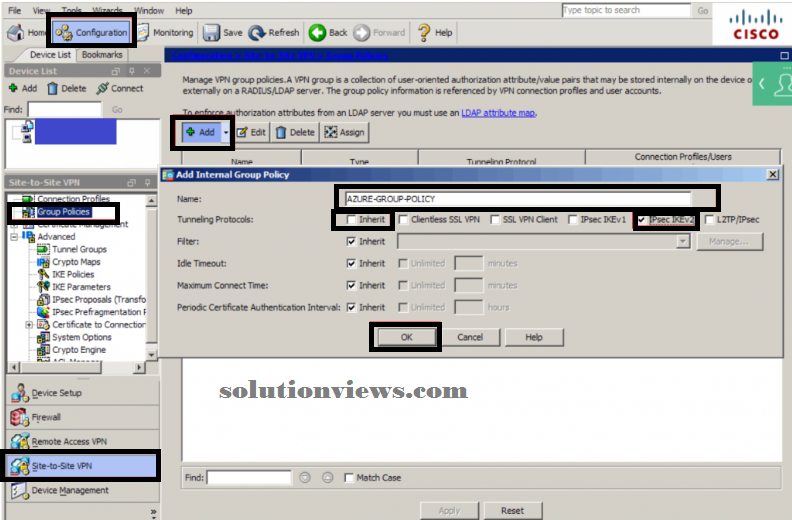
GROUP POLICY:
Navigate to Configuration-> Site-to-Site VPN -> cluster Policies
Click Add
Name: AZURE-GROUP-POLICY
Tunneling Protocols: Un-check inherit and check IPsec IKEv2
Click OK
Click Apply
Or
the CLI would be:
group-policy
AZURE-GROUP-POLICY internal
group-policy
AZURE-GROUP-POLICY attributes
vpn-tunnel-protocol
ikev2
exit
TUNNEL cluster:
Navigate to
Configuration -> Site-to-Site VPN -> Advanced -> Tunnel teams
Click Add
Name: the general public information processing address of
your Azure Virtual Network entry.
As we have a tendency to used
on the advanced tab once fitting the VTI interface
AZURE-GROUP-POLICY (what we have a tendency to simply created)
Local and Remote Pre-Shared Keys: The PSK we have a tendency to set once making the affiliation on the Azure Virtual entry.
IKE Peer ID Validation: don’t Check
Click OK
Click Apply
Or the CLI would be:
tunnel-group fifty one.143.xxx.xxx sort ipsec-l2l
tunnel-group fifty one.143.xxx.xxx general-attributes
default-group-policy AZURE-GROUP-POLICY
tunnel-group fifty one.143.xxx.xxx IPsec-attributes
peer-id-validate nocheck
ikev2 local-authentication pre-shared-key MyVerySecureKey
ikev2 remote-authentication pre-shared-key MyVerySecureKey
isakmp keep alive threshold ten hear two
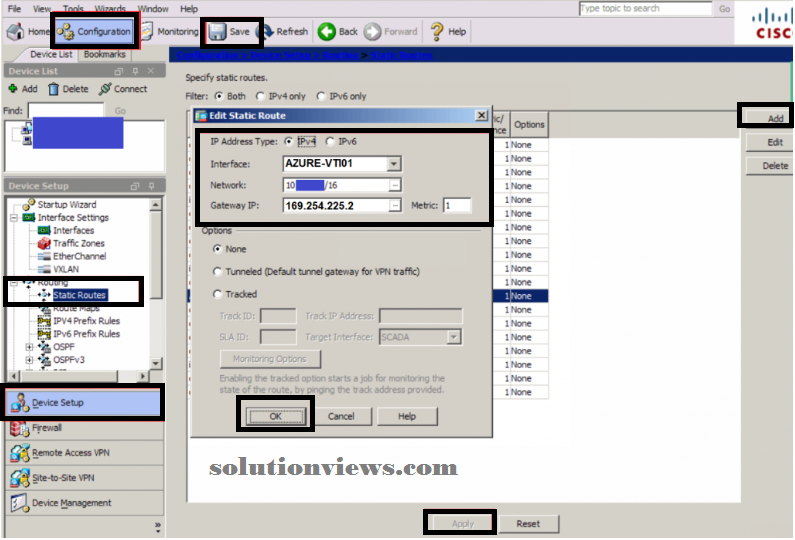
THE ROUTE(S):
The last step is to outline what destination(s) we’ll be routing over the VPN. During this example with can use a static route, however if you’ve got a lot of complicated setup BGP is associate choice.
Navigate to Configuration -> Device Setup -> Routing -> Static Routes
Click Add
Interface: AZURE-VTI01 (as we have a tendency to created within the VTI Interface section)
Network: The Azure Virtual Network or virtual network entry is on, otherwise you might add a subnet from that network if you don’t need the total network.
Gateway IP: 169.254.225.2 (Our next hop is one up from the information processing we have a tendency to assail the VTP Interface) Click OK
Add extra routes to the other subnets
Click Apply
Or the CLI would be:
route AZURE-VTI01 ten.xx.xx.xx 255.255.0.0 169.254.225.2 1
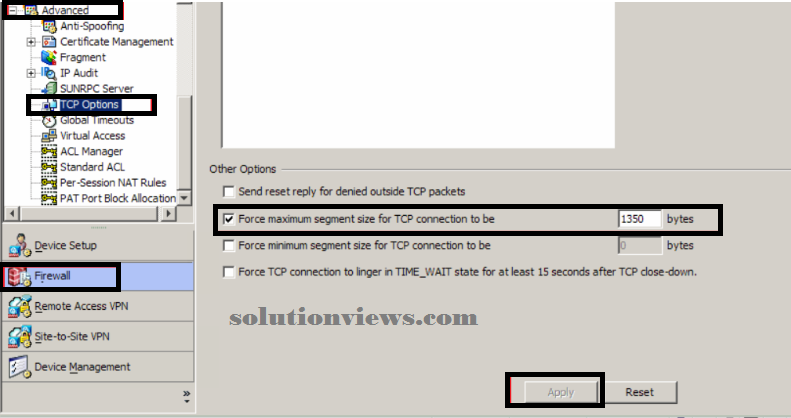
OTHER MICROSOFT advocate ASA TWEAKS:
Microsoft advocate setting the MSS to 1350 bytes, and enabling conserving vpn flows throughout tunnel rekeys
MSS:
Navigate to Configuration -> Firewall -> Advanced -> communications protocol choices
Under alternative choices tick “Force most section size for communications protocol affiliation to be” and set it to 1350
Or the CLI would be:
sysopt affiliation tcpmss 1350
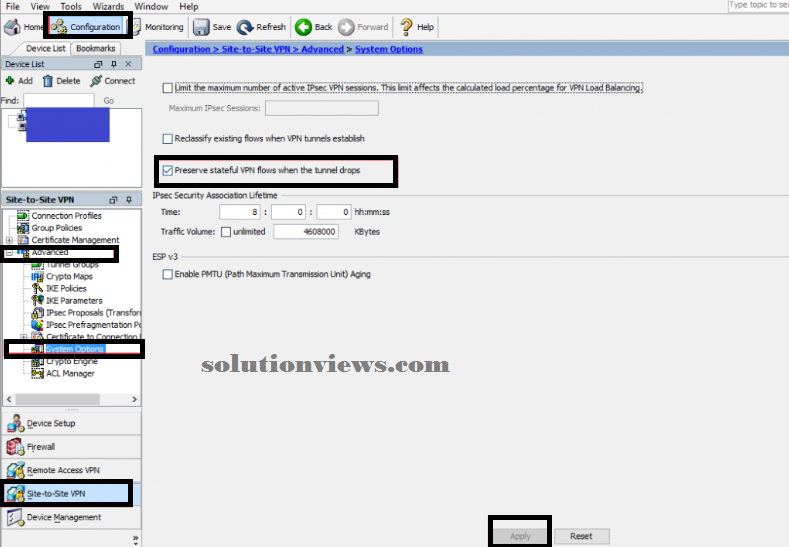
PRESERVING VPN FLOWS:
Navigate to Configuration -> Site-to-Site VPN Advanced -> System choices
Check “Preserve stateful VPN flows once the tunnel drops”
Click Apply
Click Save
Or
the CLI would be:
sysopt affiliation preserve-vpn-flows