Microsoft issued a security update in March 2018 to address a vulnerability in the Credential Security Support Provider Protocol (CredSSP). An attacker can remotely execute arbitrary code on a susceptible Windows host with an open RDP port (TCP/3389) using this vulnerability (CVE-2018–0886). The “2018-05 Security only/Monthly Rollup” update was released in May 2018. It prevents access to computers running an affected version of CredSSP.
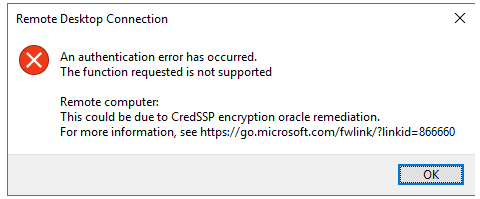
The Remote Desktop Connection error appears when you try to connect to a remote computer with a vulnerable CredSSP from Windows 10/Windows Server 2016.
An authentication error has occurred.
The function is not supported.
Remote Computer: hostname
This could be due to CredSSP encryption oracle remediation.For more information, see link.
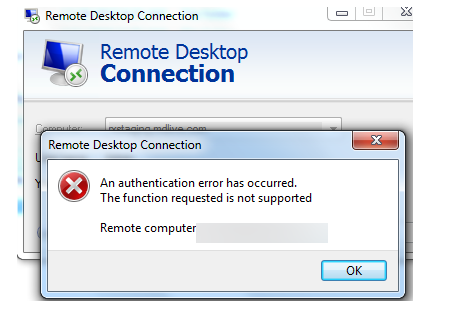
On Windows 7, the CredSSP error looks like this:
An authentication error has occurred.
The function requested is not supported.
Remote computer: hostnname
to repair This could be due to a credssp encryption oracle remediation problem, in which case you should upgrade the remote computer’s Windows security. You can update your Windows version with the most recent Cumulative Update. You can manually download the update from the Microsoft Update Catalog, or you can use Windows Update or WSUS to install it.
The CredSSP authentication error only appears when you try to connect via RDP from a computer that has the most recent security updates installed to a non-updated computer (for example, a computer that never gets updates or a clean installed device with a Windows 10/Windows Server 2016 build released before March 2018).
A workaround exists that allows you to connect to a computer running a vulnerable version of CredSSP. On the PC from which you are initiating the Remote Desktop connection, you must configure a specific Group Policy parameter entitled Encryption Oracle Remediation.
- Press Win+R, then type gpedit.msc into the Run box.
- In the Local Group Policy Editor, go to the following section: Computer
- System > Credentials Delegation > Configuration > Administrative Templates
- Open the Encryption Oracle Remediation policy setting;
- Change the status to Enabled and the Protection Level to Vulnerable;
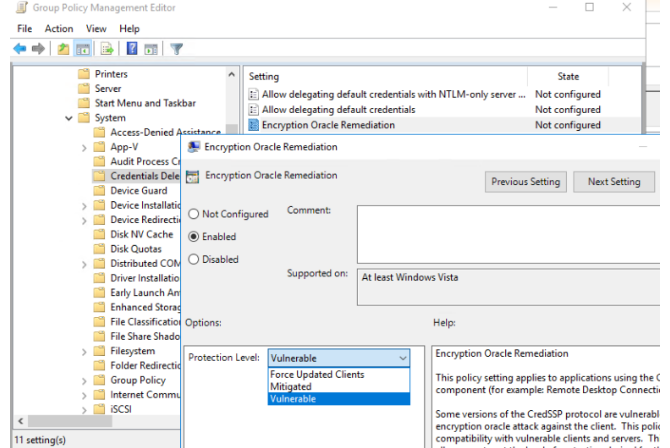
Use the following commands to make changes to the Group Policy settings:
gpupdate /forceYou can also use the registry to allow your computer to connect to vulnerable versions of CredSSP. Use the elevated command prompt to run the following command:
reg add HKLM\Software\Microsoft\Windows\CurrentVersion\Policies\System\CredSSP\Parameters /f /v AllowEncryptionOracle /t REG_DWORD /d 2You can now use RDP to connect to the remote host and install the updates. After upgrading, remember to disable the policy or restore the original value of the AllowEncryptionOracle registry value:
reg add HKLM\Software\Microsoft\Windows\CurrentVersion\Policies\System\CredSSP\Parameters /f /v AllowEncryptionOracle /t REG_DWORD /d 0There are 3 options in the “Encryption Oracle Remediation” policy:
- Vulnerable — the client can connect to vulnerable computers;
- Mitigated — the client cannot connect to vulnerable servers, but the servers can allow vulnerable clients to connect;
- Force Updated Clients — secure RDP CredSPP interoperability layer.
If you can’t connect to an updated RDP/RDS host with the “Force updated clients” option enabled from a machine that doesn’t have the CredSPP security update installed, you can allow the server to accept connections with an affected version of CredSPP. To do so, you must enable the policy on the server with the Mitigated value. To make modifications to the server, you can use PowerShell with admin credentials to connect to it remotely:
Enter-PSSession -ComputerName
Enter-PSSession -ComputerName RDSServer01 -Credential RDSServer01\administratorAllow the connection to be established:
Set-ItemProperty -Path 'HKLM:\Software\Microsoft\Windows\CurrentVersion\Policies\System\CredSSP\Parameters' -name "AllowEncryptionOracle" 2 -Type DWord